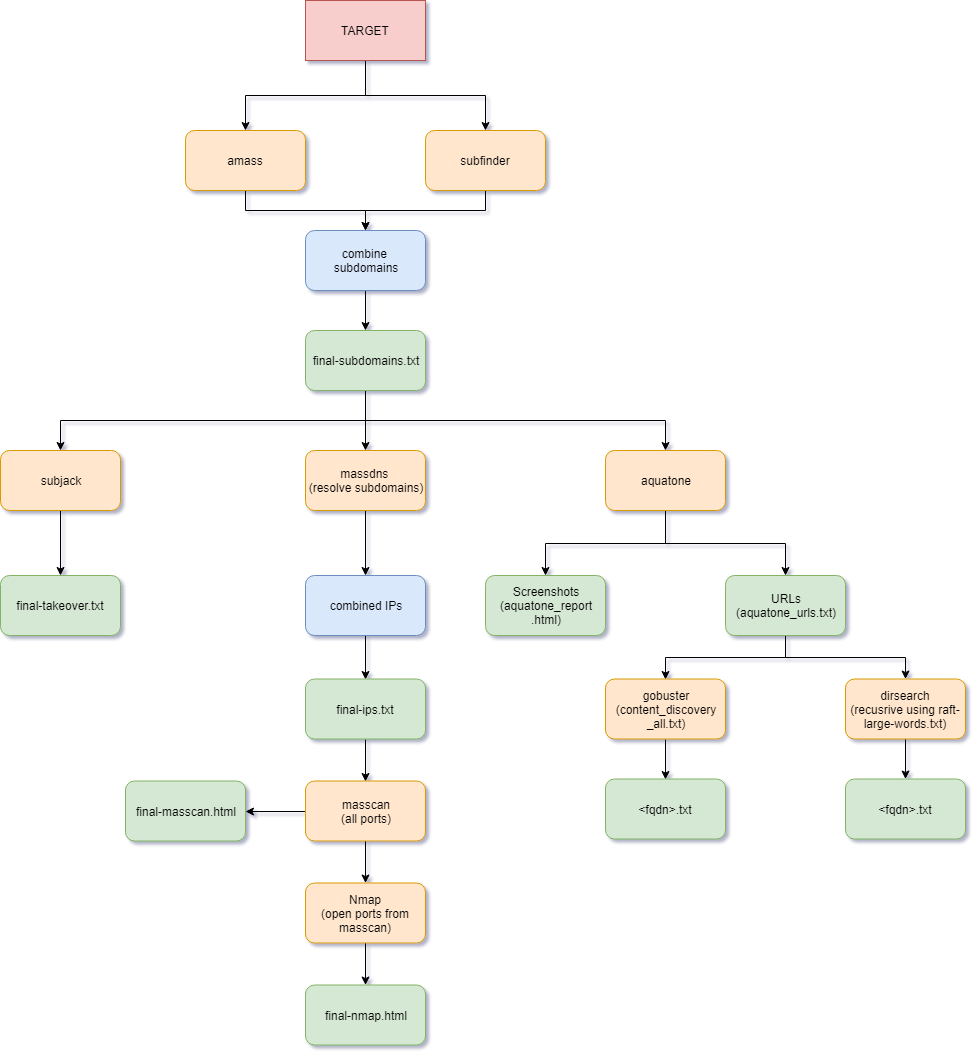
LazyRecon is a wrapper of various scripts that automates the tedious process of reconnaissance of a target domain.
LazyRecon utilizes the following tools:
- Subdomain Enumeration:
- Subdomain Takeover:
- IP Discovery:
- Port Scanner:
- Visual Recon:
- Content Discovery:
- Wordlists:
Thanks to the developers of these tools!
install.sh, modify the subEnumTools() function by placing your Virustotal, Passivetotal, SecurityTrails, Censys, Riddler, and Shodan API keys. This will give better results during the subdomain enumeration.
~/go/bin/subfinder --set-config VirustotalAPIKey=<INSERT-YOUR-API-KEY-HERE>
~/go/bin/subfinder --set-config PassivetotalUsername=<INSERT-YOUR-API-KEY-HERE>,PassivetotalKey=<INSERT-YOUR-API-KEY-HERE>
~/go/bin/subfinder --set-config SecurityTrailsKey=<INSERT-YOUR-API-KEY-HERE>
~/go/bin/subfinder --set-config RiddlerEmail=<INSERT-YOUR-API-KEY-HERE>,RiddlerPassword=<INSERT-YOUR-API-KEY-HERE>
~/go/bin/subfinder --set-config CensysUsername=<INSERT-YOUR-API-KEY-HERE>,CensysSecret=<INSERT-YOUR-API-KEY-HERE>
~/go/bin/subfinder --set-config ShodanAPIKey=<INSERT-YOUR-API-KEY-HERE>
To install, just do the following:
git clone https://github.com/capt-meelo/LazyRecon.git
cd LazyRecon
chmod +x install.sh
./install.sh
- It's recommended to run this tool in a VPS, such as DigitalOcean, for better speed.
- Running this tool takes time, thus it's suggested to run it under a screen or tmux session.
cd LazyRecon
chmod +x LazyRecon.sh
./LazyRecon.sh <target_domain>
If you have any problem or new idea, feel free to create an issue, or pull a request.
All of the tools being used by LazyRecon are developed by others. I just put all the pieces together to automate the redundant jobs.
This tool is written for educational purposes only. You are responsible for your own actions. If you mess something up or break any law while using this tool, it's your fault, and your fault only.