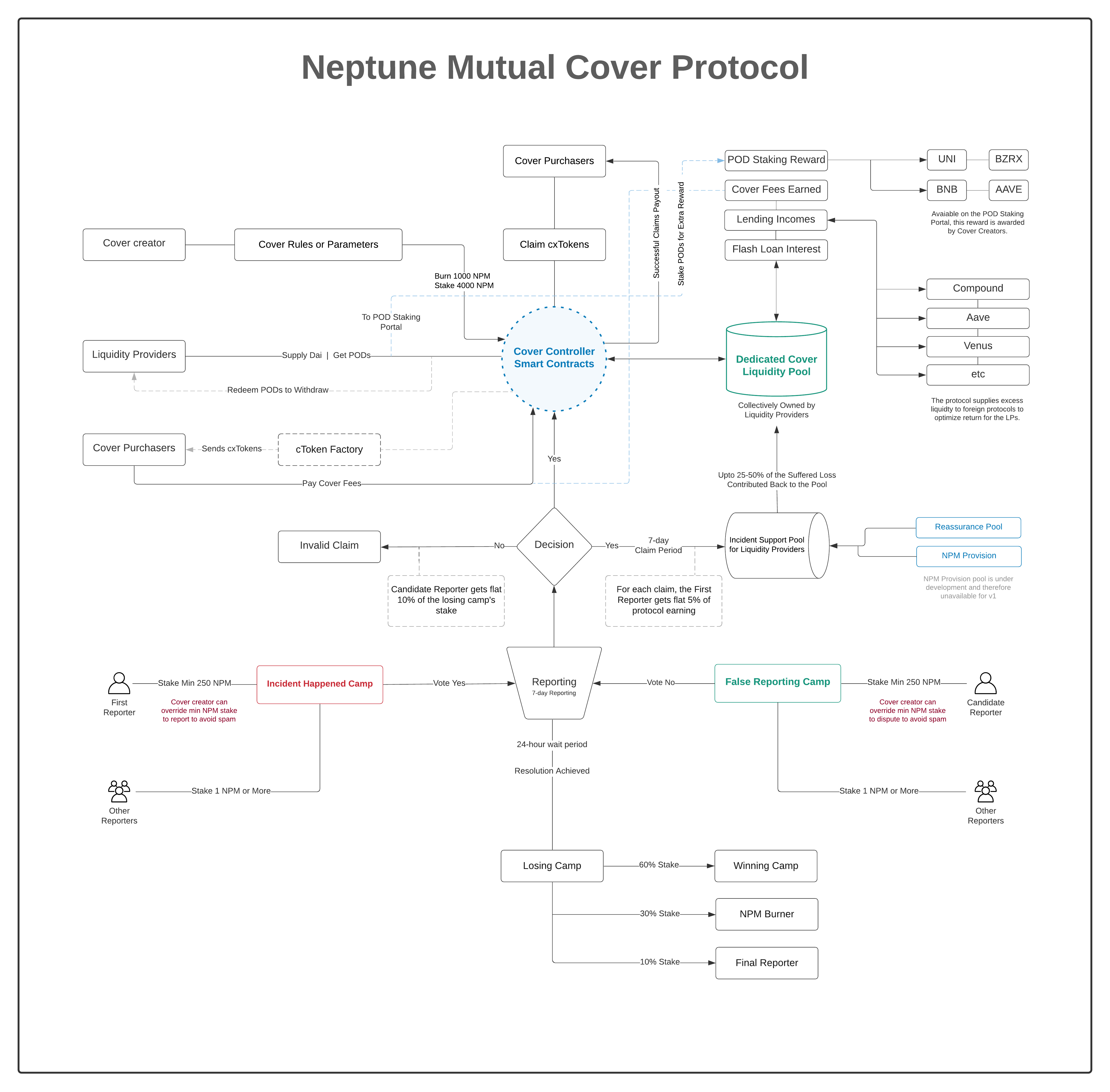
Anyone who has NPM tokens can create a cover contract. To avoid spam, questionable, and confusing cover contracts, a creator has to burn 1000 NPM tokens. Additionally, the contract creator also needs to stake 4000 NPM tokens or more. The higher the sake, the more visibility the contract gets if there are multiple cover contracts with the same name or similar terms.
[comment]: #solidoc Start
View Source: contracts/core/lifecycle/Cover.sol
↗ Extends: CoverBase
Cover
The cover contract facilitates you create and update covers
- constructor(IStore store)
- updateCover(bytes32 coverKey, bytes32 info)
- addCover(bytes32 coverKey, bytes32 info, address reassuranceToken, bool requiresWhitelist, uint256[] values)
- deployVault(bytes32 coverKey)
- stopCover(bytes32 coverKey, string reason)
- updateCoverCreatorWhitelist(address account, bool status)
- updateCoverUsersWhitelist(bytes32 coverKey, address[] accounts, bool[] statuses)
- checkIfWhitelistedCoverCreator(address account)
- checkIfWhitelistedUser(bytes32 coverKey, address account)
Constructs this contract
function (IStore store) public nonpayable CoverBase Arguments
| Name | Type | Description |
|---|---|---|
| store | IStore | Enter the store |
Source Code
constructor(IStore store) CoverBase(store) {}Updates the cover contract. This feature is accessible only to the cover owner or protocol owner (governance).
function updateCover(bytes32 coverKey, bytes32 info) external nonpayable nonReentrant Arguments
| Name | Type | Description |
|---|---|---|
| coverKey | bytes32 | Enter the cover key |
| info | bytes32 | Enter a new IPFS URL to update |
Source Code
function updateCover(bytes32 coverKey, bytes32 info) external override nonReentrant {
s.mustNotBePaused();
s.mustHaveNormalCoverStatus(coverKey);
s.senderMustBeCoverOwnerOrAdmin(coverKey);
require(s.getBytes32ByKeys(ProtoUtilV1.NS_COVER_INFO, coverKey) != info, "Duplicate content");
s.updateCoverInternal(coverKey, info);
emit CoverUpdated(coverKey, info);
}Adds a new coverage pool or cover contract.
To add a new cover, you need to pay cover creation fee
and stake minimum amount of NPM in the Vault.
Through the governance portal, projects will be able redeem
the full cover fee at a later date.
Apply for Fee Redemption
https://docs.neptunemutual.com/covers/cover-fee-redemption
As the cover creator, you will earn a portion of all cover fees
generated in this pool.
Read the documentation to learn more about the fees:
https://docs.neptunemutual.com/covers/contract-creators
function addCover(bytes32 coverKey, bytes32 info, address reassuranceToken, bool requiresWhitelist, uint256[] values) external nonpayable nonReentrant Arguments
| Name | Type | Description |
|---|---|---|
| coverKey | bytes32 | Enter a unique key for this cover |
| info | bytes32 | IPFS info of the cover contract |
| reassuranceToken | address | Optional. Token added as an reassurance of this cover. Reassurance tokens can be added by a project to demonstrate coverage support for their own project. This helps bring the cover fee down and enhances liquidity provider confidence. Along with the NPM tokens, the reassurance tokens are rewarded as a support to the liquidity providers when a cover incident occurs. |
| requiresWhitelist | bool | If set to true, this cover will only support whitelisted addresses. |
| values | uint256[] | [0] stakeWithFee Enter the total NPM amount (stake + fee) to transfer to this contract. |
Source Code
function addCover(
bytes32 coverKey,
bytes32 info,
address reassuranceToken,
bool requiresWhitelist,
uint256[] memory values
) external override nonReentrant {
// @suppress-acl Can only be called by a whitelisted address
// @suppress-acl Marking this as publicly accessible
// @suppress-address-trust-issue The reassuranceToken can only be the stablecoin supported by the protocol for this version.
s.mustNotBePaused();
s.senderMustBeWhitelistedCoverCreator();
require(values[0] >= s.getUintByKey(ProtoUtilV1.NS_COVER_CREATION_MIN_STAKE), "Your stake is too low");
require(reassuranceToken == s.getStablecoin(), "Invalid reassurance token");
s.addCoverInternal(coverKey, info, reassuranceToken, requiresWhitelist, values);
emit CoverCreated(coverKey, info, requiresWhitelist);
}function deployVault(bytes32 coverKey) external nonpayable nonReentrant
returns(address)Arguments
| Name | Type | Description |
|---|---|---|
| coverKey | bytes32 |
Source Code
function deployVault(bytes32 coverKey) external override nonReentrant returns (address) {
s.mustNotBePaused();
s.mustHaveStoppedCoverStatus(coverKey);
s.senderMustBeCoverOwnerOrAdmin(coverKey);
address vault = s.deployVaultInternal(coverKey);
emit VaultDeployed(coverKey, vault);
return vault;
}Enables governance admin to stop a spam cover contract
function stopCover(bytes32 coverKey, string reason) external nonpayable nonReentrant Arguments
| Name | Type | Description |
|---|---|---|
| coverKey | bytes32 | Enter the cover key you want to stop |
| reason | string | Provide a reason to stop this cover |
Source Code
function stopCover(bytes32 coverKey, string memory reason) external override nonReentrant {
s.mustNotBePaused();
s.mustHaveNormalCoverStatus(coverKey);
AccessControlLibV1.mustBeGovernanceAdmin(s);
s.stopCoverInternal(coverKey);
emit CoverStopped(coverKey, msg.sender, reason);
}Adds or removes an account to the cover creator whitelist.
For the first version of the protocol, a cover creator has to be whitelisted
before they can call the addCover function.
function updateCoverCreatorWhitelist(address account, bool status) external nonpayable nonReentrant Arguments
| Name | Type | Description |
|---|---|---|
| account | address | Enter the address of the cover creator |
| status | bool | Set this to true if you want to add to or false to remove from the whitelist |
Source Code
function updateCoverCreatorWhitelist(address account, bool status) external override nonReentrant {
s.mustNotBePaused();
AccessControlLibV1.mustBeGovernanceAgent(s);
s.updateCoverCreatorWhitelistInternal(account, status);
emit CoverCreatorWhitelistUpdated(account, status);
}function updateCoverUsersWhitelist(bytes32 coverKey, address[] accounts, bool[] statuses) external nonpayable nonReentrant Arguments
| Name | Type | Description |
|---|---|---|
| coverKey | bytes32 | |
| accounts | address[] | |
| statuses | bool[] |
Source Code
function updateCoverUsersWhitelist(
bytes32 coverKey,
address[] memory accounts,
bool[] memory statuses
) external override nonReentrant {
s.mustNotBePaused();
s.senderMustBeCoverOwnerOrAdmin(coverKey);
s.updateCoverUsersWhitelistInternal(coverKey, accounts, statuses);
}Signifies if a given account is a whitelisted cover creator
function checkIfWhitelistedCoverCreator(address account) external view
returns(bool)Arguments
| Name | Type | Description |
|---|---|---|
| account | address |
Source Code
function checkIfWhitelistedCoverCreator(address account) external view override returns (bool) {
return s.getAddressBooleanByKey(ProtoUtilV1.NS_COVER_CREATOR_WHITELIST, account);
}Signifies if a given account is a whitelisted user
function checkIfWhitelistedUser(bytes32 coverKey, address account) external view
returns(bool)Arguments
| Name | Type | Description |
|---|---|---|
| coverKey | bytes32 | |
| account | address |
Source Code
function checkIfWhitelistedUser(bytes32 coverKey, address account) external view override returns (bool) {
return s.getAddressBooleanByKeys(ProtoUtilV1.NS_COVER_USER_WHITELIST, coverKey, account);
}- AaveStrategy
- AccessControl
- AccessControlLibV1
- Address
- BaseLibV1
- BokkyPooBahsDateTimeLibrary
- BondPool
- BondPoolBase
- BondPoolLibV1
- CompoundStrategy
- console
- Context
- Cover
- CoverBase
- CoverLibV1
- CoverReassurance
- CoverStake
- CoverUtilV1
- cxToken
- cxTokenFactory
- cxTokenFactoryLibV1
- Delayable
- Destroyable
- ERC165
- ERC20
- FakeAaveLendingPool
- FakeCompoundDaiDelegator
- FakeRecoverable
- FakeStore
- FakeToken
- FakeUniswapPair
- FakeUniswapV2FactoryLike
- FakeUniswapV2PairLike
- FakeUniswapV2RouterLike
- FaultyAaveLendingPool
- FaultyCompoundDaiDelegator
- Finalization
- ForceEther
- Governance
- GovernanceUtilV1
- IAaveV2LendingPoolLike
- IAccessControl
- IBondPool
- IClaimsProcessor
- ICompoundERC20DelegatorLike
- ICover
- ICoverReassurance
- ICoverStake
- ICxToken
- ICxTokenFactory
- IERC165
- IERC20
- IERC20Detailed
- IERC20Metadata
- IERC3156FlashBorrower
- IERC3156FlashLender
- IFinalization
- IGovernance
- ILendingStrategy
- ILiquidityEngine
- IMember
- InvalidStrategy
- IPausable
- IPolicy
- IPolicyAdmin
- IPriceDiscovery
- IProtocol
- IRecoverable
- IReporter
- IResolution
- IResolvable
- IStakingPools
- IStore
- IStoreLike
- IUniswapV2FactoryLike
- IUniswapV2PairLike
- IUniswapV2RouterLike
- IUnstakable
- IVault
- IVaultDelegate
- IVaultFactory
- IWitness
- LiquidityEngine
- MaliciousToken
- MockAccessControlUser
- MockCoverUtilUser
- MockCxToken
- MockCxTokenPolicy
- MockCxTokenStore
- MockFlashBorrower
- MockProcessorStore
- MockProcessorStoreLib
- MockProtocol
- MockRegistryClient
- MockStore
- MockStoreKeyUtilUser
- MockValidationLibUser
- MockVault
- MockVaultLibUser
- NPM
- NPMDistributor
- NTransferUtilV2
- NTransferUtilV2Intermediate
- Ownable
- Pausable
- Policy
- PolicyAdmin
- PolicyHelperV1
- PoorMansERC20
- PriceDiscovery
- PriceLibV1
- Processor
- ProtoBase
- Protocol
- ProtoUtilV1
- Recoverable
- ReentrancyGuard
- RegistryLibV1
- Reporter
- Resolution
- Resolvable
- RoutineInvokerLibV1
- SafeERC20
- StakingPoolBase
- StakingPoolCoreLibV1
- StakingPoolInfo
- StakingPoolLibV1
- StakingPoolReward
- StakingPools
- Store
- StoreBase
- StoreKeyUtil
- StrategyLibV1
- Strings
- TimelockController
- Unstakable
- ValidationLibV1
- Vault
- VaultBase
- VaultDelegate
- VaultDelegateBase
- VaultDelegateWithFlashLoan
- VaultFactory
- VaultFactoryLibV1
- VaultLibV1
- VaultLiquidity
- VaultStrategy
- WithFlashLoan
- WithPausability
- WithRecovery
- Witness
[comment]: #solidoc End