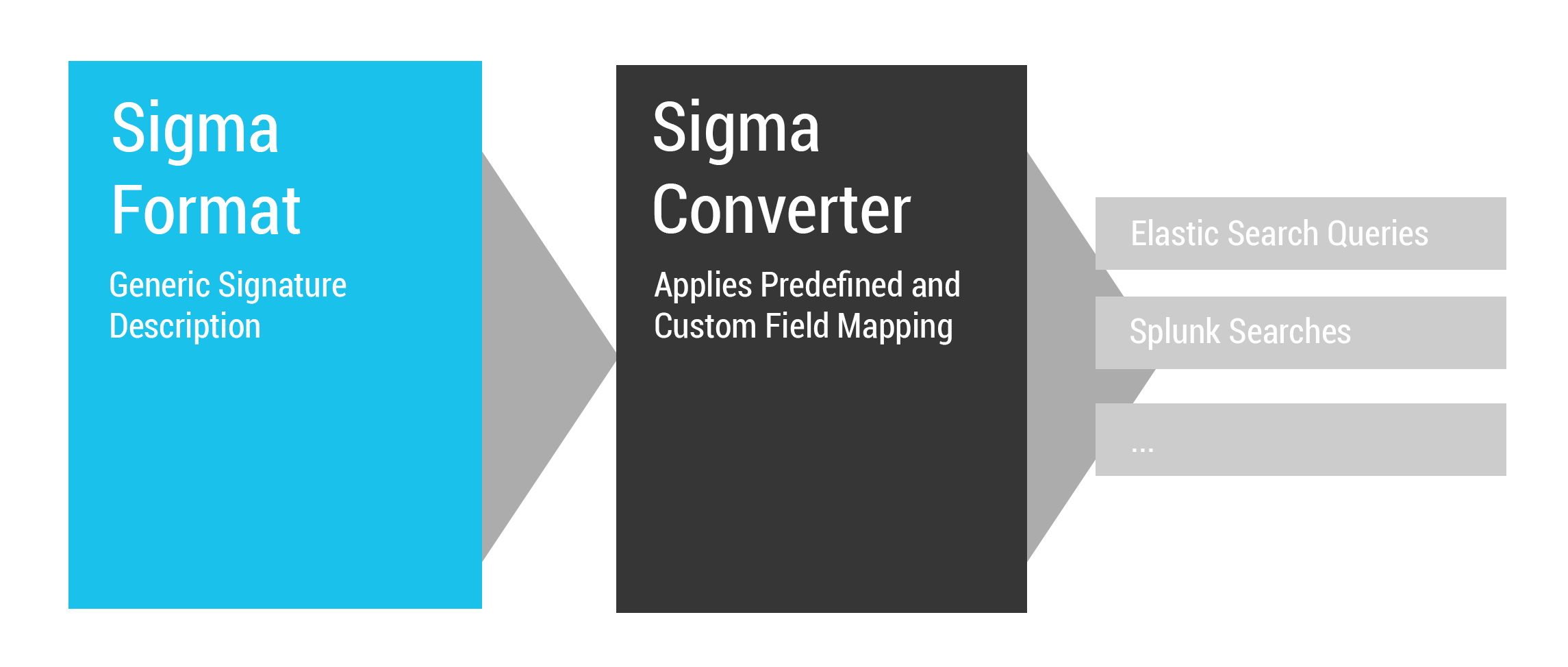
Generic Signature Format for SIEM Systems
Sigma is a generic and open signature format that allows you to describe relevant log events in a straight forward manner. The rule format is very flexible, easy to write and applicable to any type of log file. The main purpose of this project is to provide a structured form in which researchers or analysts can describe their once developed detection methods and make them shareable with others.
Sigma is for log files what Snort is for network traffic and YARA is for files.
This repository contains:
- Sigma rule specification in the Wiki
- Open repository for sigma signatures in the
./rulessubfolder - A converter that generate searches/queries for different SIEM systems [work in progress]
The SANS webcast on Sigma contains a very good 20 min introduction to the project by John Hubbart from minute 39 onward. (SANS account required; registration is free)
MITRE ATT&CK and Sigma Alerting Webcast Recording
- Describe your detection method in Sigma to make it sharable
- Write and your SIEM searches in Sigma to avoid a vendor lock-in
- Share the signature in the appendix of your analysis along with IOCs and YARA rules
- Share the signature in threat intel communities - e.g. via MISP
- Provide Sigma signatures for malicious behaviour in your own application
Today, everyone collects log data for analysis. People start working on their own, processing numerous white papers, blog posts and log analysis guidelines, extracting the necessary information and build their own searches and dashboard. Some of their searches and correlations are great and very useful but they lack a standardized format in which they can share their work with others.
Others provide excellent analyses, include IOCs and YARA rules to detect the malicious files and network connections, but have no way to describe a specific or generic detection method in log events. Sigma is meant to be an open standard in which such detection mechanisms can be defined, shared and collected in order to improve the detection capabilities for everyone.
See the first slide deck that I prepared for a private conference in mid January 2017.
Sigma - Make Security Monitoring Great Again
The specifications can be found in the Wiki.
The current specification is a proposal. Feedback is requested.
Florian wrote a short rule creation tutorial that can help you getting started.
- Download or clone the respository
- Check the
./rulessub directory for an overview on the rule base - Run
python sigmac --helpin folder./toolsto get a help on the rule converter - Convert a rule of your choice with
sigmaclike./sigmac -t splunk -c tools/config/generic/sysmon.yml ./rules/windows/process_creation/win_susp_whoami.yml - Convert a whole rule directory with
python sigmac -t splunk -r ../rules/proxy/ - Check the
./tools/configfolder and the wiki if you need custom field or log source mappings in your environment
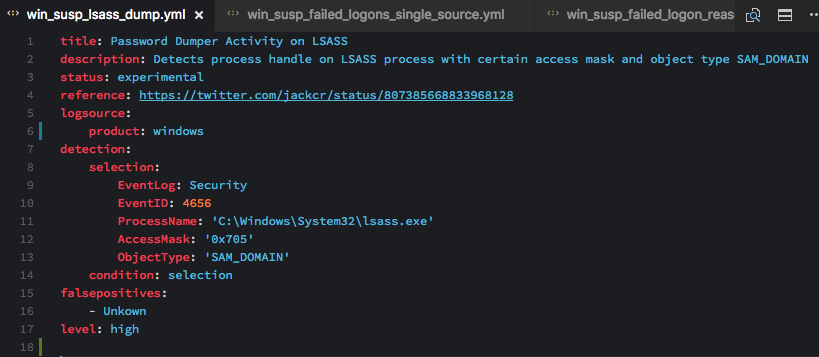
Windows 'Security' Eventlog: Access to LSASS Process with Certain Access Mask / Object Type (experimental)
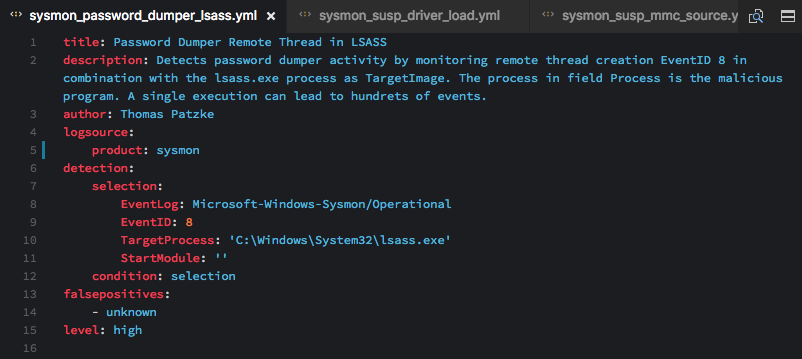
Sysmon: Remote Thread Creation in LSASS Process
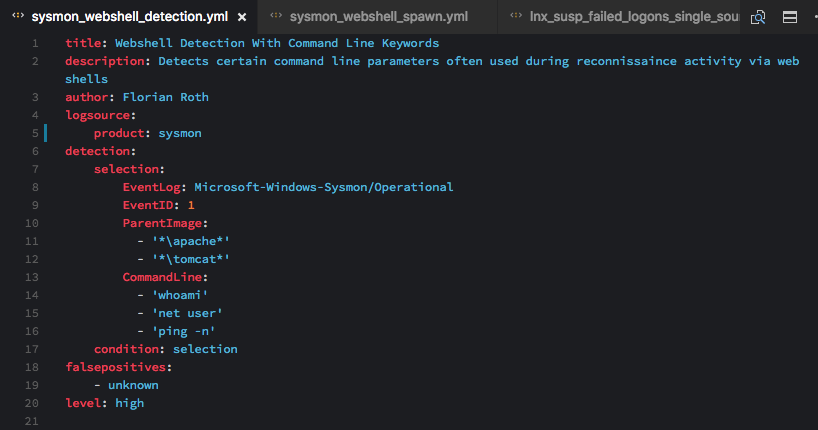
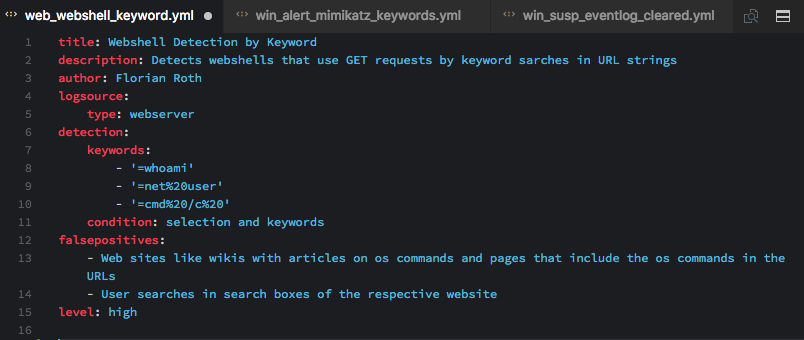
Web Server Access Logs: Web Shell Detection
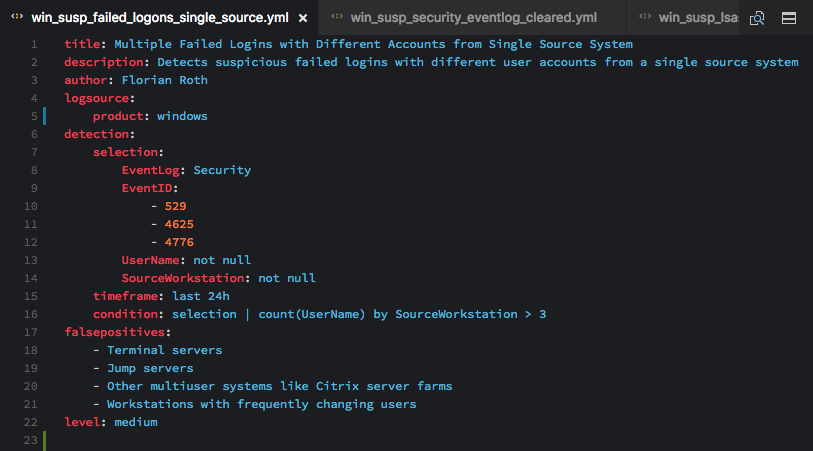
Windows 'Security' Eventlog: Suspicious Number of Failed Logons from a Single Source Workstation
Sigmac converts sigma rules into queries or inputs of the supported targets listed below. It acts as a frontend to the
Sigma library that may be used to integrate Sigma support in other projects. Further, there's merge_sigma.py which
merges multiple YAML documents of a Sigma rule collection into simple Sigma rules.
usage: sigmac [-h] [--recurse] [--filter FILTER]
[--target {arcsight,es-qs,es-dsl,kibana,xpack-watcher,elastalert,graylog,logpoint,grep,netwitness,powershell,qradar,qualys,splunk,splunkxml,sumologic,fieldlist,wdatp}]
[--target-list] [--config CONFIG] [--output OUTPUT]
[--backend-option BACKEND_OPTION] [--defer-abort]
[--ignore-backend-errors] [--verbose] [--debug]
[inputs [inputs ...]]
Convert Sigma rules into SIEM signatures.
positional arguments:
inputs Sigma input files ('-' for stdin)
optional arguments:
-h, --help show this help message and exit
--recurse, -r Use directory as input (recurse into subdirectories is
not implemented yet)
--filter FILTER, -f FILTER
Define comma-separated filters that must match (AND-
linked) to rule to be processed. Valid filters:
level<=x, level>=x, level=x, status=y, logsource=z,
tag=t. x is one of: low, medium, high, critical. y is
one of: experimental, testing, stable. z is a word
appearing in an arbitrary log source attribute. t is a
tag that must appear in the rules tag list, case-
insensitive matching. Multiple log source
specifications are AND linked.
--target {arcsight,es-qs,es-dsl,kibana,xpack-watcher,elastalert,graylog,logpoint,grep,netwitness,powershell,qradar,qualys,splunk,splunkxml,sumologic,fieldlist,wdatp}, -t {arcsight,es-qs,es-dsl,kibana,xpack-watcher,elastalert,graylog,logpoint,grep,netwitness,powershell,qradar,qualys,splunk,splunkxml,sumologic,fieldlist,wdatp}
Output target format
--target-list, -l List available output target formats
--config CONFIG, -c CONFIG
Configurations with field name and index mapping for
target environment. Multiple configurations are merged
into one. Last config is authorative in case of
conflicts.
--output OUTPUT, -o OUTPUT
Output file or filename prefix if multiple files are
generated
--backend-option BACKEND_OPTION, -O BACKEND_OPTION
Options and switches that are passed to the backend
--defer-abort, -d Don't abort on parse or conversion errors, proceed
with next rule. The exit code from the last error is
returned
--ignore-backend-errors, -I
Only return error codes for parse errors and ignore
errors for rules that cause backend errors. Useful,
when you want to get as much queries as possible.
--verbose, -v Be verbose
--debug, -D Debugging output
Translate a single rule
tools/sigmac -t splunk rules/windows/sysmon/sysmon_susp_image_load.yml
Translate a whole rule directory and ignore backend errors (-I) in rule conversion for the selected backend (-t splunk)
tools/sigmac -I -t splunk -r rules/windows/sysmon/
Apply your own config file (-c ~/my-elk-winlogbeat.yml) during conversion, which can contain you custom field and source mappings
tools/sigmac -t es-qs -c ~/my-elk-winlogbeat.yml -r rules/windows/sysmon
Use a config file for process_creation rules (-r rules/windows/process_creation) that instructs sigmac to create queries for a Sysmon log source (-c tools/config/generic/sysmon.yml) and the ElasticSearch target backend (-t es-qs)
tools/sigmac -t es-qs -c tools/config/generic/sysmon.yml -r rules/windows/process_creation
Use a config file for a single process_creation rule (./rules/windows/process_creation/win_susp_outlook.yml) that instructs sigmac to create queries for process creation events generated in the Windows Security Eventlog (-c tools/config/generic/windows-audit.yml) and a Splunk target backend (-t splunk)
tools/sigmac -t splunk -c ~/my-splunk-mapping.yml -c tools/config/generic/windows-audit.yml ./rules/windows/process_creation/win_susp_outlook.yml
(See @blubbfiction's blog post for more information)
- Splunk (plainqueries and dashboards)
- ElasticSearch Query Strings
- ElasticSearch Query DSL
- Kibana
- Elastic X-Pack Watcher
- Logpoint
- Windows Defender Advanced Threat Protection (WDATP)
- Azure Sentinel / Azure Log Analytics
- ArcSight
- QRadar
- Qualys
- RSA NetWitness
- PowerShell
- Grep with Perl-compatible regular expression support
Current work-in-progress
New targets are continuously developed. You can get a list of supported targets with sigmac --target-list or sigmac -l.
The usage of Sigmac (the Sigma Rule Converter) or the underlying library requires Python >= 3.5 and PyYAML.
It's available on PyPI. Install with:
pip3 install sigmatoolsAlternatively, if used from the Sigma Github repository, the Python dependencies can be installed with:
pip3 install -r tools/requirements.txtFor development (e.g. execution of integration tests with make and packaging), further dependencies are required and can be installed with:
pip3 install -r tools/requirements-devel.txtImport Sigma rules to MISP events. Depends on PyMISP.
Parameters that aren't changed frequently (--url, --key) can be put without the prefixing dashes -- into a file
and included with @filename as parameter on the command line.
Example: misp.conf:
url https://host
key foobarfoobarfoobarfoobarfoobarfoobarfoo
Load Sigma rule into MISP event 1234:
sigma2misp @misp.conf --event 1234 sigma_rule.py
Load Sigma rules in directory sigma_rules/ into one newly created MISP event with info set to Test Event:
sigma2misp @misp.conf --same-event --info "Test Event" -r sigma_rules/
Evt2Sigma helps you with the rule creation. It generates a Sigma rule from a log entry.
The directory contrib contains scripts that were contributed by the community:
sigma2elastalert.pyi by David Routin: A script that converts Sigma rules to Elastalert configurations. This tool uses sigmac and expects it in its path.
These tools are not part of the main toolchain and maintained separately by their authors.
- Integration of MITRE ATT&CK framework identifier to the rule set
- Integration into Threat Intel Exchanges
- Attempts to convince others to use the rule format in their reports, threat feeds, blog posts, threat sharing platforms
- MISP (since version 2.4.70, March 2017)
- TA-Sigma-Searches (Splunk App)
- SOC Prime - Sigma Rule Editor
- ypsilon - Automated Use Case Testing
- uncoder.io - Online Translator for SIEM Searches
- SPARK - Scan with Sigma rules on endpoints
- RANK VASA
The content of this repository is released under the following licenses:
- The toolchain (everything under
tools/) is licensed under the GNU Lesser General Public License. - The Sigma specification is public domain.
- Everything else, especially the rules contained in the
rules/directory is released under the GNU General Public License.
This is a private project mainly developed by Florian Roth and Thomas Patzke with feedback from many fellow analysts and friends. Rules are our own or have been drived from blog posts, tweets or other public sources that are referenced in the rules.