This document is the canonical source of truth for things like supported toolchain versions for building Kubernetes.
Please submit an issue on github if you
- find a requirement that this doc does not capture,
- find other docs with references to requirements that are not simply links to this doc.
This document is intended to be relative to the branch in which it is found.
Development branch requirements will change over time, but release branch requirements are frozen.
Make sure you decide whether your issue and/or pull request is improving kubernetes architecture or whether its simply fixing a bug.
Make sure there are no typos, if you need a diagram, add it. Make sure you SEPARATE the description of the problem (i.e. Y is a critical component that is too slow for an SLA that we care about) from the solution (i.e. make X faster).
Some of these checks were less common in Kubernetes earlier days, but now having over 1000 contributors, each issue should be filed with care, and should be sanity-checkable in under 5 minutes (even the busiest of reviewers can spare up to 5 minutes to review a patch that is thoughtfully justified).
These patches can be easy to review since test coverage is submitted with the patch. Bug fixes don't usually require alot of extra testing: But please update the unit tests so that they catch the bug !
Some examples of "Architecture" improvements:
- Adding a new feature or making a feature more configurable/modular.
- Converting structs to interfaces.
- Improving test coverage.
- Decoupling logic or creation of new utilities.
- Making code more resilient (sleeps, backoffs, reducing flakiness, etc).
These sorts of improvements are easily evaluated if they decrease lines of code without breaking functionality.
If you are improving the quality of code, then justify/state exactly what you 'cleaning up' in your Pull Request so as not to waste reviewer time.
If you're making code more resilient, test it with a local cluster to demonstrate how exactly your patch changes things.
Example: If you made a controller more robust to inconsistent data, make a mock object which returns incorrect data a few times and verify the controllers behaviour accordingly.
If you are submitting a performance bug, you MUST ALSO submit data that demonstrates your problem if you want the issue to remain open. This can be done locally using kubemark, scheduler_perf, unit tests, go benchmark tests, or e2e tests on a real cluster with metrics plots.
Examples of how NOT to suggest a performance bug (these can really lead to a long review process and waste cycles):
- We should be doing X instead of Y because it might lead to better performance.
- Doing X instead of Y would reduce calls to Z.
The above statements have basically no value to a reviewer, because neither is a strong, testable, assertive statement. This will land your PR in a no-man's-land zone (at best), or waste tons of time for a busy reviewer (at worst).
Of course any improvement is welcome, but performance improvements are the hardest to review. They often make code more complex, and to-often are not easily evaluated at review time due to lack of sufficient data submitted by the author of a performance improvement patch.
Some examples of "Performance" improvements:
- Improving a caching implementation.
- Reducing calls to functions which are O(n^2), or reducing dependence on API server requests.
- Changing the value of default parameters for proceeses, or making those values 'smarter'.
- Parallelizing a calculation that needs to run on a large set of node/pod objects.
These issues should always be submitted with (in decreasing order or value):
- A golang Benchmark test.
- A visual depiction of reduced metric load on a cluster (measurable using metrics/ endpoints and grafana).
- A hand-instrumented timing test (i.e. adding some logs into the controller manager).
Without submitting data and results for your suggested performance improvements, its very possible that bikeshedding about meaningless possible performance optimizations could waste both reviewer time as well as your own.
Some examples of properly submitted performance issues, from different parts of the codebase. They all have one thing in common: Lots of data in the issue definition. If you are new to kubernetes and thinking about filing a performance optimization, re-read one or all of these before you get started.
- kubernetes/kubernetes#18266 (apiserver)
- kubernetes/kubernetes#32833 (node)
- kubernetes/kubernetes#31795 (scheduler)
Since performance improvements deal with empirical systems, one playing in this space should be intimately familiar with the "scientific method" of creating a hypothesis, collecting data, and then revising your hypothesis. The above issues tend to do this transparently, using figures and data rather then theoretical postulations, as a first pass before a single line of code is reviewed.
Official releases are built using Docker containers. To build Kubernetes using Docker please follow these instructions.
Kubernetes development helper scripts assume an up-to-date GNU tools environment. Most recent Linux distros should work out-of-the-box.
Mac OS X ships with outdated BSD-based tools. We recommend installing Os X GNU tools.
Kubernetes maintains state in etcd, a distributed key store.
Please install it locally to run local integration tests.
Kubernetes is written in Go. If you don't have a Go development environment, please set one up.
| Kubernetes | requires Go |
|---|---|
| 1.0 - 1.2 | 1.4.2 |
| 1.3, 1.4 | 1.6 |
| 1.5 and higher | 1.7 - 1.7.5 |
| 1.8 not verified as of Feb 2017 |
After installation, you'll need GOPATH defined,
and PATH modified to access your Go binaries.
A common setup is
export GOPATH=$HOME/go
export PATH=$PATH:$GOPATH/binUpgrading Go requires specific modification of some scripts and container images.
- The image for cross compiling in build/build-image/cross.
The
VERSIONfile andDockerfile. - Update dockerized-e2e-runner.sh to run a kubekins-e2e with the desired Go version.
This requires pushing the e2e and test images that are
FROMthe desired Go version. - The cross tag
KUBE_BUILD_IMAGE_CROSS_TAGin build/common.sh.
Kubernetes build/test scripts use godep to
manage dependencies.
go get -u github.com/tools/godepCheck your version; v63 or higher is known to work for Kubernetes.
godep versionDevelopers planning to manage dependencies in the vendor/ tree may want to
explore alternative environment setups. See using godep to manage dependencies.
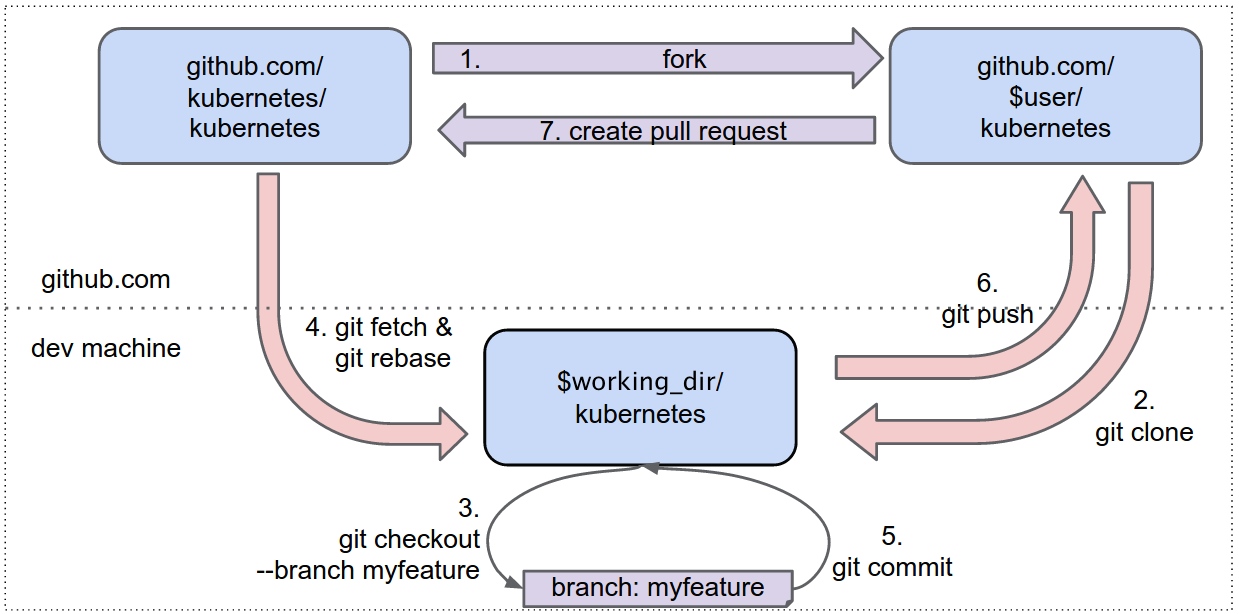
- Visit https://github.com/kubernetes/kubernetes
- Click
Forkbutton (top right) to establish a cloud-based fork.
Per Go's workspace instructions, place Kubernetes' code on your
GOPATH using the following cloning procedure.
Define a local working directory:
# If your GOPATH has multiple paths, pick
# just one and use it instead of $GOPATH here
working_dir=$GOPATH/src/k8s.ioIf you already do Go development on github, the
k8s.iodirectory will be a sibling to your existinggithub.comdirectory.
Set user to match your github profile name:
user={your github profile name}Both $working_dir and $user are mentioned in the figure above.
Create your clone:
mkdir -p $working_dir
cd $working_dir
git clone https://github.com/$user/kubernetes.git
# or: git clone [email protected]:$user/kubernetes.git
cd $working_dir/kubernetes
git remote add upstream https://github.com/kubernetes/kubernetes.git
# or: git remote add upstream [email protected]:kubernetes/kubernetes.git
# Never push to upstream master
git remote set-url --push upstream no_push
# Confirm that your remotes make sense:
git remote -vPlease link the Kubernetes pre-commit hook into your .git directory.
This hook checks your commits for formatting, building, doc generation, etc.
It requires both godep and etcd on your PATH.
cd $working_dir/kubernetes/.git/hooks
ln -s ../../hooks/pre-commit .Get your local master up to date:
cd $working_dir/kubernetes
git fetch upstream
git checkout master
git rebase upstream/masterBranch from it:
git checkout -b myfeatureThen edit code on the myfeature branch.
cd $working_dir/kubernetes
makeTo build with optimizations disabled for enabling use of source debug tools:
make GOGCFLAGS="-N -l"To build binaries for all platforms:
make crosscd $working_dir/kubernetes
# Run every unit test
make test
# Run package tests verbosely
make test WHAT=pkg/util/cache GOFLAGS=-v
# Run integration tests, requires etcd
make test-integration
# Run e2e tests
make test-e2eSee the testing guide and end-to-end tests for additional information and scenarios.
# While on your myfeature branch
git fetch upstream
git rebase upstream/masterCommit your changes.
git commitLikely you go back and edit/build/test some more then commit --amend
in a few cycles.
When ready to review (or just to establish an offsite backup or your work),
push your branch to your fork on github.com:
git push -f origin myfeature- Visit your fork at https://github.com/$user/kubernetes (replace
$userobviously). - Click the
Compare & pull requestbutton next to yourmyfeaturebranch. - Check out the pull request process for more details.
If you have upstream write access, please refrain from using the GitHub UI for creating PRs, because GitHub will create the PR branch inside the main repository rather than inside your fork.
Once your pull request has been opened it will be assigned to one or more reviewers. Those reviewers will do a thorough code review, looking for correctness, bugs, opportunities for improvement, documentation and comments, and style.
Commit changes made in response to review comments to the same branch on your fork.
Very small PRs are easy to review. Very large PRs are very difficult to review.
At the assigned reviewer's discretion, a PR may be switched to use Reviewable instead. Once a PR is switched to Reviewable, please ONLY send or reply to comments through reviewable. Mixing code review tools can be very confusing.
See Faster Reviews for some thoughts on how to streamline the review process.
Upon merge (by either you or your reviewer), all commits left on the review branch should represent meaningful milestones or units of work. Use commits to add clarity to the development and review process.
Before merging a PR, squash any fix review feedback, typo, and rebased sorts of commits.
It is not imperative that every commit in a PR compile and pass tests independently, but it is worth striving for.
For mass automated fixups (e.g. automated doc formatting), use one or more commits for the changes to tooling and a final commit to apply the fixup en masse. This makes reviews easier.