Important: You can only use this skill for glibcs < 2.39.
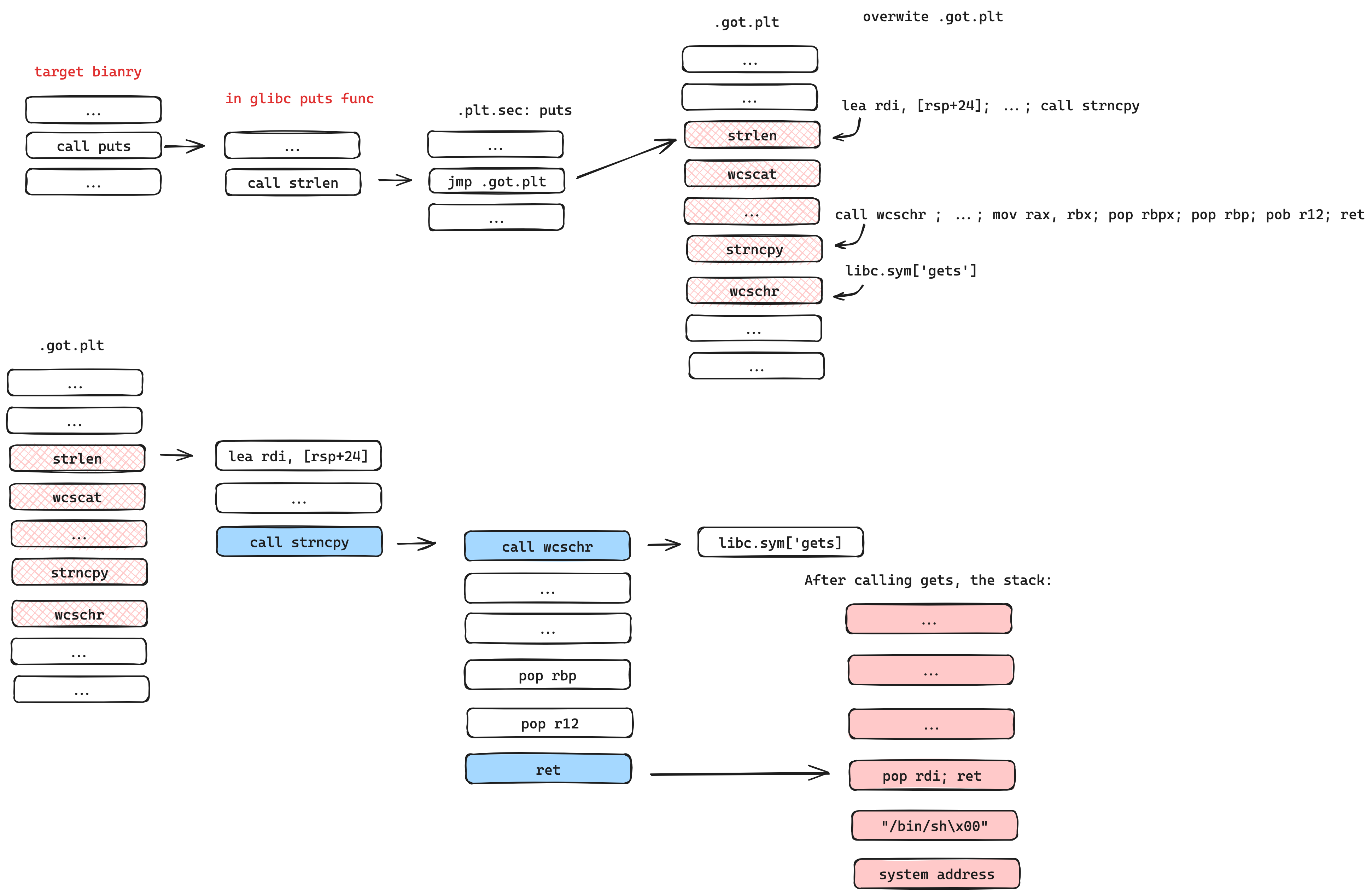
Transform arbitrary write to RCE.
This is a userspace attacking skill: If you can write arbitrary memory space, you can use this method to execute arbitrary code.
You only need to know the base address of Glibc Glibc is FULL RELRO by default for glibc2.39. A great security improvement! We can't hijack Libc GOT on libc version >= 2.39
While exploiting a CTF challenge, I found libstdc++ is a juicy target of this technique. It's still usable on the latest LTS-ubuntu(24.04).
[14:26:12] n132 :: xps ➜ ~/Downloads/FL_Support_Center » pwn checksec /lib/x86_64-linux-gnu/libstdc++.so.6
[*] '/lib/x86_64-linux-gnu/libstdc++.so.6'
Arch: amd64-64-little
RELRO: Partial RELRO
Stack: Canary found
NX: NX enabled
PIE: PIE enabled
FORTIFY: EnabledI'll provide a demo later. A simple way to get a shell is just to modify del/new got to system and cin the string /bin/sh (Kylebot told me people already found it even though they didn't show that publicly I just re-find this technique). But if ROP is what we want, aha, we can do libc-got-hijacking (even though it's unnecessary, it's a general solution!)
Compared to glibc<=2.35 there is mitigation implemented, which forbids the methods for the old library. However, we designed a method to bypass it and execute arbitrary code by once arbitrary write on Glibc's GOT table. This method performs Return Oriented Programming (ROP) attack on the Global Offset Table (GOT).
You can find details, templates, demos, and everything you want in: Details and Templates
I learned the original method from Sammy Hajhamid also the methods for glibc <=2.35 are inspired by his work.
Based on his work, We designed a method to execute arbitrary code by once arbitrary write on Glibc's GOT table. The method uses PLT_0 to push libc_exe_address to the stack and then use POP RSP, RET to execute our ROPchain.
You can find details, templates, demos, and everything you want in: Details and Templates
-
Great job @swing on the impressive work with glibc >2.35!
-
Appreciate the original work done by @pepsipu.