This repo is a collection of demos of the Dapr building blocks. Each demo provides a local and cloud based configuration to demonstrate the ability to run on multiple platforms. They are self contained and automatically provision the required infrastructure using the provided Bicep files.
| Demo | Building Blocks | Local | Cloud | Language |
|---|---|---|---|---|
| Binding | Bindings | File Share | Azure Storage | HTTP |
| Observability | Observability | Zipkin | Azure Application Insights | C#, HTTP |
| PubSub | Publish & Subscribe Publish & Subscribe State management |
Redis Redis Redis |
Azure Service Bus Azure Event Hubs Azure SQL Server |
C#, HTTP |
| Secrets | Secrets management | Local | Azure Key Vault | HTTP |
| StateStore | State management | Redis | Azure Cosmos DB | HTTP |
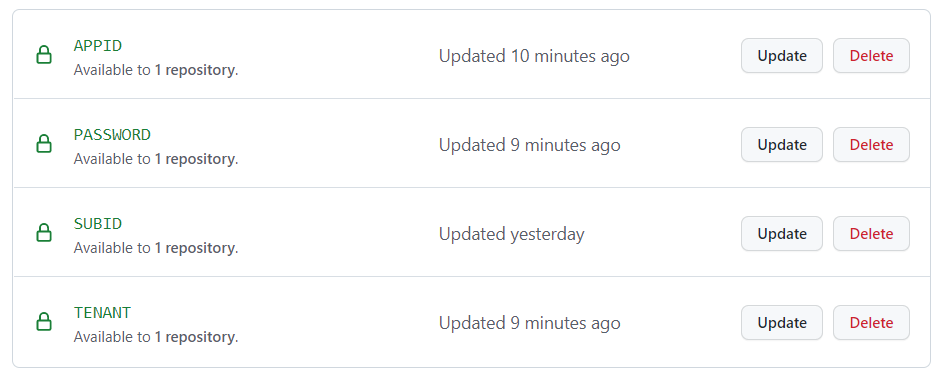
These demos require CodeSpaces. This repo is configured to create a CodeSpace with all the required tools. Simply fork this repo and setup the Codespace secrets and assign them to your fork.
To create the Codespace secrets you will need an Azure service principal, tenant and subscription id.
When the Codespace is created it runs a script to log in to the Azure CLI. It uses a service principal and needs the appid, password and tenant all of which are returned when you create a service principal. You can use an existing service principal or create a new one using the command below. You can learn more on the Create an Azure service principal with the Azure CLI page.
az ad sp create-for-rbac --name DaprServicePrincipal
{
"appId": "00000000-0000-0000-0000-000000000000",
"displayName": "DaprServicePrincipal",
"name": "00000000-0000-0000-0000-000000000000",
"password": "000000.0000000000.000000000-000000",
"tenant": "00000000-0000-0000-0000-000000000000"
}
Save this information because there is no way to retrieve it again.
You will also need the id of the subscription you want to use. You can retrieve that running the following command.
az account show -o json
{
"environmentName": "AzureCloud",
"homeTenantId": "00000000-0000-0000-0000-000000000000",
"id": "00000000-0000-0000-0000-000000000000",
"isDefault": true,
"managedByTenants": [],
"name": "Subscription Name",
"state": "Enabled",
"tenantId": "00000000-0000-0000-0000-000000000000"
}
With the appId, password, and tenant from the service principal and the id from the subscription you can set the Codespace secrets. You can learn how to set them on the Managing encrypted secrets for your codespaces page. Make sure you assign them permission to the fork of this repository.
All the scripts in the repository are PowerShell scripts. When using Codespaces the terminal should default to PowerShell, if not type pwsh to switch.
$ pwsh
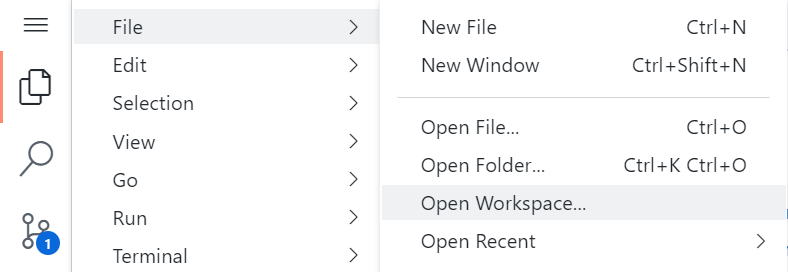
Each demo has a workspace file in the root folder. Select the workspace for the demo you want to run and click the Open Workspace button in the lower right corner.
This will reload your Codespace and scope your Explorer to just the folders needed for this demo.
When you are ready to load another workspace select Open Workspace... from the file menu.
In the root of each demo workspace is a demo.ps1 file. From a terminal execute this file to load the sampleRequest.http file and issue the dapr run command. The demo.ps1 file can accept a -env parameter to run the demo against cloud resources. When the -env parameter is used the script will provision the cloud resources if needed. The required cloud infrastructure can be deployed ahead of time by running the demo.ps1 with the -deployOnly switch. The script uses the Azure CLI to deploy a bicep file to deploy the required infrastructure.
To encourage best practices the components are all configured using secret stores. After the infrastructure is deployed the script will collect all the information needed to configure the components and write the data to a local_secrets.json file or in environment variables. The file or environment variables are read in a secret store component used to configure the other components. The local_secrets.json file is listed in the .gitignore file of the repository so they are not accidentally committed.
To delete your cloud resources and restore the repository to pre-demo state run the cleanUp.ps1 file in the root of each workspace.
See the README.md files in each demo folder for instructions on how to run the demo.