LAPS solution for macOS managed with Jamf
Below is a guide for setting up LAPS for macOS on your Jamf instance. The LAPS solution creates the local admin account, randomises and encrypts the password, uploads the encrypted password to Jamf and then a self service app is used to decrypt and show the local admin password to your engineers.
v2.1 now uploaded and available. Check the Change log for changes and improvments.
LAPS v2 uses Swift Dialog the original project can be found here https://github.com/bartreardon/swiftDialog All credit for swift Dialog goes to the owner and creator please support their project.
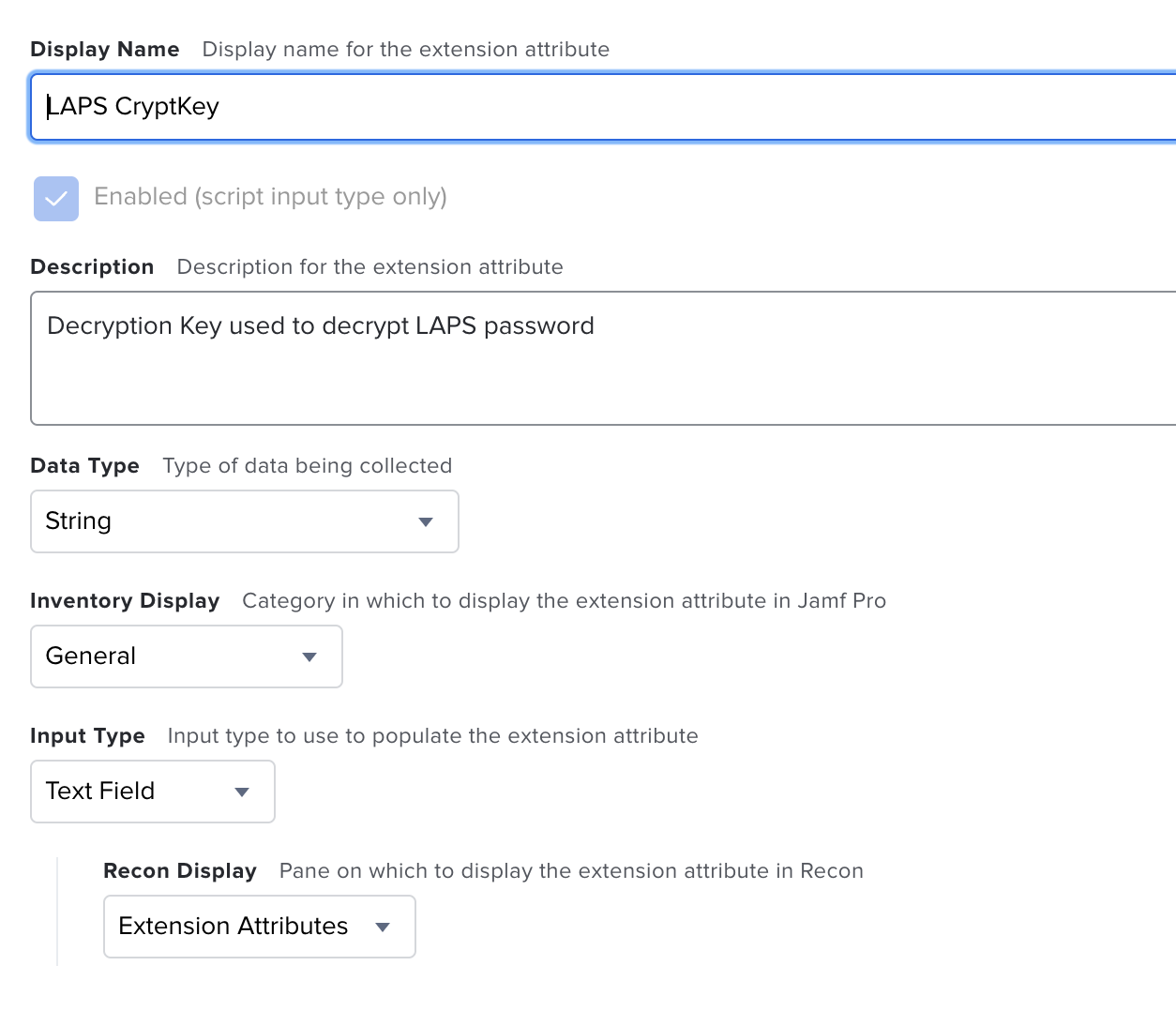
Create an Extension Attribute to store the encrypted password in the Device inventory. Name this extension attribute "LAPS CryptKey".
Repeat this process for the encrypted secret calling it "LAPS Secret" and password reset called "LAPS Reset Password". You will end up with 3 Extension attributes.
Upload both Scripts from the git repositry to your Jamf instance and give them a name to go with their function.
Upload the LAPS pkg file to your JAMF Instance.
Set the parameters in each script and name each $ function to what it does. (each function can be found in the script header)
Creation and password cycle script
Decryption script
Create 4 policies.
- One for Creating the admin and cycling the password. Create this with a trigger of "Ongoing" and a custom trigger "CreateLAPS". Add the Script and pkg.
- One for Running the LAPS Script Monthly using the custom trigger. Enable the "Files and Processes" Payload and then in the "Execute command" option enter "jamf policy -event CreateLAPS"
- One for the self service Decryption app.
- One for cycling the password once its viewed.
In each policy set the script functions with your credentials and URL.
Creation and password cycle script
Decryption script
Make sure the Decryption script is set as a self service app. You can upload your own Icon and name it how you wish.
Create a smart Group called "LAPS Reset Password" and set the criteria as below. Scope the "Reset Password" Policy to ONLY this group.
The decryption self service policy can be scoped to your Engineers so they can view the local admin password.
The app works as follows:
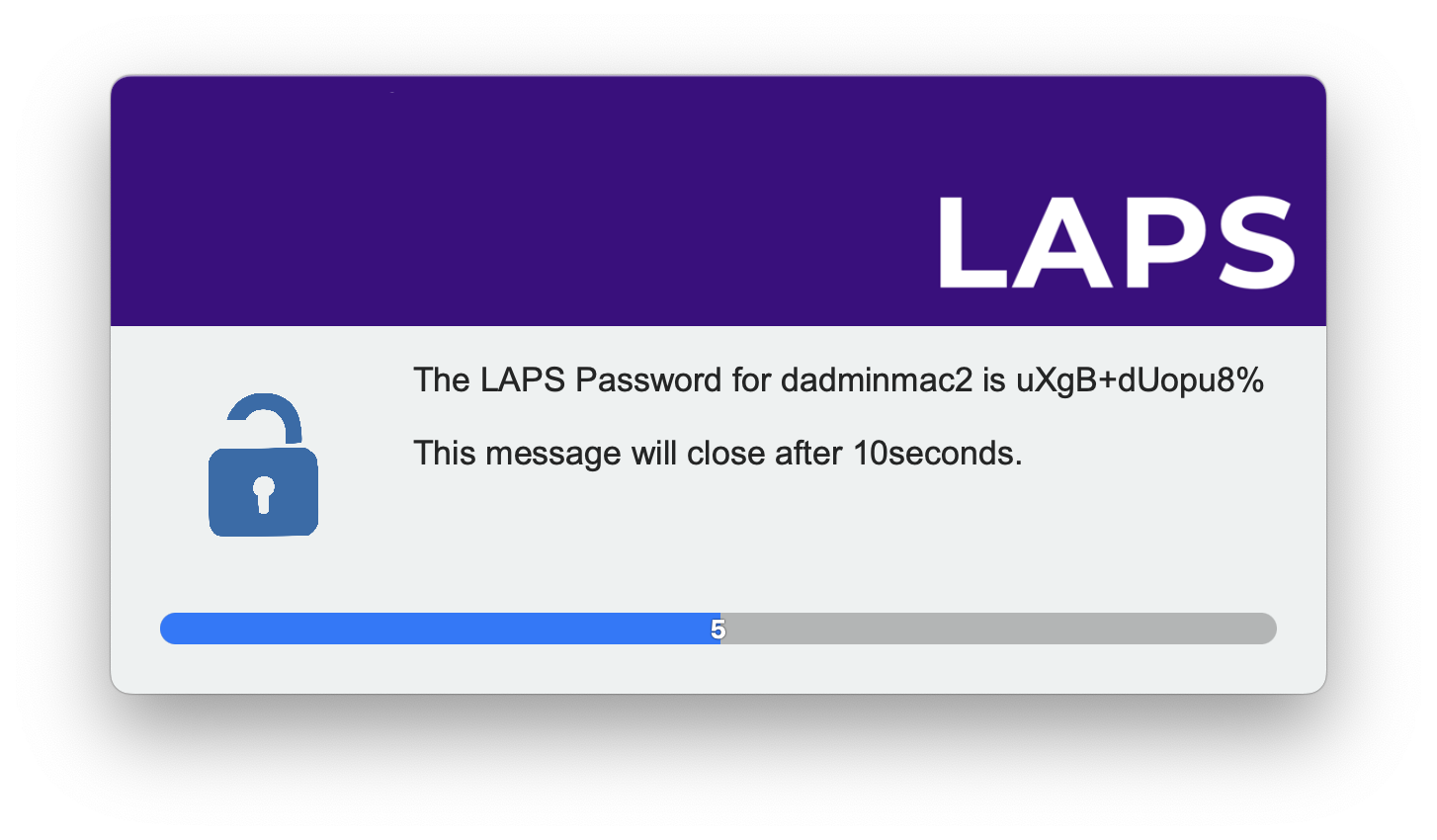
Enter the device name of which you require the local admin password for
The engineer will then be presented with the password which will disapear after 10seconds
If all is working ok then in the computer inventory record you should see the Extension attributes populated as below. Please note, none of these are the local admin passwords and will not do anything if just copied and pasted.