-
Notifications
You must be signed in to change notification settings - Fork 104
Accessing PCI devices #12
Comments
|
Hi @kakaroto. You can get it through several ways:
You can also use the suffix "P" to access physical memory (like "0xf0080004P"). ME doesn't have I/O ports, if I recall correctly. |
|
Hi @h0t, thanks for the quick answer. I guess my issue was the selector, I was setting the breakpoints on the linear address and that doesn't seem to work. Weirdly though even if I break inside the interrupt now (int 0x80) the "flags" register still show ring-3 and yes, it seems you're right, ME has no I/O ports according to datasheet vol.2, I had missed that it seems. I'm still unclear then on how we can access any device, without I/O ports, I can't access PCI devices without using MMIO and I can't figure out what the MMIO addresses for PCI is (or for IOSF-SB or for anything pretty much). in your README.md, you talk about HROMMB at offset 0xe20 of the MISA MMIO, and I can see in datasheet vol3, section 27.13 that HROMMB is at offset 0xe20 of MISA MMIO, but I don't see how you got that MISA MMIO is at 0xf0000000P. Also it doesn't seem to help me figure out how to access the PCI configuration space (or if that's not possible, how to use IOSF-SB to access a PCI device, although vol2 says that CSE has access to all those PCI devices so there must be a way to enumerate them). FYI: I've been working on reversing the exact details of the exploit used here to write up an analysis/explanation of how it works (since you used syslib_tracer, not sys_shared_mem to achieve it on apollolake, it's technically a different method from what you showed at Blackhat), the only thing missing for me to figure out is what that side_band_mapping in the ROPs does which sets values in segment 0xC7 and why you call it with the values 0x706a8 for DCI and 0x70684 for DfX personality. Any hints would be welcome! Thanks for the help! |
|
Hi kakaroto, |
|
Hi @kakaroto, |
|
Thanks for the help. @h0t now that I know how to access the ATT, I'll try and bruteforce my way around it, maybe I'll find something, but with the datasheet saying "The CSE can access IOSF-SB Private CR space from an SB ATT window" and your Visa slides saying "Intel CSME has full access to SB (via its own ATT bridge with a privileged SAI).", I guess I should be able to access the PCI devices with the right DestID sent to the right IOSF CR in the right ATT window... The problem is knowing what values are needed. I'd like to be able to access PCIe, USB or SATA PCI devices so yes, I want the non-private PCI devices which according to your presentations should be doable from the ME but I can't find information on how to achieve it.. |
|
By the way, I still don't know how you got the 0x706a8 (for DCI) and 0x70684 for (DfX aggregator) values. I assume those are the Dest ID to the IOSF SB through ATT window, but I don't see where you found them (I did find 0x10070684 in TXE code but not 0x706a8) or how you got that full list of SB ports for LBG in your bonus slides. (I did find the 0x54 IR command for DFX Aggregator from the TDef files, so at least there's that answer). |
|
I'm not entirely sure about the highest nybble of the sideband address, but the breakdown of that bitfield is:
Which for the examples yields:
And to find those numbers, there are tables in bup and busdrv which contain all devices that are available at runtime, which have base addresses, SB endpoints, PCI BDFs and so on. Source: Own research and https://twitter.com/_markel___/status/1121131631245443074 |
|
Thank you Peter, that was very helpful. I facepalmed when I realized the sideband port is basically the PCR port id. I just made a loop to dump all of their bars and found quite a few. I'm not sure about those readop/writeop or flag28, it didn't seem to make any difference to me what I set in bits 24 and up. I did manage to get the MODPHY (0xa5) and USB Host (0xa2) BARs, just not the PCI config space. Unfortunately, I still can't get the main CPU to boot (seems to block in an infinite loop at 0x35644), if I can't figure it out soon, I'll be opening another issue (or re-open #11). |
Did you try activate HAP-mode? #11 (comment) |
Yes of course. I've tried the F5 image as is and the Brix boots, I tried with the exploit only, and I get that expected behavior of it shutting down continuously, I enabled HAP bit and I get that infinite loop issue in bup where it doesn't seem to finish that initiatlization (it was at index (ebx) 0xC and byte_97258 has 0x2 and byte_97259 has 0x3). I used JTAG to make it unlock it (changed byte_97258 to 0x3) and BUP did finish but then the kernel went into the hang function. I have the v2 hardware and so far, I haven't been able to debug what's the issue, especially with you saying it works on your side. |
|
Hi @ValZapod. We aren't going to publish your collection of visa.xml files. You can get it from Intel System Studio, installers is available on Intel's website. We don't use USB-C. Unfortunately, I have no idea about DCI throgh USB-C. What is your hardware? Please create separate issues for different topics! |
|
Hi again, I'm still struggling to get access to PCI devices here.
Read opcode 4:
There's nothing else when I try the other read opcodes. As you can see, there's no LPC, USB, HDA, SATA, PCIe, xHCI or SPI device that the sideband channel grants access to. I haven't looked at the private PCI devices yet, but without a valid device ID, I can't really figure out what they are for, and their class IDs are all zero apart from the Host bridge. I also found one PCI-to-PCI bridge device, but even after enabling MMIO access and bus master enable (PCI command 0x6) and setting the primary and secondary bus channels, it didn't seem to give me access to an additional PCI devices/buses. From your presentation, you said that the ME had access to every device on the machine, was there anything that needed to be done in order to enable that access ? If there's anything you can help with, I'd appreciate it. Thanks! |
|
By the way, I thought I should clarify something. I've tried using This shows that xHCI is indeed available on port 0xe6 with opcode 0 and bar 0, it's readable via JTAG but not by the ME core itself. |
|
Hi @kakaroto, the next are some explanations regarding your problem and ME ability to access platform devices (IPs):
|
|
Hi @markel777 and thanks a lot for taking the time to explain that. It was very helpful in better understanding how the IOSF SB works. As you can see from that Are you able to reproduce this problem from your side? Do you have any other ideas on what could be preventing the ME thread from accessing the SB channel ? Thank you! |
|
@markel777 sorry for bumping this thread. It's been a month and I'm wondering if you have any updates relating to this or any ideas for me to explore ? I don't know what is different from using the I think the issue might somehow be related to the EPMASK register, but when I checked the P2SB device's PCI config, the EPMASK isn't blocking access to those ports. I assume that this is because that configuration is specific to the host, and there must be an equivalent one for the CSME. Any ideas where to find it or access it (none of the CSME PCI devices seem to match)? I'd appreciate if you have any other thoughts/ideas that I could experiment with. |
|
+1 year later, and @kakaroto's blog post gives some more information about why the XHCI registers are write-only on Skylake—because of the setting of the |
|
And a link to the blog post itself…: |
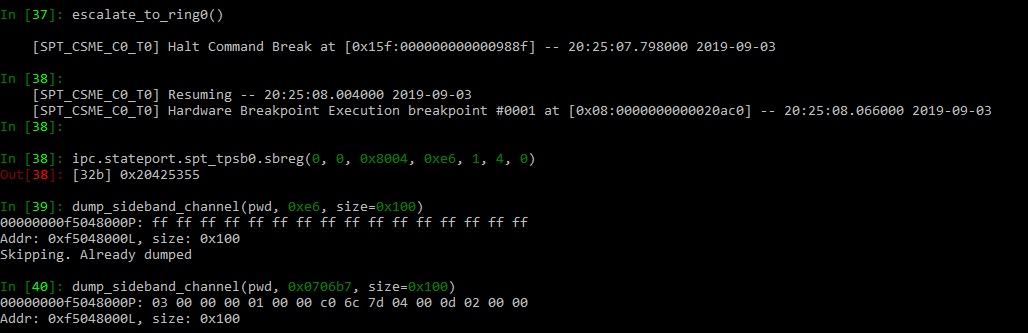


Hi, I have a question and maybe it's a dumb one but I can't seem to figure it out. When the JTAG is enabled, it's from the BUP process, which is a user space program, at Ring-3. Is there a way to escalate privilege to kernel mode? I can't seem to be able to set a breakpoint in kernel code, modifying the TSS doesn't work and thread.step() doesn't actually seem to work either (does the same as thread.go())
I'm not sure how we're supposed to get the full access to the ME from Ring-3, I'm trying to just read io port 0x80 for example (or any I/O port for that matter) and it all returns 0xFFFFFFF and that's because the TSS for BUP process has IOPB empty.
Any advice?
Thanks!
The text was updated successfully, but these errors were encountered: