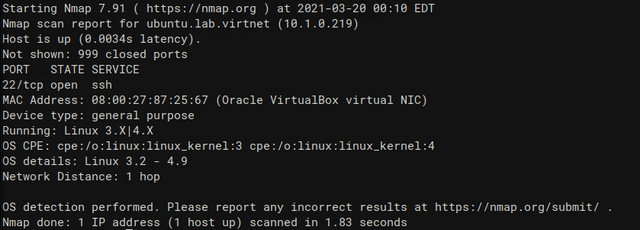
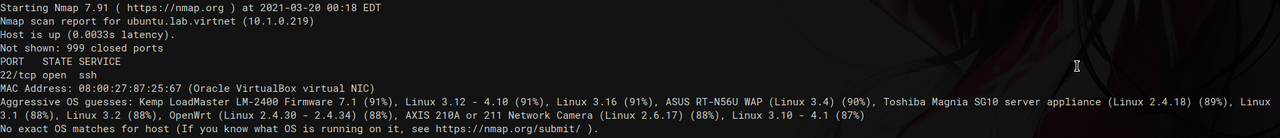
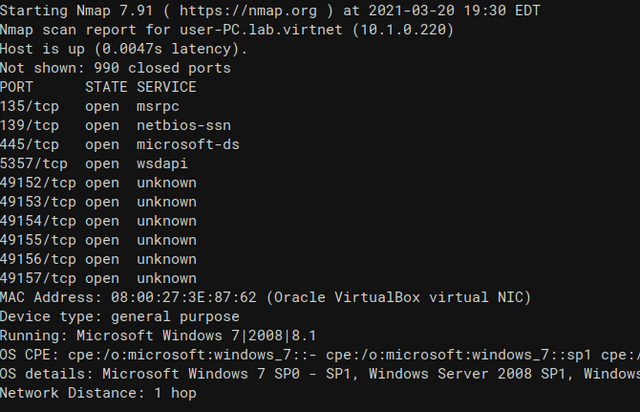
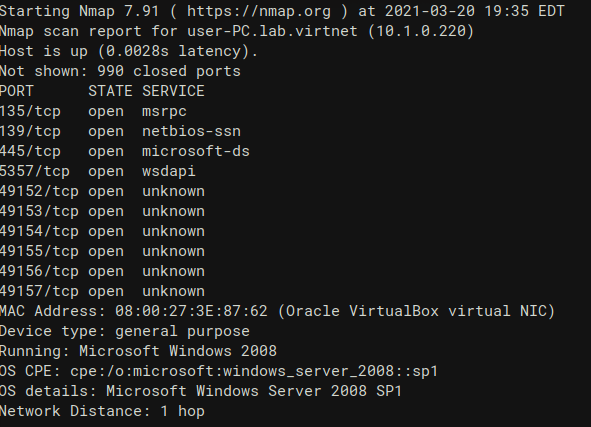
spoof OS detection by messing with the tcp stack
Based on security cloak by Craig Heffner: https://web.archive.org/web/20061202015837/http://www.craigheffner.com/security/
Inspired by: https://nmap.org/book/nmap-defenses-trickery.html#nmap-defenses-os-spoofing
./impostor <profile>
profiles are defined in profiles.ini
unfortunately the results are currently far form perfect. will most likely have to play with the window size on linux
windows version