Author: tg
Step 1:
This is simple Challenge we have to join Slack channel but flag is we can see in image.
Step 1:
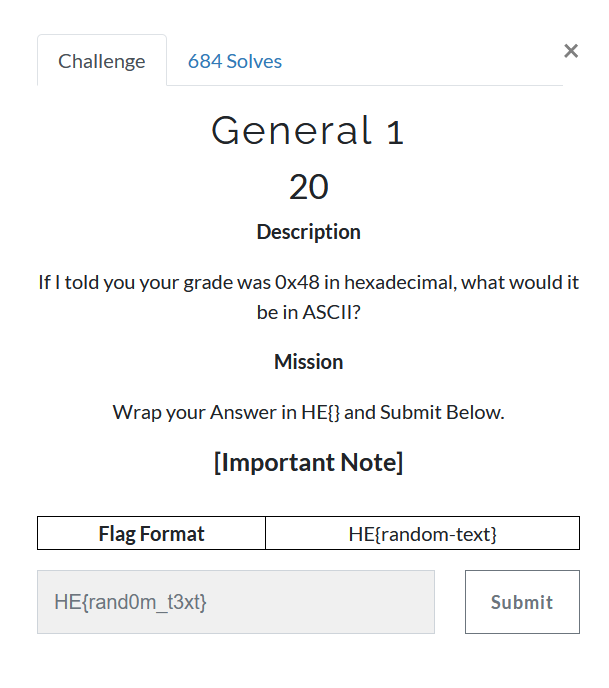
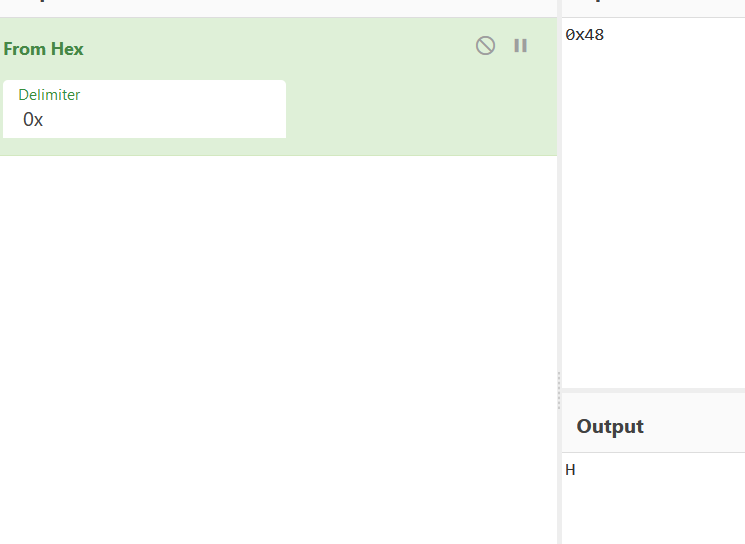
In given statement we have to change Hex value to ASCII value is `0x48`. do manualy or online.
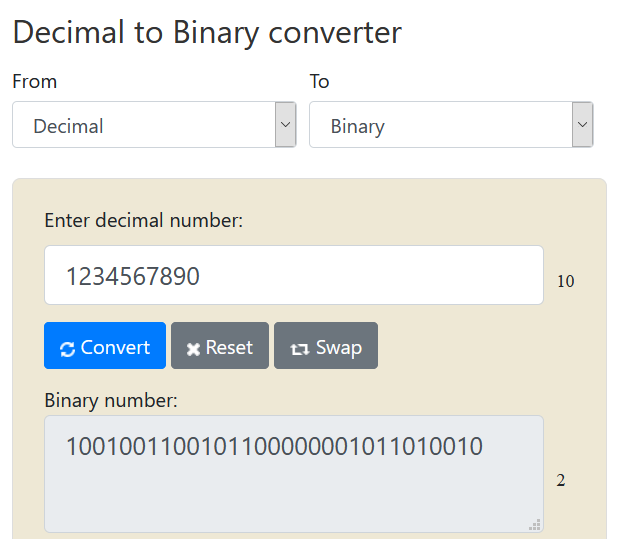
Step 1:
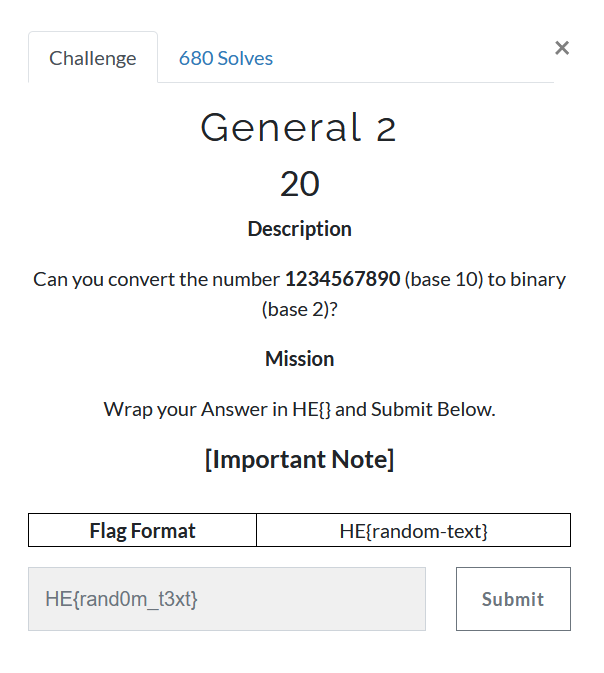
In given statement we have to convert Base 10 (`Decimal`) to Base 2 (`Binary`) that value will be our flag.
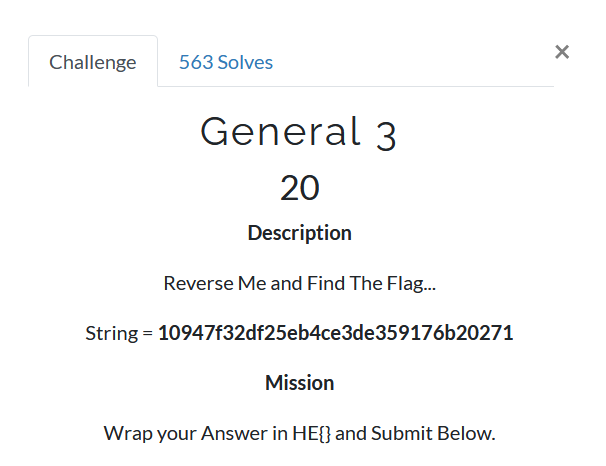
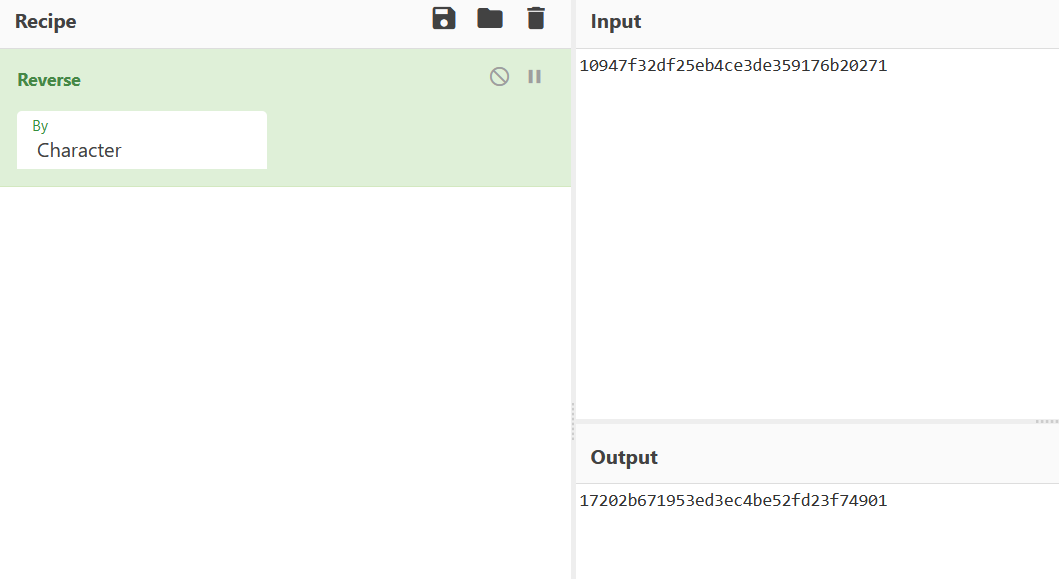
Step 1:
In given statement given value is string in HASH form but statement said that just only reverse it not to convert in a actually string.in CTF play you have to read statement carefully because mostly main hints are give in statement just we have to look carefully.for this we will use `CyberChef`.
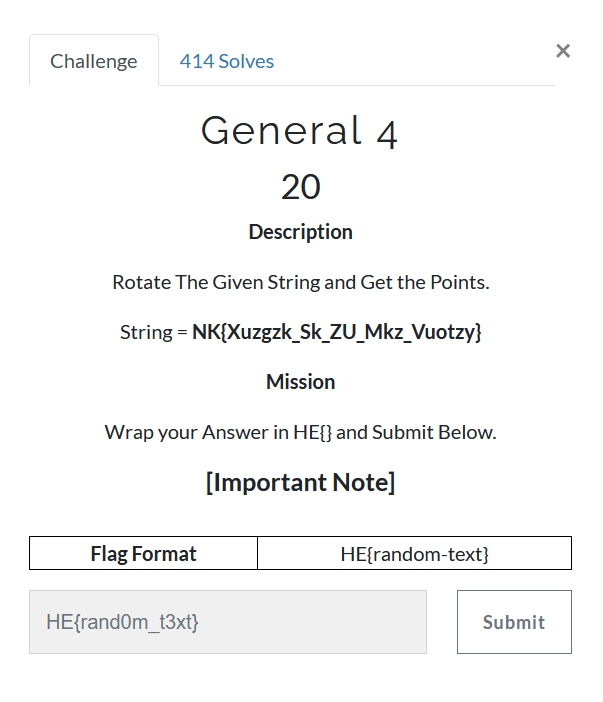
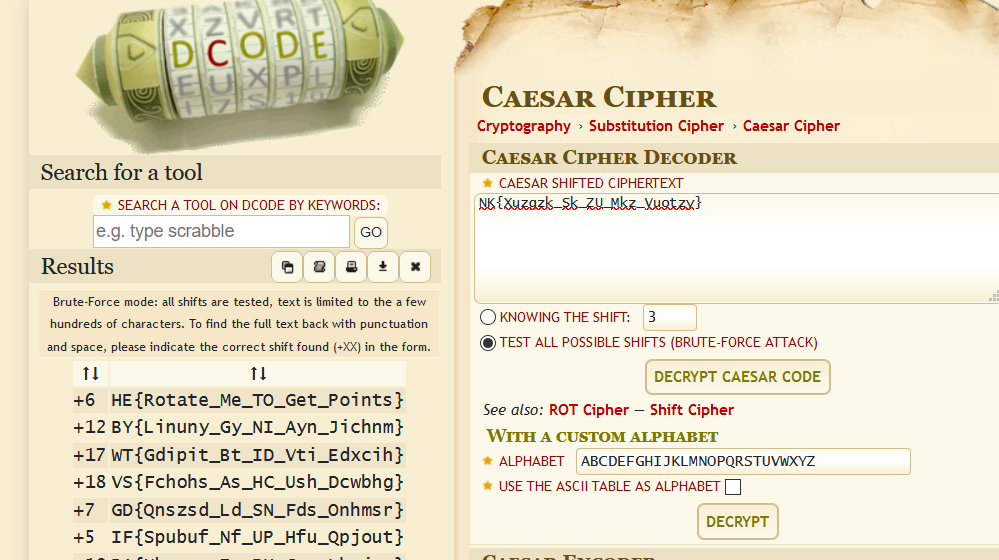
Step 1:
Read statement that say rotate the string may be this a kind of shift cipher so try them.and find out that is a Caesar Cipher so we have online tool.
Source : https://www.dcode.fr/caesar-cipher
Step 1:
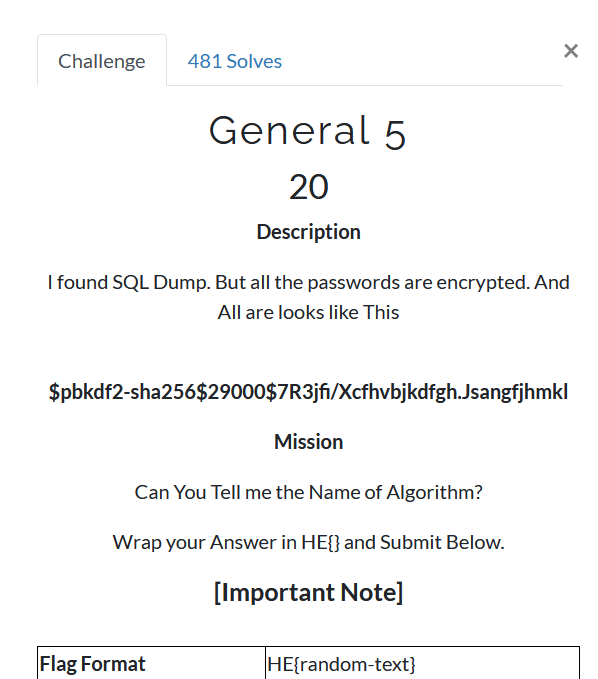
Read statement that is a SQL Dump and we have to find Name of Algorithm
$pbkdf2-sha256$29000$7R3jfi/Xcfhvbjkdfgh.Jsangfjhmkl
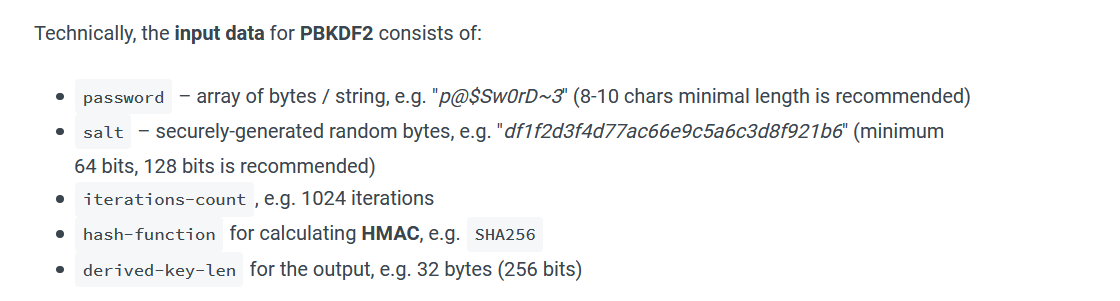
key = pbkdf2(password, salt, iterations-count, hash-function, derived-key-len)
Source : https://cryptobook.nakov.com/mac-and-key-derivation/pbkdf2
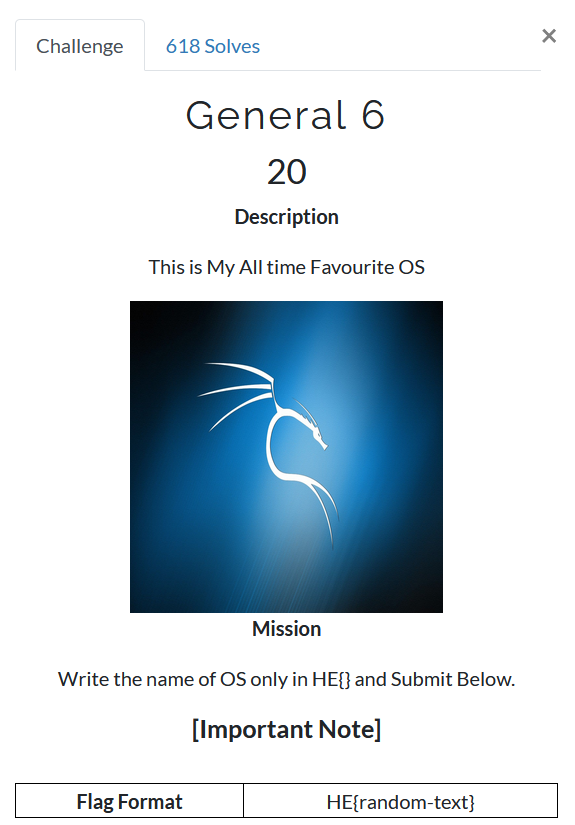
Step 1:
See the image given in the Challenge . Its a kali logo/Image.
Source : https://www.kali.org/
Step 1:
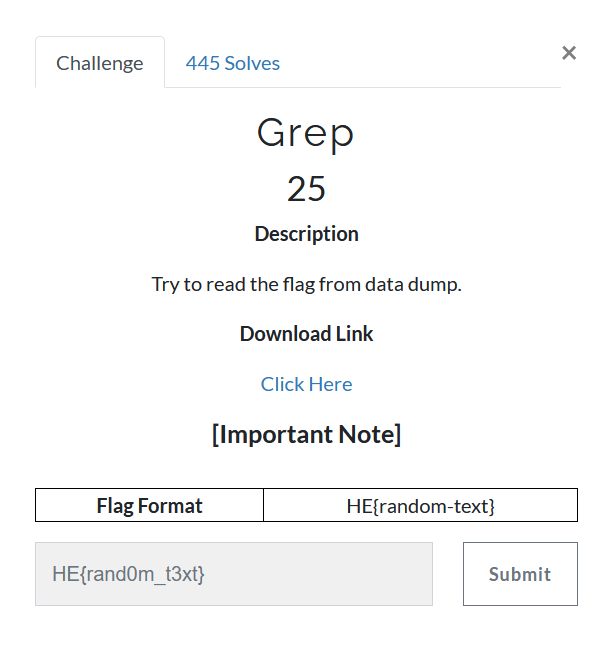
Read statement flag is in given file and that file contain some random text and we have to use GREP to catch the flag
Step 1:
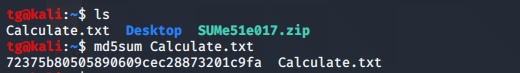
Read given statement we have to calculate HASH of file so file in not tempared.use kali for this.
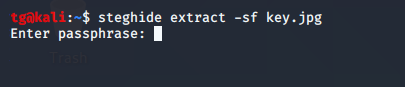
So in Challenge we have a JPEG file and we have to find flag which embeded in image.so i try with Steghide and image is password protected so we have to bruteforce the thing .
Step 2:
I used stegcracker for bruteforce and rockyou.txt as worldlist so no use so i just look at the source of file and Yes flag was there.so lession is always try basic thing first.
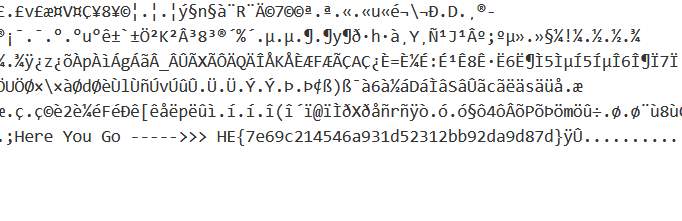 Source : https://github.com/Paradoxis/StegCracker
Source : https://github.com/Paradoxis/StegCracker
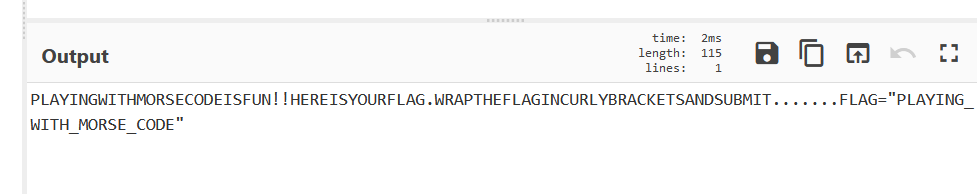
Read statement and find the clues M***** _ Code and we have attach Image so it means may be kind of Morse code is embedded in that Image. Again do basic forensic on image and find out that image is password protected. Bruteforce is method.
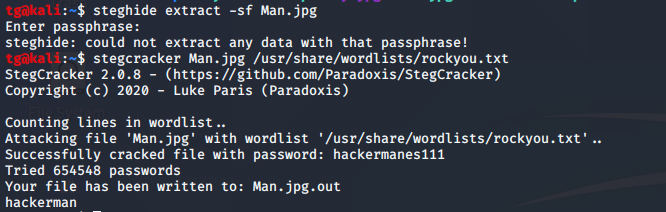 Source : https://github.com/Paradoxis/StegCracker
Source : https://github.com/Paradoxis/StegCracker
Step 2:
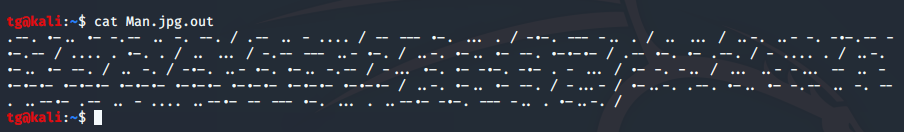
We get a extracted file name Man.jpg.out and contain out Morse Code. decoe the morse code .
Step 1:
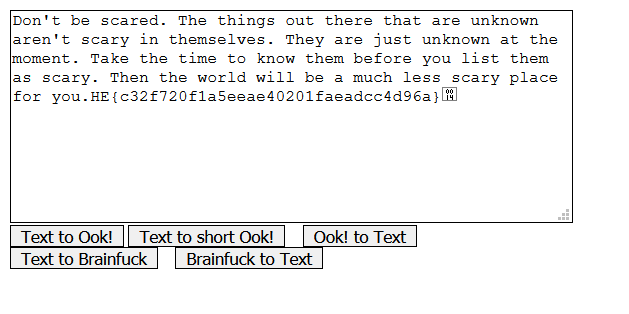
Read statement and name of CTF that will give you a hint and its a crypto section and its a esoteric programming language and its Brainfuck cipher.
Source : https://www.splitbrain.org/_static/ook/
Extra Source : https://en.wikipedia.org/wiki/Esoteric_programming_language
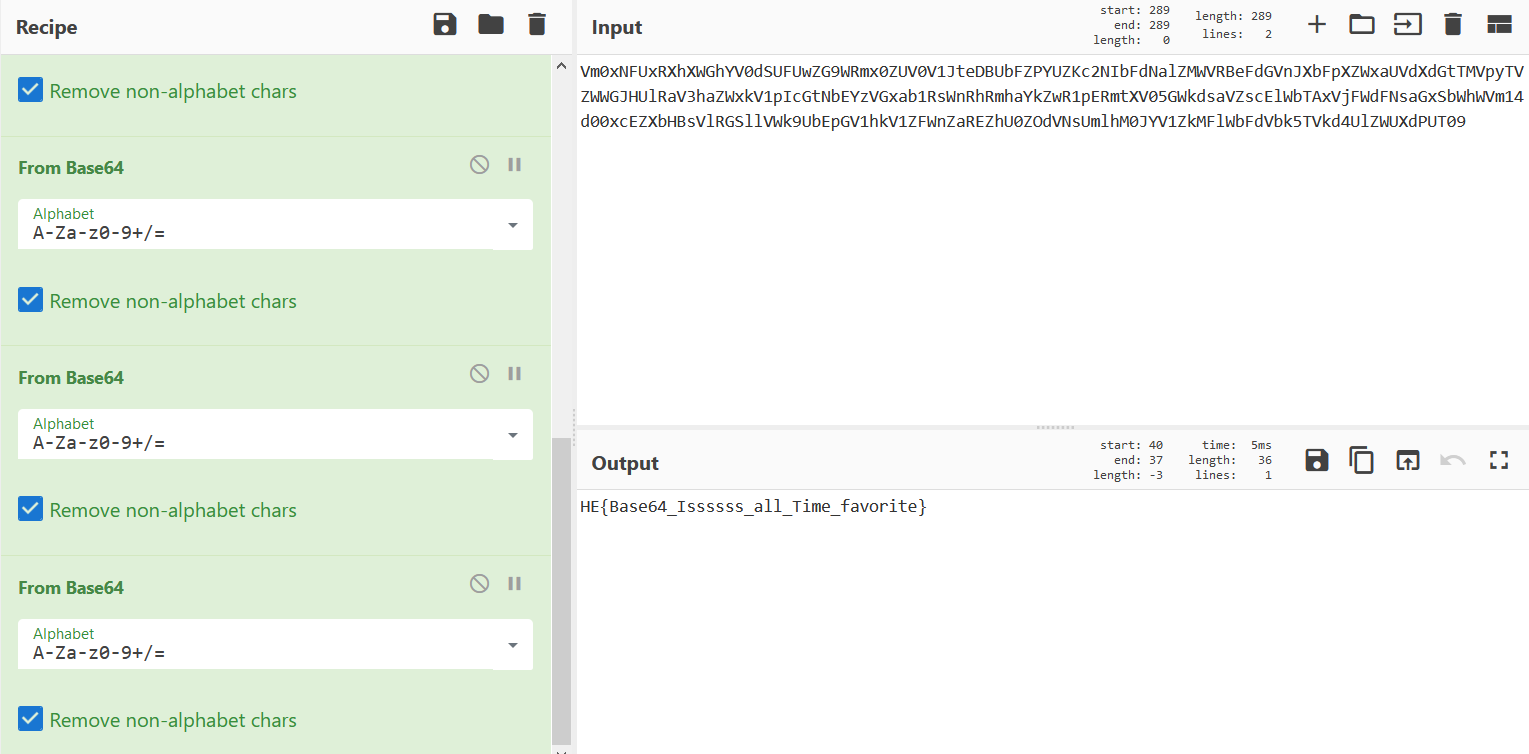
See the contain try CyberChef. so we find out that its Base 64 encode in 7 time using same method .you have decode cipher seven time.Suggestion is alway try any cipher in CyberChef first.
Step 1:
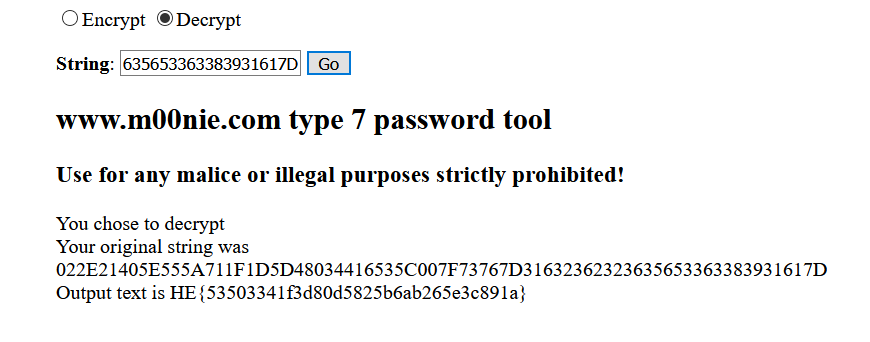
Download the file see what contain in it. this is random alphanumaric data and we have hint is SEVEN so size of passwords bit is 7. I try muliple method but no outcome.after sometime i find out that its a password and got thre result as Cisco type 7 password.
Random data:
022E21405E555A711F1D5D48034416535C007F73767D31632362323635653363383931617D
Source : https://www.m00nie.com/type-7-password-tool/
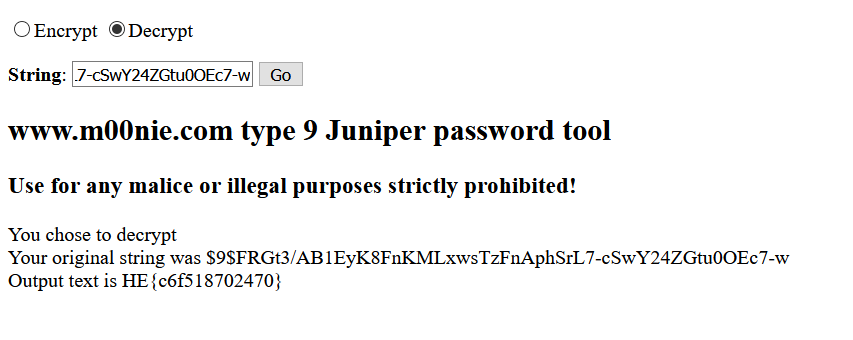
This is a similar CTF to the SEVEN just diffrence is that password was Cisco type 7 and this is Juniper type $9$ Hashed password.
Source : https://www.m00nie.com/juniper-type-9-password-tool/
In the attachment we have a image and contain some numbers but may be in flag form.
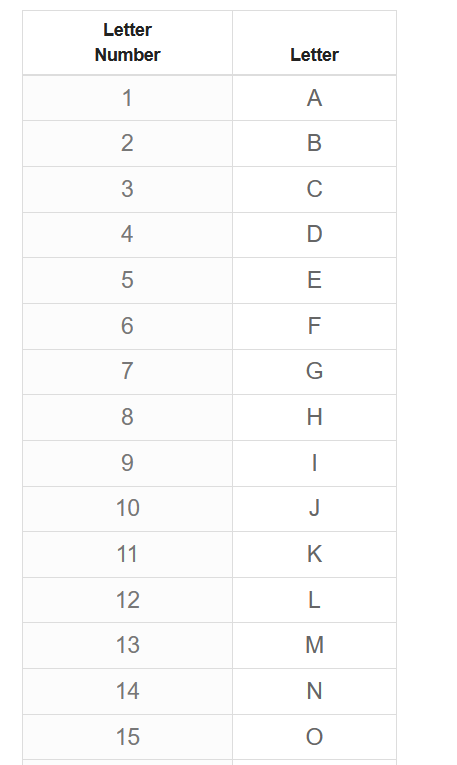
May be its really numbers game so pull out English alpha with numbers and we have numbers in image.
85{20 8 5_2 1 19 9 3_14 21 13 2 5 18_7 1 13 5} HE{the_basic_number_game}
Source : https://www.worldometers.info/languages/how-many-letters-alphabet/
Step 1:
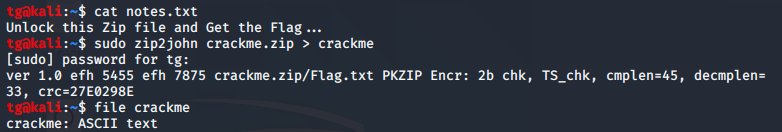
Challenge name suggest us that we have to crack lock means have to do bruteforce. and we have a file attach that contain crackme.zip
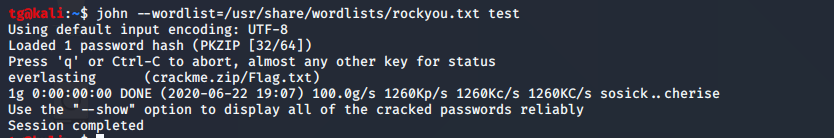
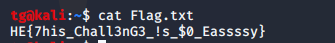
Step 2:
We will use john for crack a zip.notes.txt not contain anything.