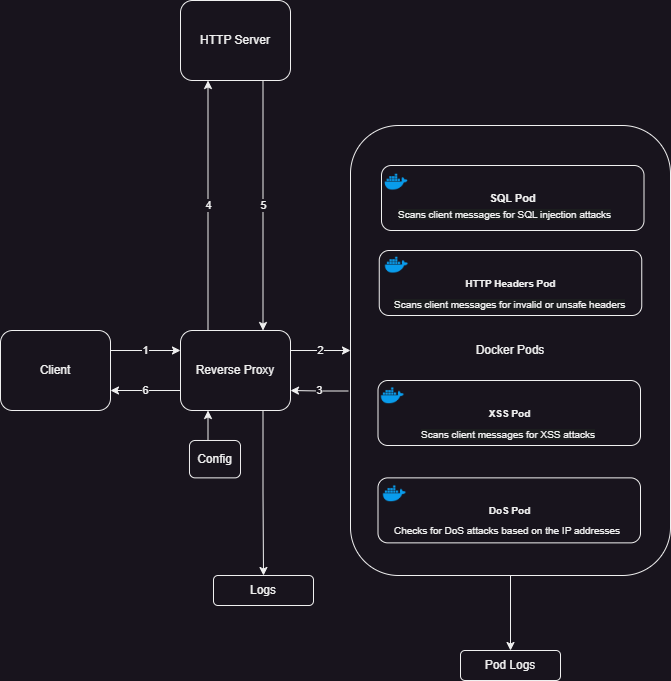
- The reverse proxy first intercepts the client's connection.
- It then inspects the destination URL and routes the request to a specific "pod". This pod is responsible for conducting various validation checks on the request.
- If the request passes all validation checks and is deemed non-malicious, it is then relayed to the server.
- Throughout this process, both the proxy and the individual pods generate and maintain logs for tracking and auditing purposes.
-
Notifications
You must be signed in to change notification settings - Fork 0
47Cid/Castle
Folders and files
| Name | Name | Last commit message | Last commit date | |
|---|---|---|---|---|
Repository files navigation
About
A neat way to consolidate web security libraries (such as xss-filters, DOM-purify, SecureHeaders, etc) into a single framework.
Resources
Stars
Watchers
Forks
Releases
No releases published
Packages 0
No packages published