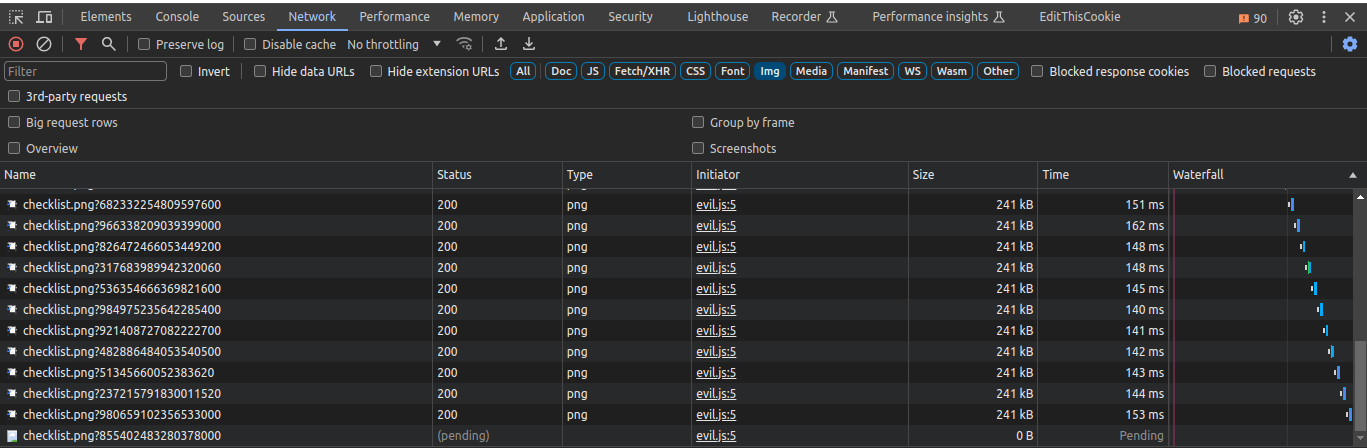
JavaScript-based DDoS is a type of DDoS attack where JavaScript is used to generate a large number of requests to a targeted website or server. These requests can be generated from various devices and browsers, making the attack harder to detect and defend against.
JavaScript-based DDoS is an exceptionally perilous threat, as malevolent actors can inject such scripts into already compromised websites, effectively utilizing their traffic as a potent weapon for executing devastating DDoS attacks. This presents a deeply alarming scenario since, unbeknownst to the proprietors of compromised sites, all visitors unwittingly contribute to the assault.
What makes this threat particularly insidious is that it renders traditional IP blocking methods nearly ineffective. Since the traffic originates from real users, it becomes exceedingly challenging to distinguish between legitimate visitors and malicious agents.
Furthermore, when considering a website with 10,000 visitors in an hour, the potential impact becomes staggering. This influx of users could result in a mind-boggling 3,600,000,000 requests directed towards the site in just one hour. This highlights the fact that even with a relatively modest volume of visitors, this type of attack has the potential to devastate server infrastructures.
In many cases, unfortunately, the only effective protection against "JavaScript-based DDoS" attacks may indeed be implementing CAPTCHA verification for all visitors during a specific time period. This measure means that all users will need to solve CAPTCHA challenges to prove that they are real humans and not automated bots.
This material and the information provided within this conversation are intended for educational purposes only. The author are not responsible for any misuse, unlawful activity, or damage that may result from the use of this information or tools for improper purposes.
Contributions are welcome! Feel free to open issues or submit pull requests to improve this project.