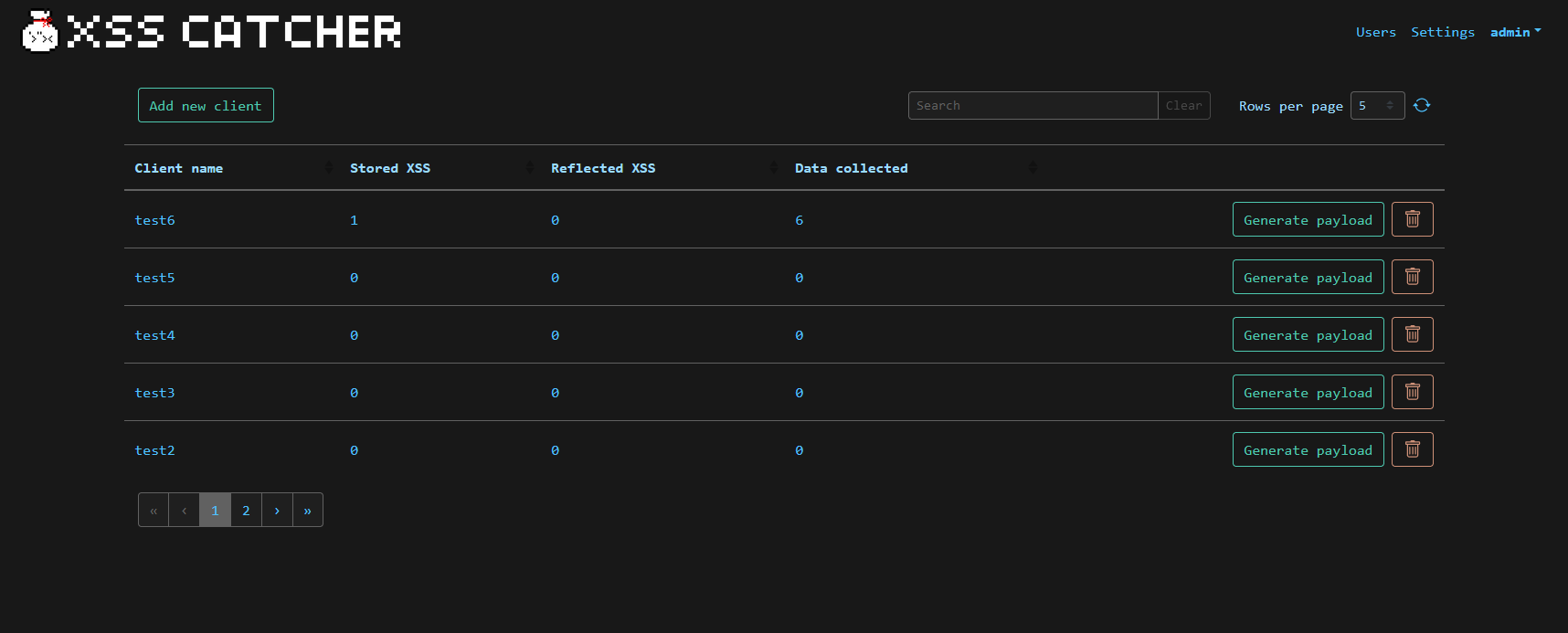
A blind XSS detection and XSS data capture framework that runs on Flask, VueJS and PostgreSQL.
Features • Installation • Updating • First login • API documentation • Demo • Troubleshooting • Credits
- Generate simple and customizable XSS payloads with an easy-to-use payload generator
- Send notifications when a new XSS is caught using webhooks (Slack, Discord or automation format) and email
- The destination email or webhook can be configured globally and per client
- Multi-user with admin and low privilege users
- Multi factor authentication with TOTP
- Allows capture of cookies, local storage, session storage, and more
- Stores additional information about the XSS such as like HTTP headers, source IP address, timestamp, etc.
- Acts as a "catch-all" endpoint. Just send your data in the querystring (GET) or body (POST) to your client's URL and XSS Catcher will catch it!
- Leverages html2canvas and fingerprintjs
- Captures the full DOM so you can easily know where the payload triggered
- Allows you to add custom tags to your XSS to better categorize and search them.
- Allows you to run custom JavaScript code and capture the output.
- Support up to 5 API keys per user to automate advanced attack scenarios when combined with webhooks
To clone and run this application, you'll need Git, Docker, Docker Compose and make. From your command line:
# Clone this repository
$ git clone https://github.com/daxAKAhackerman/XSS-Catcher.git
# Go into the repository
$ cd XSS-Catcher
# Start the application
$ make start# Pull the repository
$ git pull
# Before running an update, it is recommended to make a copy of your database in case something unexpected happens
$ cp -r /var/lib/docker/volumes/xss-catcher_xss-db/ /var/lib/docker/volumes/xss-catcher_xss-db-bak/
# Update the application
$ make update# Start the containers
$ make start
# Stop the containers
$ make stop- Default credentials to connect to the Web interface are admin:xss
- Default Web port is 8888
The Postman collections can be found here: https://www.postman.com/maintenance-architect-74448403/workspace/xss-catcher
In order to avoid JavaScript mixed content errors when the XSS payload is triggered, it is highly recommended to put XSS Catcher behind a reverse proxy providing valid TLS certificates.
You can set a new database password by following these steps:
# While XSS Catcher is running, attach to the database container
$ docker exec -it xss-catcher_db_1 bash
# Log into the PostgreSQL database
$ psql -U user xss
# Set a new password for the user "user"
$ \password user
# Exit PostgreSQL and the container
$ exit
$ exit
# Create a new file in the XSS Catcher directory named ".db_password" with the following content
POSTGRES_PASSWORD=YOUR_NEW_PASSWORD
# Stop the application and start it again
$ make stop
$ make startI updated to XSS Catcher v2, understood that my data would not carry over from v1 as stated by the release note and update warning, but I'd like some pointers on how I can import my data to the new PostgreSQL database
While there is no guarantee about the following procedure, it is possible to "import" the data from v1 to v2 with a very manual (but achievable) process:
# Using SQLite3, create a dump using the database backup file
$ sqlite database-backup.db .dump > dump
# The statements you are interested in are the INSERT INTO statements
# Choose which ones you want to import
# While XSS Catcher is running, attach to the database container
$ docker exec -it xss-catcher_db_1 bash
# Log into the PostgreSQL database
$ psql -U user xss
# To import users, you will have to take the INSERT INTO statements, put double quotes around the table name (user) and replace the 1 and 0 by 't' or 'f' in the fourth and fifth columns.
# Once that's done, you can paste the commands directly into the psql CLI
# To import clients, the INSERT INTO statements can be executed as is
# To import settings, first drop the current settings
$ DELETE from settings where id=1;
# Then replace the 1 and 0 by 't' or 'f' in the fourth and fifth columns
# Once that's done, you can paste the statement into the psql CLI
# Finally, to import XSS, the INSERT INTO statements can be executed as is- Flask
- VueJS
- BootstrapVue
- FingerprintJS
- html2canvas
- Bootswatch Slate theme
- vue-code-highlight
- vue-json-pretty
Usage of this tool for attacking targets without prior mutual consent is illegal. It is the end user’s responsibility to obey all applicable local, state and federal laws. We assume no liability and are not responsible for any misuse or damage caused by this tool.
- Simple One Time Secret - Generate single use, expiring links to share sensitive information
- Source Map Decoder - Quickly decode source maps
GitHub @daxAKAhackerman