-
Notifications
You must be signed in to change notification settings - Fork 446
Home
Shusei Tomonaga edited this page Dec 21, 2022
·
11 revisions
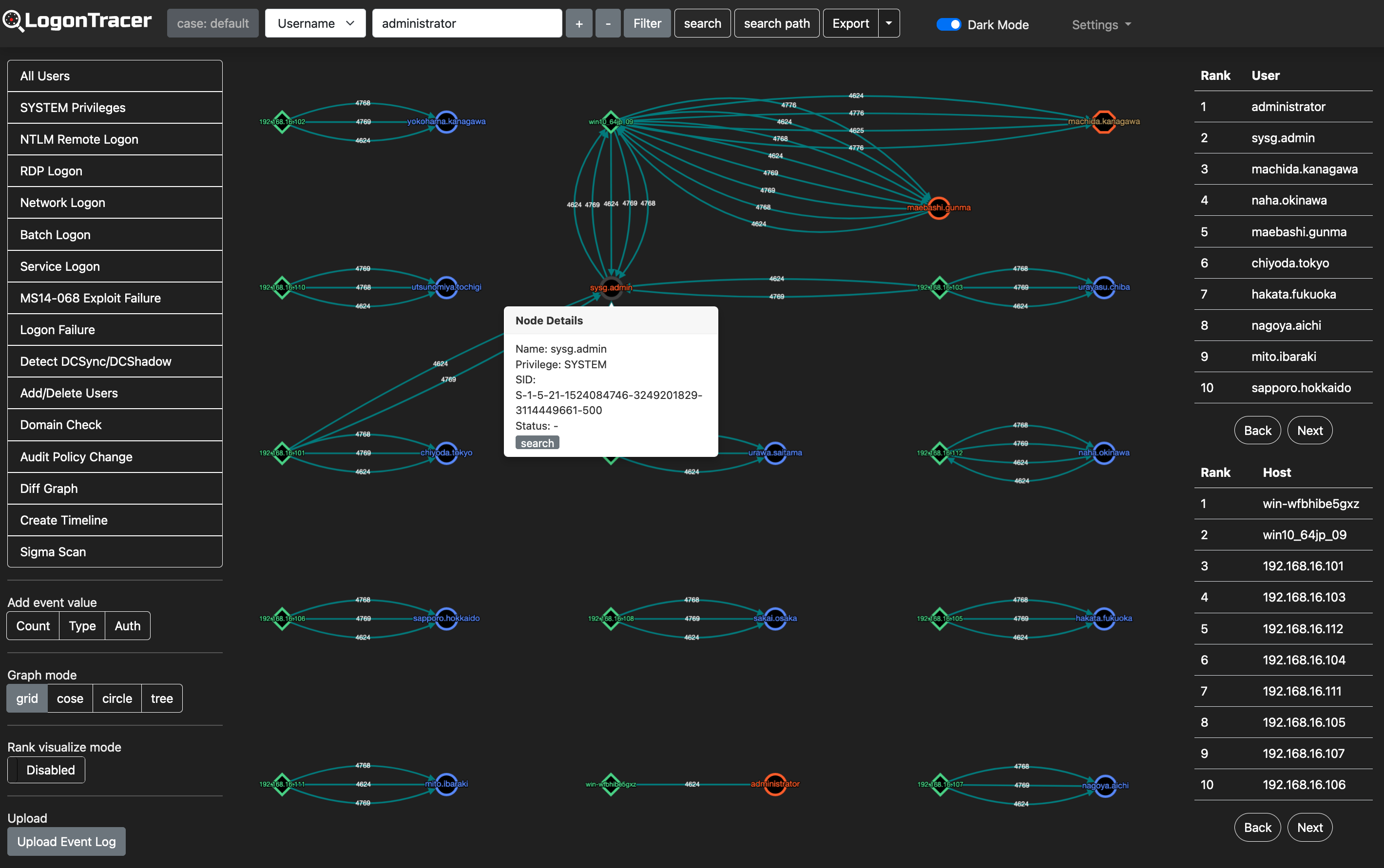
LogonTracer is a tool to investigate malicious logon by visualizing and analyzing Windows active directory event logs. This tool uses PageRank, Hidden Markov model and ChangeFinder to detect malicious hosts and accounts from event logs. This tool visualizes the following event ids related to Windows logon based on our previous research.
- 4624: Successful logon
- 4625: Logon failure
- 4768: Kerberos Authentication (TGT Request)
- 4769: Kerberos Service Ticket (ST Request)
- 4776: NTLM Authentication
- 4672: Assign special privileges
More details are described in the following documents:
- Visualise Event Logs to Identify Compromised Accounts - LogonTracer -
- Investigate Unauthorised Logon Attempts using LogonTracer
Dark Mode