Comprehensive Kubernetes Security from Development to Runtime
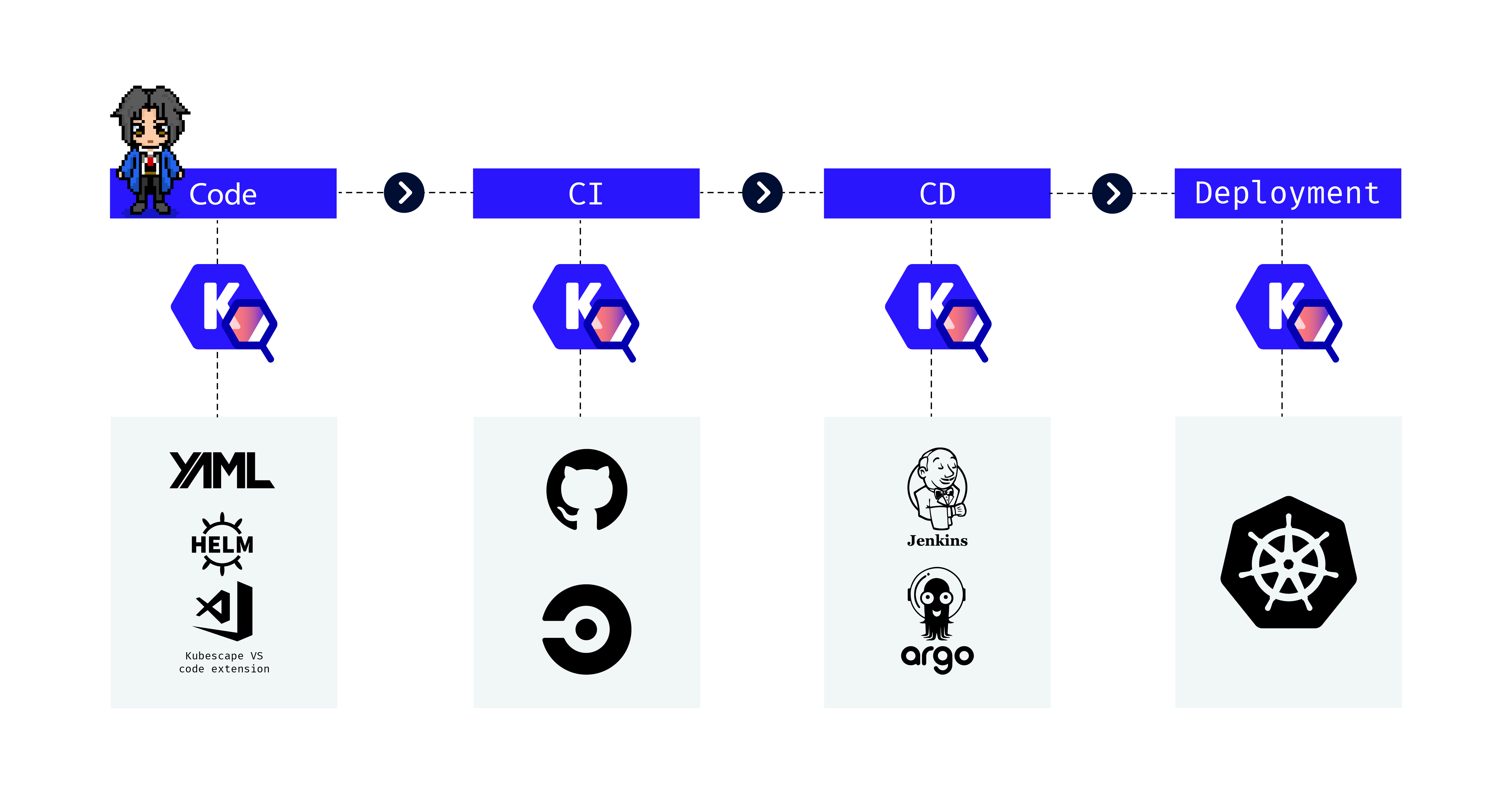
Kubescape is an open-source Kubernetes security platform that provides comprehensive security coverage, from left to right across the entire development and deployment lifecycle. It offers hardening, posture management, and runtime security capabilities to ensure robust protection for Kubernetes environments. It saves Kubernetes users and admins precious time, effort, and resources.
Kubescape scans clusters, YAML files, and Helm charts. It detects misconfigurations according to multiple frameworks (including NSA-CISA, MITRE ATT&CK® and the CIS Benchmark).
Kubescape was created by ARMO and is a Cloud Native Computing Foundation (CNCF) sandbox project.
Please star ⭐ the repo if you want us to continue developing and improving Kubescape! 😀
Kubescape has a command line tool that you can use to quickly get a report on the security posture of a Kubernetes cluster:
Experimenting with Kubescape is as easy as:
curl -s https://raw.githubusercontent.com/kubescape/kubescape/master/install.sh | /bin/bashThis script will automatically download the latest Kubescape CLI release and scan the Kubernetes cluster in your current kubectl context.
Learn more about:
Did you know you can use Kubescape in all these places?
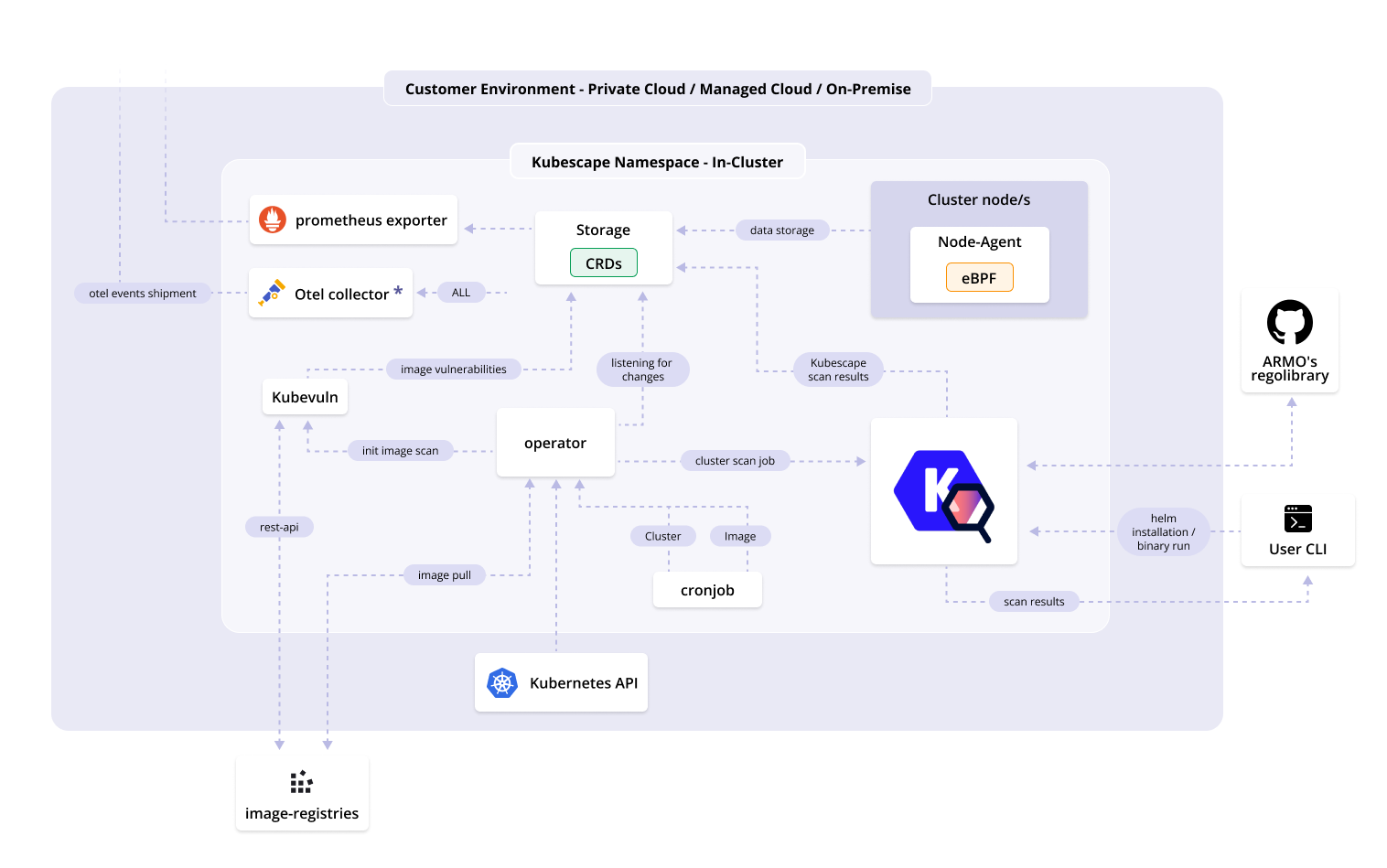
As well as a CLI, Kubescape provides an in-cluster mode, which is installed via a Helm chart. Kubescape in-cluster provides extensive features such as continuous scanning, image vulnerability scanning, runtime analysis, network policy generation, and more. Learn more about the Kubescape operator.
Kubescape can be used as a GitHub Action. This is a great way to integrate Kubescape into your CI/CD pipeline. You can find the Kubescape GitHub Action in the GitHub Action marketplace.
Kubescape uses Open Policy Agent to verify Kubernetes objects against a library of posture controls.
For image scanning, it uses Grype.
For image patching, it uses Copacetic.
For eBPF, it uses Inspektor Gadget
By default, CLI scan results are printed in a console-friendly manner, but they can be:
- exported to JSON, junit XML or SARIF
- rendered to HTML or PDF
- submitted to a cloud service
Kubescape is an open source project. We welcome your feedback and ideas for improvement. We are part of the CNCF community and are evolving Kubescape in sync with the security needs of Kubernetes users. To learn more about where Kubescape is heading, please check out our ROADMAP.
If you feel inspired to contribute to Kubescape, check out our CONTRIBUTING file to learn how. You can find the issues we are working on (triage to development) on the Kubescaping board
- Feel free to pick a task from the board or suggest a feature of your own.
- Open an issue on the board. We aim to respond to all issues within 48 hours.
- Join the CNCF Slack and then our users or developers channel.
The Kubescape project follows the CNCF Code of Conduct.
For more information about the Kubescape community, please visit COMMUNITY.
We would like to take this opportunity to thank all our contibutors to date.
Kubescape changes are tracked on the release page.
Copyright 2021-2024, the Kubescape Authors. All rights reserved. Kubescape is released under the Apache 2.0 license. See the LICENSE file for details.
Kubescape is a Cloud Native Computing Foundation (CNCF) sandbox project and was contributed by ARMO.