Azure Managed Identity tool - azmi - simplifies authentication to Azure resources inside Azure Linux VMs. Using VM with assigned Managed Identity you can easily authenticate against Azure services like Key Vault, Storage Account, etc.
# get token from Azure infrastructure
azmi gettoken
# list all blobs in a container
azmi listblobs --container $CONTAINER_URL
# download blob from a storage account container and save to a file
azmi getblob --blob $BLOB_URL --file $FILE
# download blobs from a storage account container and save them to folder
azmi getblobs --container $CONTAINER_URL --directory ./downloadBlobsHere
# upload file as a blob to storage account container
azmi setblob --file $FILE --container $CONTAINER_URL
# upload file by specifying blob url and identity
azmi setblob --file ~/info.txt --blob $CONTAINER_URL/myhostname/info.txt --identity 117dc05c-4d12-4ac2-b5f8-5e239dc8bc54
# fetch latest or specific version of a secret from Azure Key Vault
azmi getsecret --secret $SECRET_URL
azmi getsecret --secret $SECRET_URL/$VERSION
# fetch latest or specific version of a certificate from Azure Key Vault
azmi getcertificate --certificate $CERTIFICATE_URL
azmi getcertificate --certificate $CERTIFICATE_URL/$VERSIONFor more explanations, see detailed commands overview.
For more examples, see detailed examples page.
To download executable / package, use following commands:
- executable
curl https://azmideb.blob.core.windows.net/azmi-deb/azmi > ./azmi
chmod +x azmi
ls azmi -lP.S. Running azmi executable does not require root privilege.
- Debian package
curl https://azmideb.blob.core.windows.net/azmi-deb/azmi.deb > ./azmi.deb
ls azmi.deb -l
sudo dpkg -i ./azmi.deb- Windows
Tool azmi is built on top of cross-platform dotnet core.
Therefore, there are versions of azmi also for Windows.
Read more here.
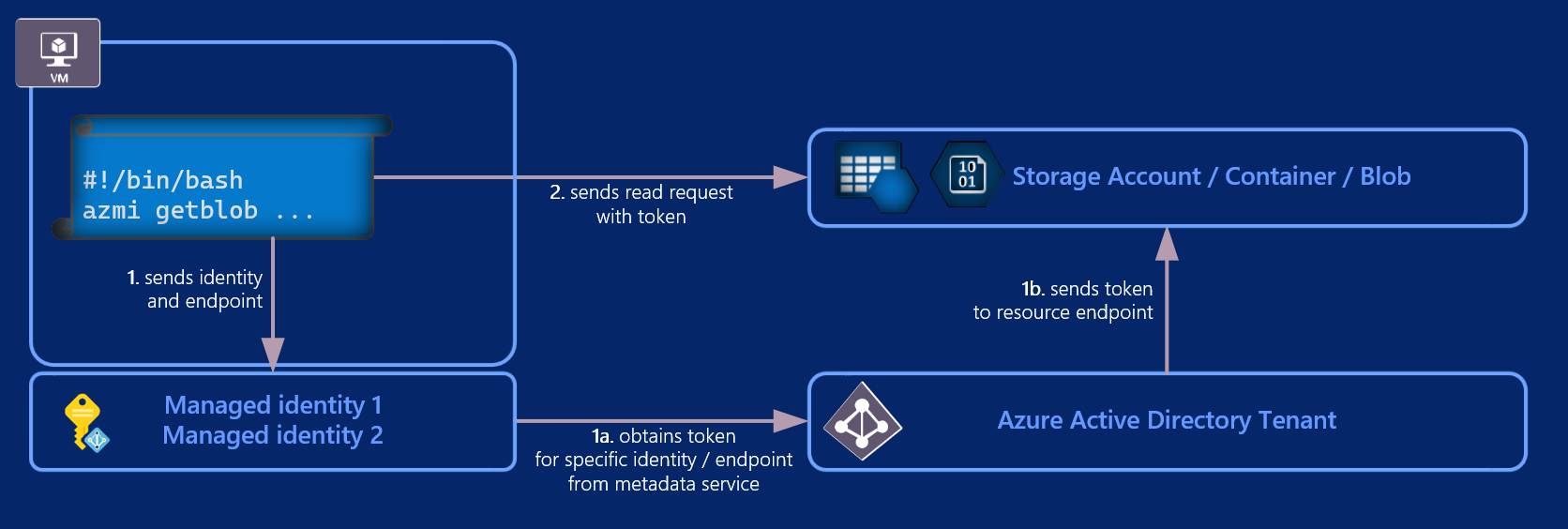
All Azure authentication is completely transparent for VM user or for a running script. Authentication is not attached for a user running the command, but actually to VM and its managed identity. There is no need to keep any secrets in the code or on the system, or to rotate and distribute them.
Azmi is utilizing managed identities to authenticate against Azure AD and obtain access token. This token is then sent to specified resource together with request for specific action (read/write data).
For other azmi commands (i.e. setblob) authentication works the same way. The only difference is with request being sent to target resource.
Azmi is not working across different AAD tenants.
Read more:
By default, azmi will display simple, Linux style errors. To discard the error, you can redirect the error stream to nul.
To get more verbose error output, use --verbose or -v switch in command.
Missing identity argument
If your VM has exactly one managed identity, you can omit --identity parameter. If it has more than one identity, you must specify it using the same argument.
No managed identity endpoint found
If you run azmi on non-Azure VM, you will get the error above.
Identity not found
If you used --identity argument, please verify if you used correct client / application ID