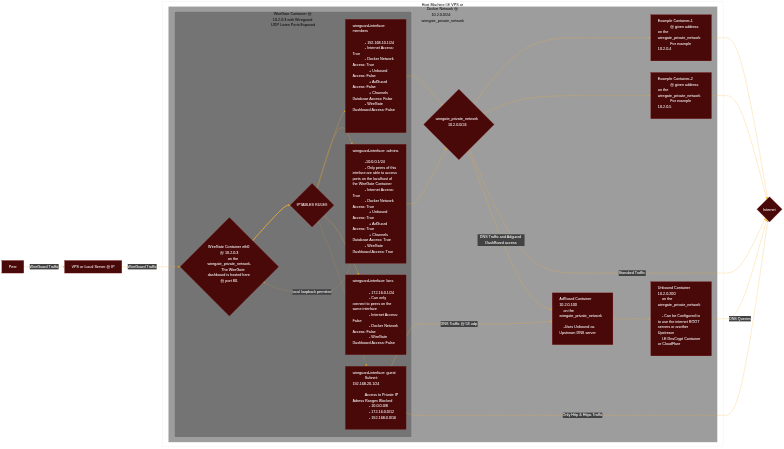
WireGate is a fully automated Docker Based intranet deployment that allows users to host web other applications on their existing server and be able to securely connect to said web applications without exposing them to the open internet. This is done by utilizing the WireGuard protocol in conjunction with Docker Networks and Containers. Hence applications hosted behind the WireGate private network need not expose any ports and can only be accessed via a WireGuard connection already registered to to an existing server interface on the deployed WireGate instance. Secure by Design, the WireGuard Dashboard & other services are only accessible on first deployment via the master configuration that is generated at install and encrypted after being outputted to the console. Wiregate also acts as a ISP DNS query logging bypass. Wiregate by default is configured to have minimal logging.
| Project | Easy Setup | Production Ready | Client Firewall Rules | GUI | DNS Filtering | Multi Interface | Built in Security |
|---|---|---|---|---|---|---|---|
| Wiregate | ✅ | ✅ | ✅ | ✅ | ✅ | ✅ | ✅ |
| Wirehole | ✅ | ❌ | ❌ | ❌ | ✅ | ❌ | ❌ |
| WG-Easy | ✅ | ❌ | ❌ | ✅ | ❌ | ❌ | ❌ |
Wiregate is configured with 4 zones that peers can be added to. The zone a peer belongs to dictates the network access permissions of said peer. Wiregate supports the x86-64 and arm64 CPU architectures . Tested on Ubuntu LTS & Debian 12
| Zone | Internet Access | WireGuard Dashboard Access | Docker Network Access | Peer to Peer Access |
|---|---|---|---|---|
| Admin | ✅ | ✅ | ✅ | ✅ |
| Members | ✅ | ❌ | ✅ | ✅ |
| LAN Users | ❌ | ❌ | ❌ | ✅ |
| Guest | ✅ | ❌ | ❌ | ❌ |
| Use Cases | Description |
|---|---|
| Authentication | Access to service can be limited by requiring a WireGuard client config as well as a registered account on said service |
| Secure Self Hosted VPN | Self Explanatory |
| Adblock & DNS Filtering | Self Explanatory |
| Local Network Filter Proxy | By using a raspberry Pi ruining on the same local network your able to pre proxy all network traffic through your desired device using adguard/pihole & unbound. The unbound config will need to be modified to use an upstream DNS server for this to work, unless a cloud based Wiregate Node is used in conjunction with the Raspeberry Pi. |
| Secure Invite Only Messaging Service | This is done via channels and allows all members of the Wiregate Private Network to communicate under the same secure umbrella. |
| VPN Splitter | Wiregate can be used to extend the number of clients allowed by any VPN service provider by using your Wiregate machine as a hub |
| Container | Vulnerability Status | Know Image CVE's | Tag |
|---|---|---|---|
| WG-Dashboard | ✅ None | 0 | noxcis/wg-dashboard:mantis-shrimp |
| Pihole | ❌ Vulnerable | 30 | pihole/pihole:latest |
| AdGuard | ✅ None | 0 | adguard/adguardhome:latest |
| Channels | ✅ None | 0 | noxcis/channels:orca |
| Unbound | ✅ None | 0 | klutchell/unbound:latest |
| Postgres | ✅ None | 0 | postgres:13-alpine |
All Wiregate supporting configurations can be found in the Global Configs Folder.
Give a ⭐ if this project helped you! If your feeling generous? Cashapp: $N0XCIS
Run these commands to install Wiregate.
#!/bin/bash
git clone https://github.com/NOXCIS/Wiregate.git
cd Wiregate
chmod +x install.sh
sudo ./install.sh
- ./install.sh -Starts the setup script menu.
For Pihole Setup
- ./install.sh pi-exp - Starts the setup script and automatically configures the compose file with following environment variables:.
For AdGuard Setup
- ./install.sh pi-adv - Starts the setup script and automatically configures the compose file with following environment variables.
For Pihole Setup
- ./install.sh pi-adv - Start the setup script allowing the user to manually configure the compose file environment variables.
For AdGuard Setup
- ./install.sh ad-adv - Start the setup script allowing the user to manually configure the compose file environment variables.
For AdGuard Setup
- ./install.sh ad-predef - Set your Desired Environment Variables in the environment files located in Global-Configs/ENV-FILES
For Pihole Setup
- ./install.sh pi-predef - Set your Desired Environment Variables in the environment files located in Global-Configs/ENV-FILES
- ./install.sh fresh - Reset WireGuard Dashboard
The installer will output a master client config similar to the one below. The master key file is automatically encrypted after the final output. To decrypt the Master Key use the Master Key decryption key.
While connected to WireGate, navigate to http://channels.msg/
WireGate has a updated version of Channels messenger by dzionek built in, to felicitate secure encrypted communication via the WireGate network.
Flask web-application where you can create own channels, manage them, and chat with your friends/colleagues.
Inspired by the Project 2 of Harvard's CS50’s Web Programming with Python and JavaScript.
While connected to WireGate, navigate to http://wire.gate/
The password & username are randomly generated and provided in the final output if not set manually.
WireGate uses a modified version of WG-Dashboard by Donald Zou, with the following modifications.
- Dockerized (For isolation from the main host and easy deployment)
- User Interface Modification (for readability)
- Auto Generate and Start Wireguard Configs
- Added Postup and Postdown Firewall Rules for generated wireguard configs (ZONES)
- Flask App Secret Key passed as shell generated environment variable (because flask-key relied on the website URL to be generated)
- Username & Password passed as shell generated environment variable (because of hard coded admin defaults)
- UWSGI instead of Gunicorn
- Refactored Code based (For UWSGI compatibility)
- Bcrypt instead of SHA256 (because of hard coded password)
- Removed Update checks to Donald Zou WG-Dashboard repo (because of cybersecurity paranoia)
While connected to WireGate, navigate to http://ad.guard/
The password & username are randomly generated and provided in the final output if not set manually.
While connected to WireGate, navigate to http://pi.hole/
The password is randomly generated and provided in the final output if not set manually.
Custom unbound confurations can be done by modifying the file unbound.conf located in the Unbound folder inside Global-Configs folder before stack deployment.
If you choose to not use Cloudflare any reason you are able to modify the upstream DNS provider in unbound.conf.
Search for forward-zone and modify the IP addresses for your chosen DNS provider.
NOTE: The anything after
#is a comment on the line.
What this means is it is just there to tell you which DNS provider you put there. It is for you to be able to reference later. I recommend updating this if you change your DNS provider from the default values.
forward-zone:
name: "."
forward-addr: 1.1.1.1@853#cloudflare-dns.com
forward-addr: 1.0.0.1@853#cloudflare-dns.com
forward-addr: 2606:4700:4700::1111@853#cloudflare-dns.com
forward-addr: 2606:4700:4700::1001@853#cloudflare-dns.com
forward-tls-upstream: yes
The code in this repo is influenced by IAmStoxe's WireGate project.
WireGate lacked the ability to easily generate new users and has recenlty stopped working due to updates to the parent project of Unbound-Docker, Unbound-Docker by MatthewVance .
Therefore with the help of klutchell's unbound-docker Docker image & donaldzou's WGDashboard Dockerized by Noxcis, WireGate was recreated as WireGate.
However, the upstream projects and their authors most certainly also deserve credit for making this all possible.
-
AdGuard -AdGuard
-
Pihole. - Pihole
-
NLnetLabs. -Unbound
-
Kyle Harding. -Distroless Unbound Docker Image
-
Donald Zou. -WG Dashboard (WireGuard UI)
-
Bartosz Dzionek -Channels Messenger