A Burp Suite extension to apply the current Google Two-Tactor Authentication (2FA) code to relevant/selected requests.
This Burp Suite extension turns Burp into a Google Authenticator client. The current Google Two-Factor Authentication (2FA) code is automatically computed from a given shared secret and applied to bespoke location(s) in relevant requests in real-time.
Further information on two-factor authentication is available at the following links:
- https://en.wikipedia.org/wiki/Google_Authenticator
- https://tools.ietf.org/html/rfc4226
- https://tools.ietf.org/html/rfc6238
Further information about Burp session handling rules is available at the following link:
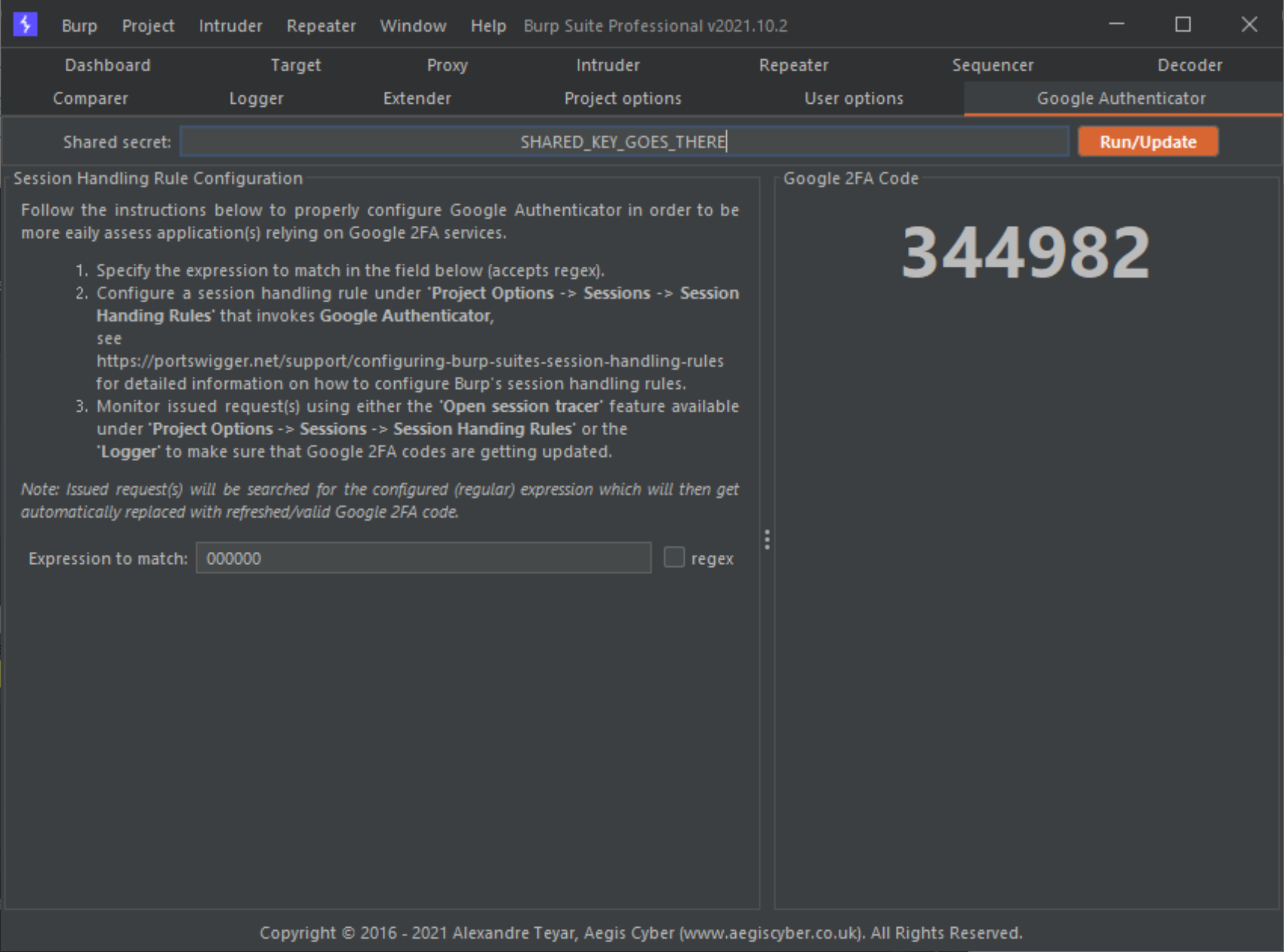
- Top panel: Secret shared key, used to generate the
Google 2FAcode using theTime-based One-Time Password (TOTP)algorithm specified inRFC4226andRFC6238. - Left panel: Regular expression for the session handling rule to match and replace with the current
Google 2FAcode. - Right panel:
Google 2FAgenerated code in real-time.
We have been commissioned to perform a web application penetration test on www.foobar.com. This web application implements a login form incorporating Google 2FA for an additional layer of defence (prevents automated attacks such as brute forcing attacks). The client provided us with testing credentials along with a link to set up the Google Authenticator mobile application to allow for authenticated testing.
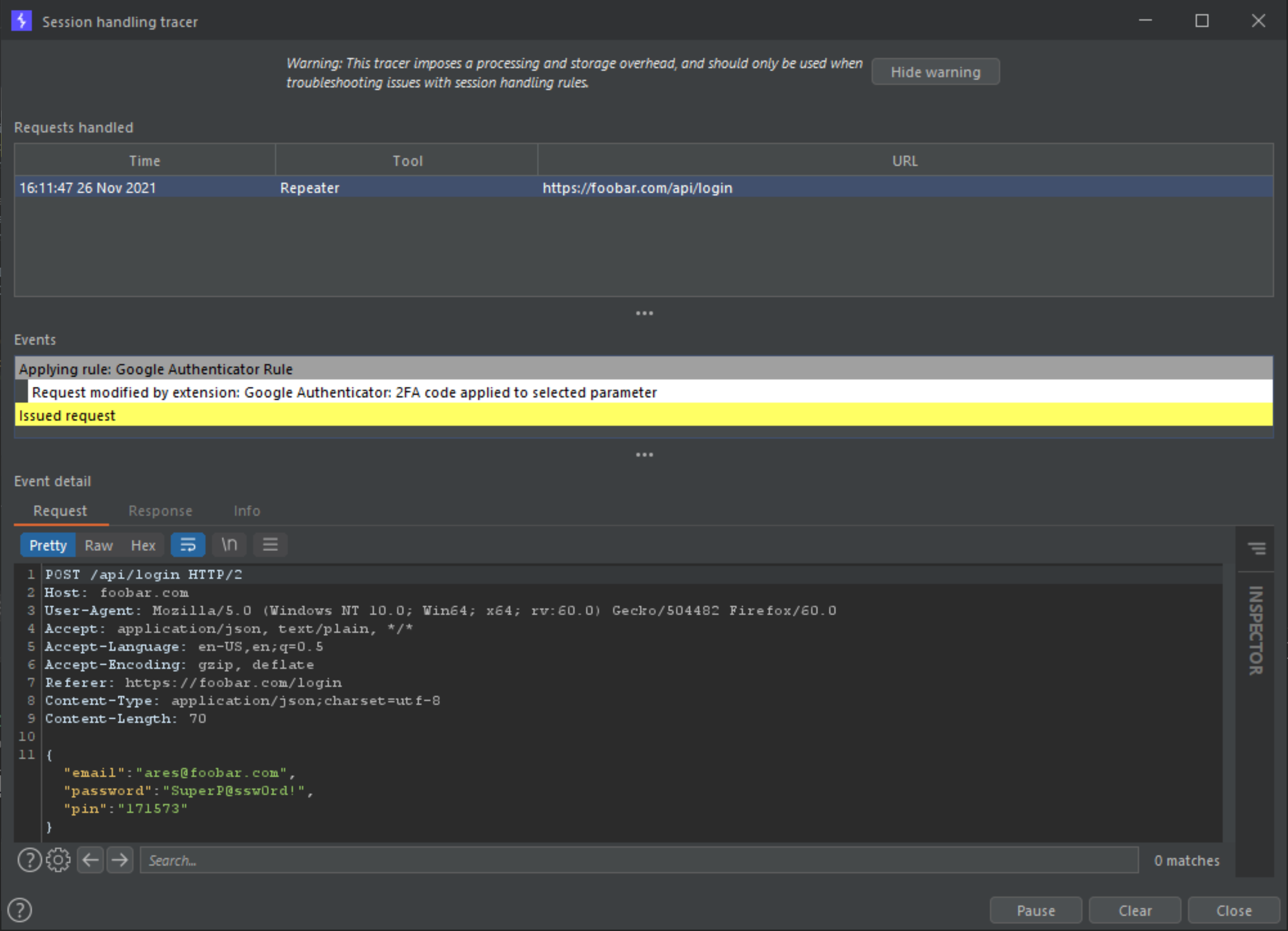
A login is performed using the following request (in this example, the pin JSON parameter is the Google 2FA).
POST /api/login HTTP/1.1
Host: foobar.com
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:60.0) Gecko/504482 Firefox/60.0
Accept: application/json, text/plain, */*
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Referer: https://foobar.com/login
Content-Type: application/json;charset=utf-8
Content-Length: 74
Connection: close
{"email":"[email protected]","password":"SuperP@ssw0rd!","pin":"504482"}
Following the aforementioned link, we obtain the shared secret (42TCJUDP94W27YR3) that the Time-based One-time Password Algorithm (TOTP) uses to generate the Google 2FA codes.
During testing, we observed that the application is being protected by a Web Application Firewall (WAF), logging our test user out each time a malicious payload is detected or if too many requests are sent in a short period of time. This configuration makes it virtually impossible to take advantage of the Burp Suite automated scan capabilities.
-
Input relevant parameter(s) into the Google Authenticator interface:
- Shared secret:
42TCJUDP94W27YR3 - Regular expression:
(?<![\w\d])\d{6,8}(?![\w\d])
- Shared secret:
-
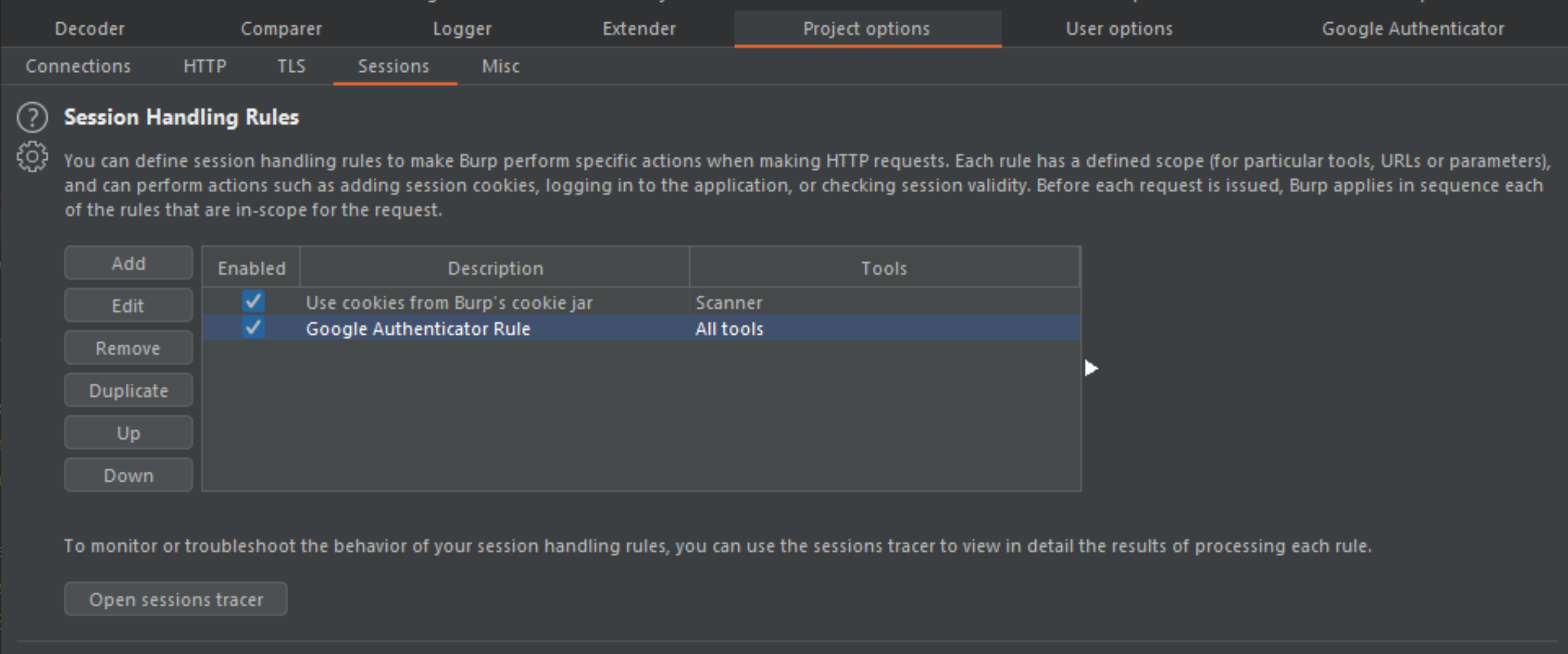
Project options->Sessions->Session Handling Rules->AddaSession Handling Rule->Invoke a Burp extension->Google Authenticator: 2FA code applied to selected parameter. -
Configure the relevant scope for the registered session handling rule.
-
Watch/monitor relevant request(s) getting updated with the valid/refreshed
Google 2FAcode generated byGoogle Authenticatorusing eitherProject options->Sessions->Session Handling Rules->Open session traceror theLoggertab.
- Use the regex
(?<![\w\d])\d{6,8}(?![\w\d])for optimal results asGoogle 2FAcodes are made up of 6 to 8 digits according to the relevant RFCs. - Restrict the scope of the session handling rule down to the request(s) containing the
Google 2FAcode only.
-
Install and configure Gradle.
-
Download this repository.
git clone https://github.com/aress31/googleauthenticator cd .\googleauthenticator\
-
Create the standalone
jar:gradle fatJar
In Burp Suite, under the Extender/Options tab, click on the Add button and load the googleauthenticator-all jar file located in the .\build\libs folder.
Alternatively, you can now directly install/load this extension from the BApp Store.
Note: The version distributed on the BApp Store might be behind the version available on this repository.
- Add additional features, maybe support for
Microsoft Authenticator. - Beautify the
GUI. - Implement a
JTableto view modified requests in real-time. - Leverage the
IHttpListenerinterface and rework the filers in order to provide users with more ways of processing request(s). - Source code optimisation.
If you want to support this project and appreciate the time invested in developping, maintening and extending it; consider donating toward my next cup of coffee. ☕
It is easy, all you got to do is press the Sponsor button at the top of this page or alternatively click this link. 💸
Found a bug? I would love to squash it! 🐛
Please report all issues on the GitHub issues tracker.
You would like to contribute to better this project? 🤩
Please submit all PRs on the GitHub pull requests tracker.
See LICENSE.