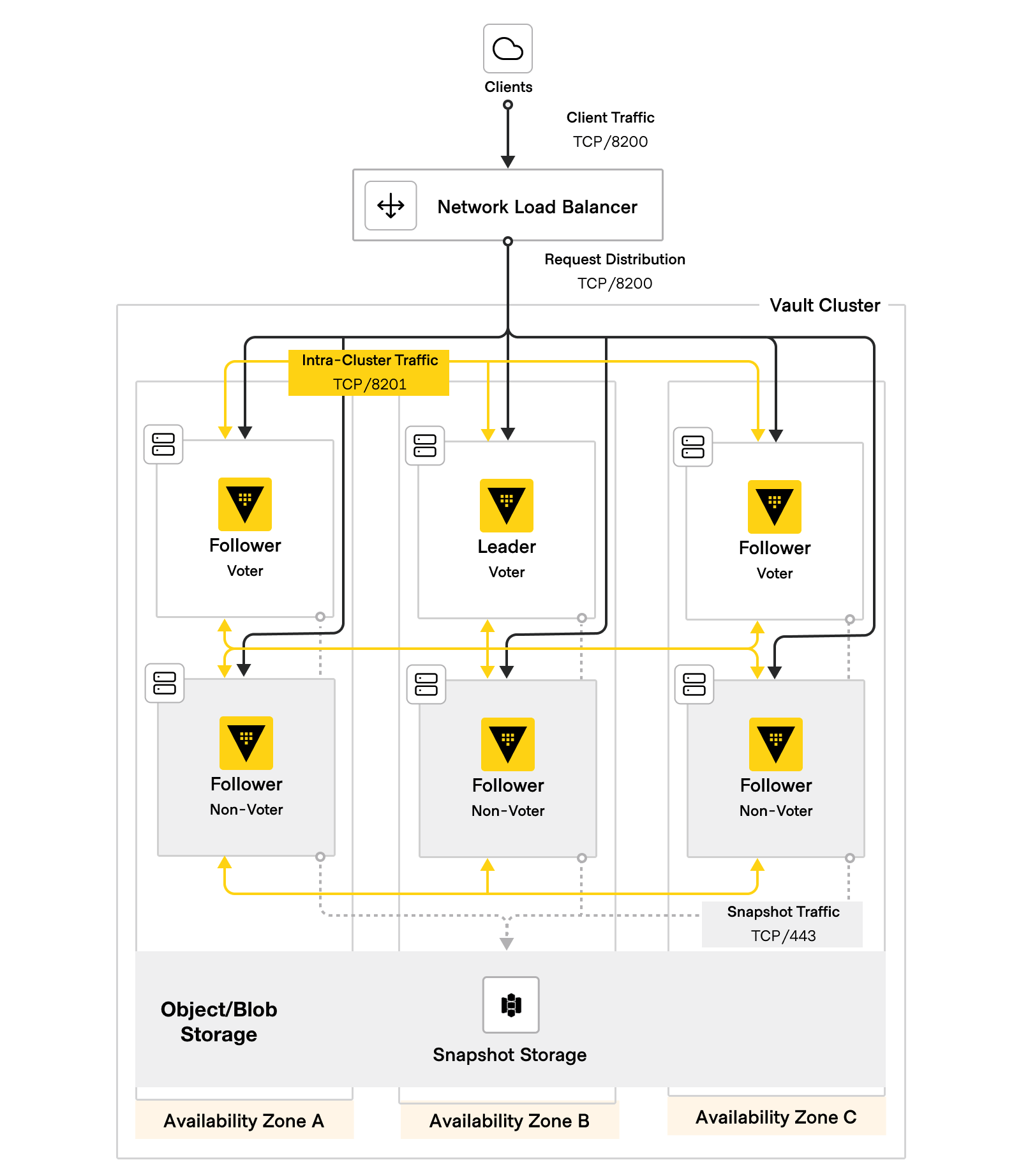
Terraform module aligned with HashiCorp Validated Designs (HVD) to deploy Vault Enterprise on Google Cloud Platform (GCP) using Compute Engine instances. This module deploys Vault Enterprise with integrated storage.
This module requires the following to already be in place in GCP:
- A Google Cloud project with the following:
- A VPC network
- A Cloud NAT gateway
- Secret Manager API enabled
- Cloud Key Management Service API enabled with a Key Ring and Key created (if using auto-unseal)
- Cloud Resource Manager API enabled
- A principal with the Compute Admin role or equivalent
It is recommended to authenticate to GCP via the Google Cloud SDK tool. If running Terraform non-interactively, you can use a Google Cloud Service Account.
With the SDK installed locally, authenticate to GCP by running gcloud auth application-default login. You can then set the project for the module by setting the GOOGLE_PROJECT environment variable.
Create a dedicated GCP service account in the target project and download the key file. You can then set the GOOGLE_APPLICATION_CREDENTIALS environment variable to be used by Terraform along with the GOOGLE_PROJECT variable to set the appropriate project.
Upon first deployment, Vault servers will auto-join and form a fresh cluster. The cluster will be in an uninitialized, sealed state. An operator must then connect to the cluster to initialize Vault. If using Shamir seal, the operator must manually unseal each node. If auto-unseal is used via Google KMS, the Vault nodes will automatically unseal upon initialization.
Example deployment scenarios can be found in the examples directory of this repo here. These examples cover multiple capabilities of the module and are meant to serve as a starting point for operators.
This module by default deploys on ubuntu-os-cloud this can be changed by updating the following;
var.compute_image_familyvar.compute_image_project
or by creating packer image and providing the var.packer_image see the Packer for additional detail.
There is a helper doc for tls cert generation should you need it TLS.
This module supports the deployment of Google's TCP Layer 4 load balancer to sit in front of the Vault cluster. The load balancer can be external (public IP) or internal (private IP) and is configured to use Vault's sys/health API endpoint to determine health status of Vault to ensure clients are always directed to a healthy instance when possible.
The variable load_balancing_scheme is used to dictate the type of load balancer that should be used and can be set as one of the following values:
INTERNAL- Load balancer should receive an IP address on a private subnetEXTERNAL- Load balancer should receive a public IP addressNONE- No load balancer should be provisioned
This module supports both the Shamir and Auto Unseal (via Google Cloud KMS) seal mechanism. By default, the module will assume the Shamir method should be used. In the event Auto Unseal should be used, set the variable vault_seal_type to gcp_kms and set the following two additional variables:
gcp_kms_key_ring- The name of the cryptographic key ring to usegcp_kms_crypto_key- The name of the cryptographic key to use
See KMS docs for helper material on producing the required KMS inputs.
| Name | Version |
|---|---|
| ~> 5.33 |
| Name | Version |
|---|---|
| 5.34.0 |
No modules.
| Name | Type |
|---|---|
| google_compute_firewall.allow_https | resource |
| google_compute_firewall.allow_iap | resource |
| google_compute_firewall.allow_vault_health_checks | resource |
| google_compute_forwarding_rule.vault_fr | resource |
| google_compute_health_check.vault_auto_healing | resource |
| google_compute_instance_template.vault | resource |
| google_compute_region_backend_service.vault_bs | resource |
| google_compute_region_health_check.vault_hc | resource |
| google_compute_region_instance_group_manager.vault | resource |
| google_dns_record_set.vault | resource |
| google_project_iam_member.vault_iam | resource |
| google_project_iam_member.vault_iam_kms | resource |
| google_service_account.vault_sa | resource |
| google_client_config.current | data source |
| google_compute_network.network | data source |
| google_compute_subnetwork.subnetwork | data source |
| google_compute_zones.available | data source |
| google_dns_managed_zone.vault | data source |
| google_netblock_ip_ranges.legacy | data source |
| google_netblock_ip_ranges.new | data source |
| Name | Description | Type | Default | Required |
|---|---|---|---|---|
| application_prefix | (optional) The prefix to give to cloud entities | string |
"vault" |
no |
| auto_join_tag | (optional) A list of a tag which will be used by Vault to join other nodes to the cluster. If left blank, the module will use the first entry in tags |
list(string) |
null |
no |
| cidr_ingress_https_allow | CIDR ranges to allow HTTPS traffic inbound to Vault instance(s). | list(string) |
[ |
no |
| cloud_dns_managed_zone | Zone name to create TFE Cloud DNS record in if create_cloud_dns_record is set to true. |
string |
null |
no |
| common_labels | (optional) Common labels to apply to GCP resources. | map(string) |
{} |
no |
| compute_image_family | (optional) The family name of the image, https://cloud.google.com/compute/docs/images/os-details,defaults to Ubuntu |
string |
"ubuntu-2204-lts" |
no |
| compute_image_project | (optional) The project name of the image, https://cloud.google.com/compute/docs/images/os-details, defaults to Ubuntu |
string |
"ubuntu-os-cloud" |
no |
| create_cloud_dns_record | Boolean to create Google Cloud DNS record for vault_leader_tls_servername resolving to load balancer IP. cloud_dns_managed_zone is required when true. |
bool |
false |
no |
| debug | [Optional bool] Enable additional outputs available module outputs for debug purposes. | bool |
false |
no |
| disk_size | (optional) The disk size (GB) to use to create the disk | number |
100 |
no |
| disk_type | (optional) The disk type to use to create the disk | string |
"pd-ssd" |
no |
| enable_auto_healing | (optional) Enable auto-healing on the Instance Group | bool |
false |
no |
| enable_iap | (Optional bool) Enable https://cloud.google.com/iap/docs/using-tcp-forwarding#console, defaults to true. |
bool |
true |
no |
| gcp_kms_crypto_key | (optional) The name of the KMS crypto key | string |
"vault-key" |
no |
| gcp_kms_key_ring | (optional) The name of the KMS key ring | string |
"vault" |
no |
| gcp_kms_project | (optional) The project the KMS key ring is in. Can be left blank if project is the same as provider | string |
null |
no |
| gcp_kms_region | (optional) The region the KMS key ring is in. Can be left blank if region is the same as main region | string |
null |
no |
| google_service_account_iam_roles | (optional) List of IAM roles to give to the Vault service account | list(string) |
[ |
no |
| health_check_interval | (optional) How often, in seconds, to send a health check | number |
30 |
no |
| health_timeout | (optional) How long, in seconds, to wait before claiming failure | number |
15 |
no |
| initial_auto_healing_delay | (optional) The time, in seconds, that the managed instance group waits before it applies autohealing policies | number |
1200 |
no |
| load_balancing_scheme | (optional) Type of load balancer to use (INTERNAL, EXTERNAL, or NONE) | string |
"INTERNAL" |
no |
| machine_type | (optional) The machine type to use for the Vault nodes | string |
"e2-standard-2" |
no |
| metadata | (optional) Metadata to add to the Compute Instance template | map(string) |
null |
no |
| network | (optional) The VPC network to host the cluster in | string |
"default" |
no |
| network_project_id | (optional) The project that the VPC network lives in. Can be left blank if network is in the same project as provider | string |
null |
no |
| network_region | (optional) The region that the VPC network lives in. Can be left blank if network is in the same region as provider | string |
null |
no |
| node_count | (optional) The number of nodes to create in the pool | number |
6 |
no |
| packer_image | (optional) The packer image to use | string |
null |
no |
| project_id | (required) The project ID to host the cluster in (required) | string |
n/a | yes |
| region | (optional) The region to host the cluster in | string |
"us-central1" |
no |
| skip_install_tools | (optional) Skips installing required packages (unzip, jq, wget) | bool |
false |
no |
| subnetwork | (optional) The subnet in the VPC network to host the cluster in | string |
"default" |
no |
| tags | (optional) A list containing tags to assign to all resources | list(string) |
[ |
no |
| vault_api_port | (optional) The port the Vault API will listen on | string |
"8200" |
no |
| vault_backend_storage | (optional) The backend storage type to use, defaults to consul | string |
"integrated" |
no |
| vault_bin_directory | (optional) The bin directory for the Vault binary | string |
"/usr/bin" |
no |
| vault_ca_bundle_secret | (required) The name of the CA bundle secret in Secret Manager | string |
n/a | yes |
| vault_cluster_port | (optional) The port the Vault cluster port will listen on | string |
"8201" |
no |
| vault_data_directory | (optional) The data directory for the Vault raft data | string |
"/opt/vault" |
no |
| vault_disable_mlock | (optional) Disable the server from executing the mlock syscall |
bool |
true |
no |
| vault_enable_ui | (optional) Enable the Vault UI | bool |
true |
no |
| vault_health_endpoints | (optional) The status codes to return when querying Vault's sys/health endpoint | map(string) |
{ |
no |
| vault_home_directory | (optional) The home directory for the Vault user | string |
"/etc/vault.d" |
no |
| vault_leader_tls_servername | (optional) TLS servername to use when trying to connect to the Raft cluster with HTTPS | string |
null |
no |
| vault_license_secret | (optional) The ARN of the license secret in AWS Secrets Manager | string |
null |
no |
| vault_private_key_secret | (required) The name of the signed certificate's private key secret in Secret Manager | string |
n/a | yes |
| vault_seal_type | (optional) The seal type to use for Vault | string |
"shamir" |
no |
| vault_signed_cert_secret | (required) The name of the signed certificate secret in Secret Manager | string |
n/a | yes |
| vault_systemd_directory | (optional) The directory for the systemd unit | string |
"/lib/systemd/system" |
no |
| vault_tls_disable_client_certs | (optional) Disable client authentication for the Vault listener | bool |
true |
no |
| vault_tls_require_and_verify_client_cert | (optional) Require a client to present a client certificate that validates against system CAs | bool |
false |
no |
| vault_user_data_template | (optional) Alternative template file to provide for instance template metadata script. place the file in your local ./templates folder no path required |
string |
"google_vault_metadata.sh.tpl" |
no |
| vault_version | (optional) The version of Vault to use | string |
"1.16.0+ent" |
no |
| Name | Description |
|---|---|
| loadbalancer_ip | The external ip address of the forwarding rule. |
| user_data_template | n/a |
| vault_data | Vault utility output for first Vault connection and init. |