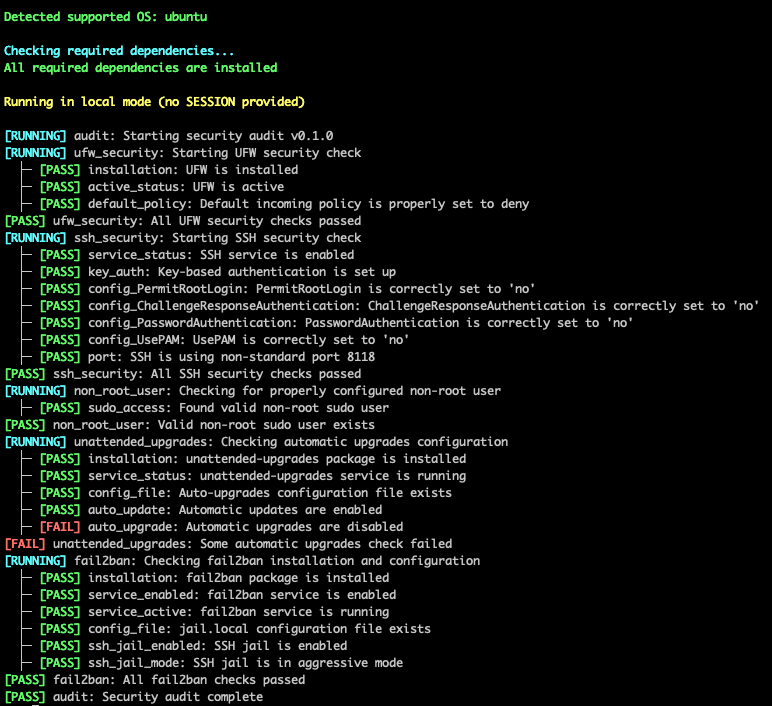
Scans your server to find common issues like weak SSH settings, missing firewalls, lack of updates, and more. Perfect for getting your VPS ready for production.
- Download the script
$ curl -O https://raw.githubusercontent.com/healthyhost/audit-vps-script/main/audit.sh- Make it executable:
$ chmod +x audit.sh- Run the security audit:
$ sudo ./audit.shVisit https://auditpvps.com to run checks through our web app for free and render the results in your browser.
- Ubuntu/Debian-based distributions
jq(temporary dependency, planned for removal)- Root or sudo privileges
The scripts perform the following checks:
- Firewall (UFW)
- Check if UFW is installed
- Check if UFW is enabled
- Check if incoming traffic is blocked
- SSH
- Check if SSH is enabled
- Check if key-based authentication is enabled
- Check if root login is disabled
- Check if password authentication is disabled
- Check if SSH is listening on port 22
- Root
- Check if non-root sudo user exists
- System updates
- Check if automatic system updates are enabled
- Check if automatic system upgrades are enabled
- Fail2Ban
- Check if Fail2ban is installed
- Check if Fail2ban is enabled
- Check if Fail2ban is configured correctly
- Check if Fail2ban SSH is enabled
- Check if Fail2ban SSH is in aggressive mode
We welcome contributions! If you have any suggestions or improvements, please open an issue or submit a pull request.
MIT
- Support for additional Linux distributions:
- RHEL/CentOS
- Fedora
- Alpine Linux
- Removal of
jqdependency - Warning states (WARN) for non-critical security recommendations
- Code refactoring to improve readability