This project is to clone data to either gen1 or gen2 devices.
- Clone my apartment key fob - works like a charm :)
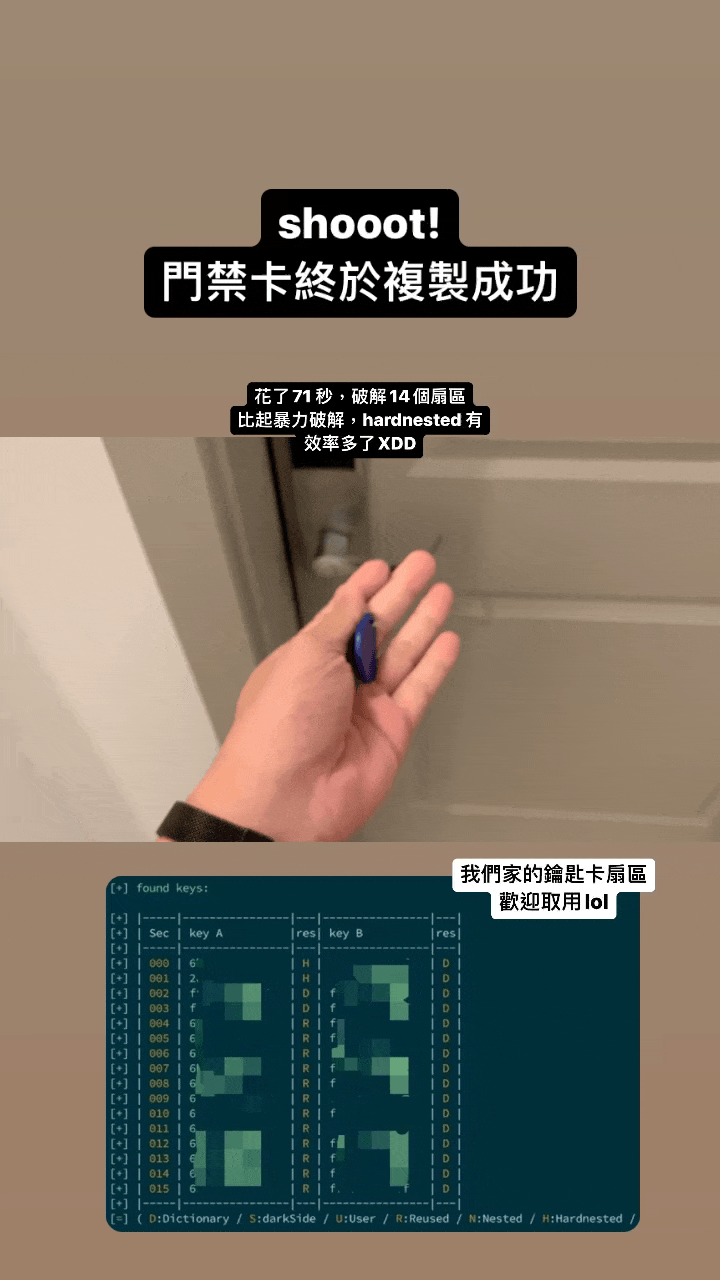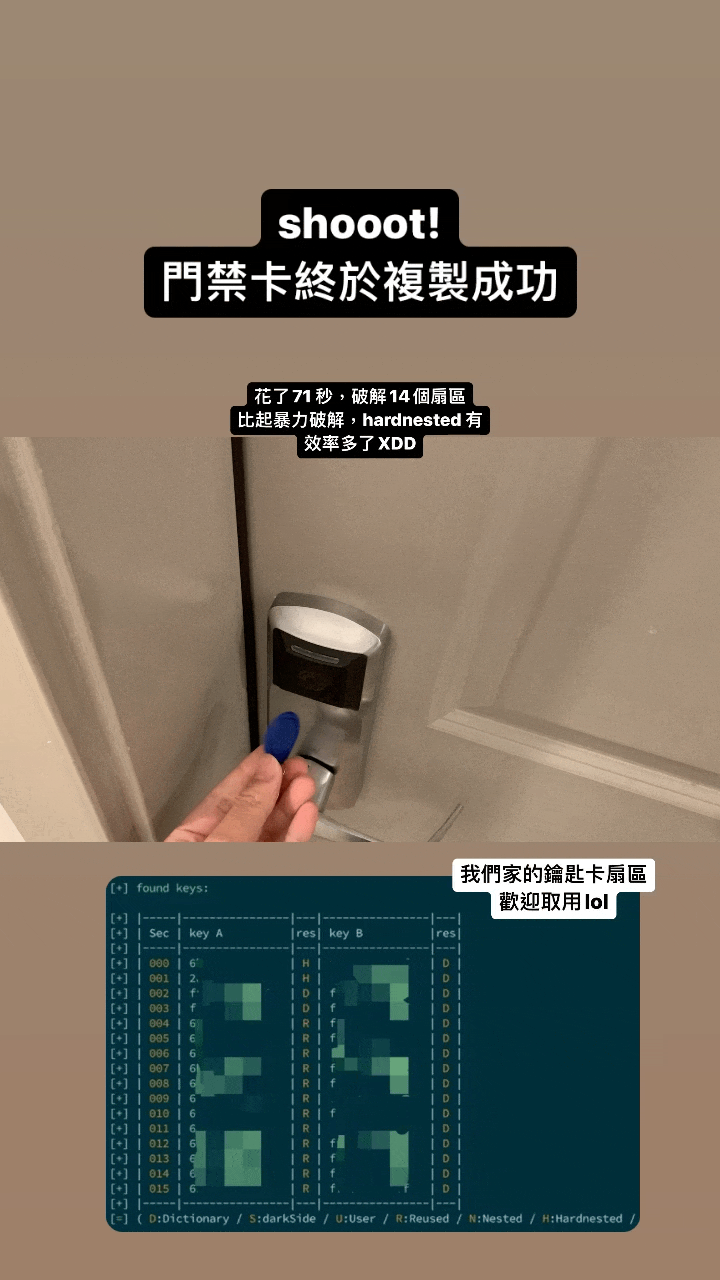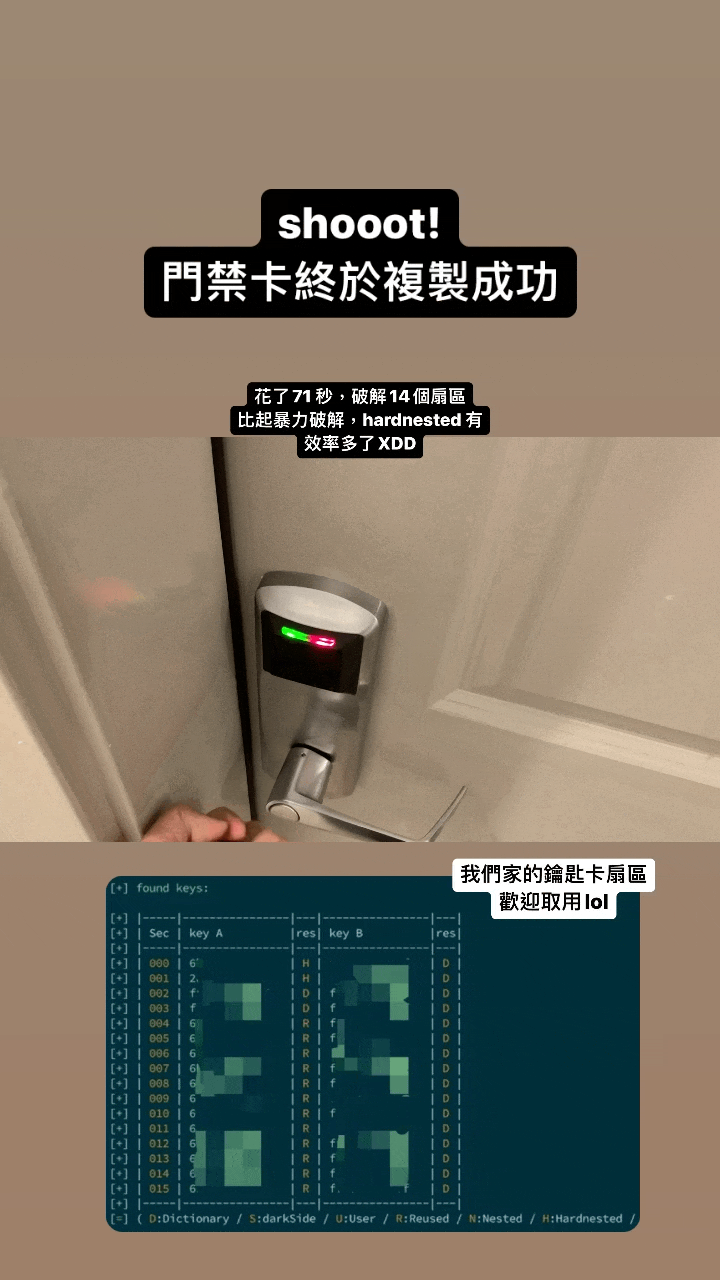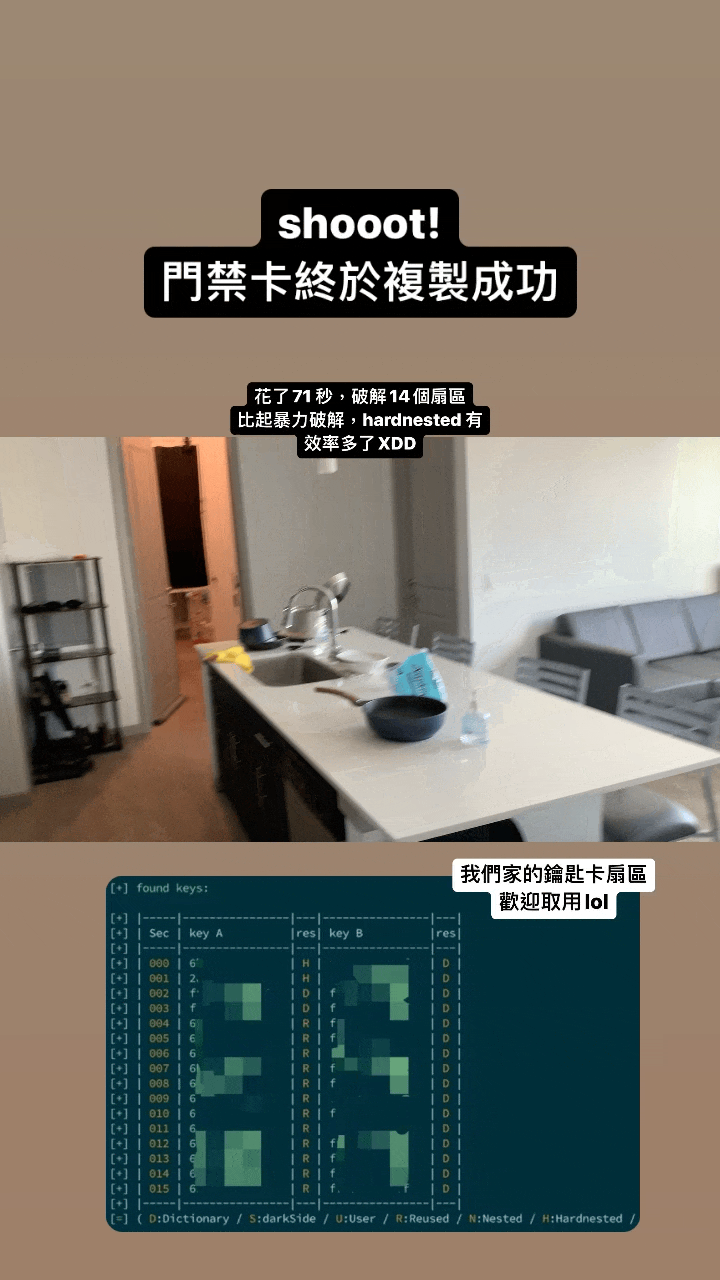
- Relay the key fob to another device - works like a charm :)

- Cards I've test to work - spent pretty much of time and effort, but it's a fun adventure

The primary goal of this project is to facilitate the efficient cloning of data onto gen1 or gen2 devices. It offers a systematic approach that begins with differentiating the device generation, dumping necessary data, and executing appropriate commands. The project ensures that users can seamlessly clone their key fobs and offers solutions for common hitches in the process.
# In pm3, Use this command to check if it's a gen1 card
# This could be a gen2 card if cgetblk command is not working
[usb] pm3 --> hf mf cgetblk --blk 0
[#] wupC1 error
[!!] 🚨 Can't read block. error=-1
# Double check with the following command, if it works it's a gen2 card:
[usb] pm3 --> hf mf rdbl --blk 0 -k FFFFFFFFFFFF
- Dump the file from the the key fob you want to clone by pm3
- Run this command
- the filename:
/hf-mf-XXXXXXXX-dump.binis the dump binary from pm3 using commandhf mf dump XXXXXXXXis the uid you can get it when dumping data with pm3
- the filename:
- If key A is all
FFFFFFFFFFFF- Create the file with filename:
dump_data-> we can get it by dumping from the key fob you want to clone withhf mf dump. And the format should be similar as this example - Run this command
- connect to pm3 before running this command
- Create the file with filename:
- If key A is random in each sector, follow the instructions below
- The filename:
find_keys-> can get it by pm3 with commandhf mf autopwn- the
find_keysformat should be similar as this example. We are using key A to read and write the data to specific block- e.g key A at
Sec 000is to unlockblock0-3and so on - command examples:
- READ:
hf mf rdbl --blk 0 -k ffffffffffff~hf mf rdbl --blk 3 -k ffffffffffff - WRITE:
hf mf wrbl --blk 0 -k ffffffffffff -d 0102030405~hf mf wrbl --blk 3 -k ffffffffffff -d 0102030405
- READ:
- e.g key A at
- the
- The filename:
dump_data-> we can get it by dumping from the key fob you want to clone withhf mf dump. And the format should be similar as this example
How to use? Code base
- Connect with pm3
parse_dump.sh- parse the data dumped from pm3
- Input:
dump_data, output:parse_dump
parse_keys.sh- parse the key dumped from pm3
- Remember to input the idential format of find_keys mentioned here
- Input:
find_keys, outpus:parsed_keys
- parse the key dumped from pm3
gen2card_clone_key_fob.sh- Clone the key fob
- Input:
dump_dataandparsed_keys, no output
If the key fob is not able to unlock the door (and the reader shows yellow light), the block0 is probably wrong (SAK)
- Mediation: change from
SAK 88toSAK 08- Change from
XXXXXXXXXX88XXXXXXXXXXXXXXXXXXXXtoXXXXXXXXXX08XXXXXXXXXXXXXXXXXXXXand write it with commands:hf mf wrbl --blk 0 -k ffffffffffff -d XXXXXXXXXX08XXXXXXXXXXXXXXXXXXXX
- Change from
