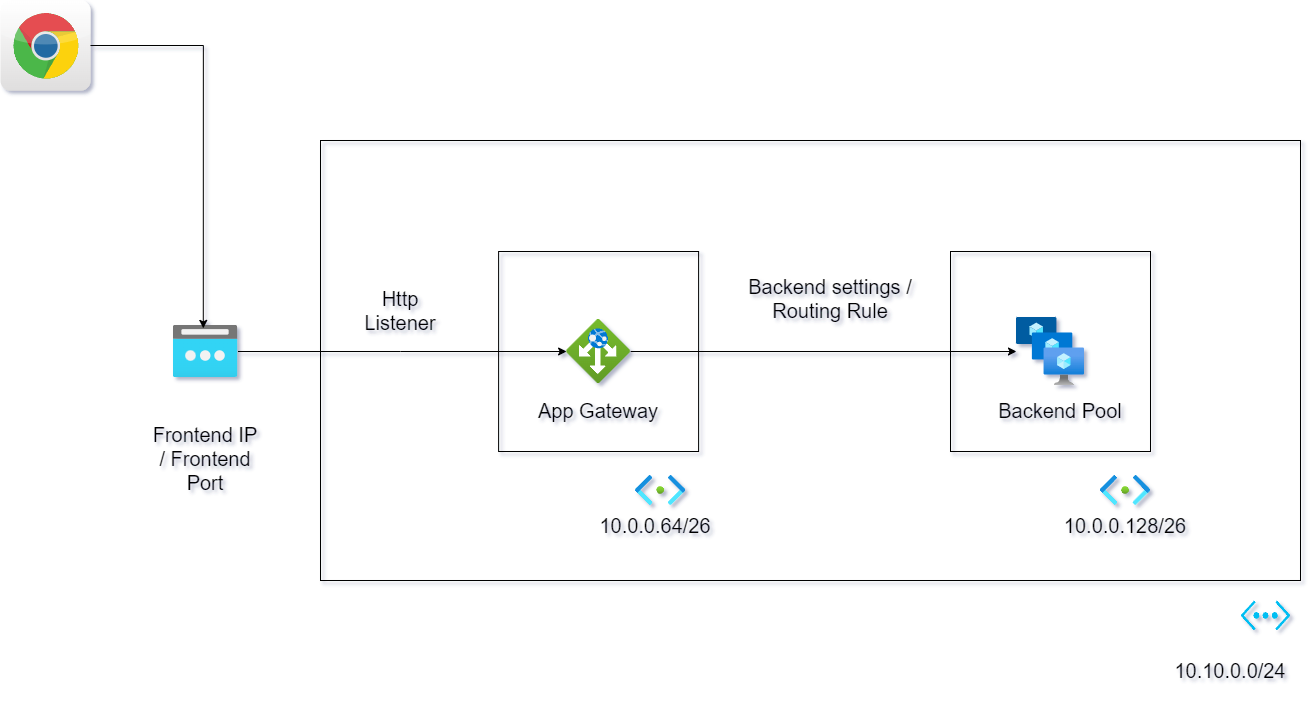
Windows and Linux backend servers under Azure Application gateway, provisioned using Terraform. Ansible is used to manage backend servers. DNS records are created using Cloudflare Terraform provider.
-
Frontend IP Configuration — Defines the private or public IP address that receives requests to the application gateway.
-
Frontend Port — Defines a port that accepts incoming requests to the application gateway.
-
Backend Pool — A list of IP addresses or FQDNs where traffic is forwarded.
-
HTTP Settings — Defines how the application gateway sends incoming traffic to backend servers by setting up a protocol, backend port, and timeout interval.
-
HTTP Listener — Binds the Frontend IP Configuration, Frontend Port, and protocol together to listen for incoming requests.
-
SSL Certificate — Used in HTTPS listeners to secure communication between the gateway and clients by enabling traffic encryption.
-
Routing Rules — Binds HTTP Listener, Backend Pool, and HTTP Settings to define how traffic is routed to backend servers.
-
Health Probe — Ensures that traffic is delivered only to healthy backend servers.
-
Gateway IP Configuration — Binds an application gateway to a specific subnet, ensuring proper internal communication.
- Deploy virtual network
- Deploy application gateway subnet
- Deploy application gateway public IP
- Associate gateway with subnet using
gateway_ip_configurationblock - Define app gateway frontend ports (80, 443) by using
frontend_portblock - Associate app gateway with public IP using
frontend_ip_configurationblock - Define backend pools with app services FQDNs by using
backend_address_poolblock - Define the way gateway communicates with backend via
http_settingsblock - Add http and https listeners to the app gateway using
http_listenerblock - Define routing rules to handle requests based on headers CN
- Create a Cloudflare DNS record for the app gateway public IP and test connection
- https://github.com/kolosovpetro/packer-azure-windows-image
- https://github.com/kolosovpetro/azure-windows-vm-terraform
- Control node (SSH key authentication)
- DB server (Password authentication -> then copy id to be executed)
- Web server (Password authentication -> then copy id to be executed)
- Windows DB server (RDP)
- Windows Web server (RDP)
- http://ansible-control-node.razumovsky.me
- http://ansible-dbserver.razumovsky.me
- http://ansible-webserver.razumovsky.me
- http://ansible-win-dbserver.razumovsky.me
- http://ansible-win-webserver.razumovsky.me
DEV
QA
From control node execute:
- Update
known_hostsfile by removing the old entries (if necessary) - ssh [email protected]
- ssh-keygen
- ssh-copy-id -i ~/.ssh/id_rsa [email protected]
- ssh-copy-id -i ~/.ssh/id_rsa [email protected]
- Copy SSH key and configure permissions
scp "$env:USER_DIRECTORY/.ssh/id_rsa" [email protected]:~/.sshssh [email protected] "chmod 600 ~/.ssh/id_rsa"ssh [email protected]
- Validate Python installation
git clone [email protected]:kolosovpetro/ansible-control-node.gitcd ansible-control-node- Run
install_python.sh
- Install Ansible
- Run
install_ansible.sh
- Run
- Copy Ansible global configuration file
ansible.cfgsudo cp ansible.cfg /etc/ansible/ansible.cfgscp ansible.cfg [email protected]:~/ansible.cfgssh [email protected] "sudo cp ~/ansible.cfg /etc/ansible/ansible.cfg"
- Copy Ansible inventory file
inventory/inventory.yamlsudo cp inventory/inventory.ini /etc/ansible/inventory.iniscp "inventory/inventory.ini" [email protected]:~/inventory.inissh [email protected] "sudo cp ~/inventory.ini /etc/ansible/inventory.ini"
- Update inventory file
inventory/inventory.yamlif necessary - Check connection to Linux managed nodes
ansible-playbook ping.yml
- Windows nodes require additional configuration
- Login to your Windows machines via RDP
- Open PowerShell as Administrator
- Copy script contents from
Configure-Ansible-Host.ps1to the terminal - Check connection to Windows managed nodes
ansible windows_servers -m win_ping
- ssh [email protected]
- ssh [email protected]
- ssh [email protected]
- https://docs.ansible.com/ansible/latest/os_guide/windows_winrm.html
- https://docs.ansible.com/ansible/latest/os_guide/windows_setup.html
- https://github.com/AlbanAndrieu/ansible-windows/blob/master/files/ConfigureRemotingForAnsible.ps1
- Set-ExecutionPolicy -ExecutionPolicy Bypass
- pip install "pywinrm>=0.3.0"
- Application gateway quizlet: https://quizlet.com/pl/975398961/azure-application-gateway-flash-cards/