This is an updated version of the Binwalk firmware analysis tool. It has been re-written in Rust, and is currently in the beta testing phase.
While the usage and output is similar to that of previous Binwalk releases, this version has several notable improvements:
While Binwalk still fundamentally relies on identifying files and data based on their magic signatures, each signature has an associated file parser which is repsonsible for parsing the expected file format and validating the data for correctness.
Signatures that are deemed to be valid have an associated confidence level, indicating how confident the file parser is in the accuracy of the reported result.
This results in fewer false positives, more reliable file extraction, and more detailed analysis results.
Rust is inherently faster than Python; this, combined with efficient pattern matching and multi-threaded recursive extraction makes analysis and extraction much faster than previous Binwalk releases.
Analysis and extraction results can be saved in JSON format, making Binwalk results easily ingestible by other tools.
A fork of the old Binwalk repository is currently maintained by OSPG.
Binwalk is only supported on 64-bit Linux systems, and only tested on DUbuntu Linux. It is recommended that you run Binwalk on a Ubuntu-based system.
Tip
The easiest way to get up and running quickly is to use the included Dockerfile to build a docker image.
To build a Binwalk docker image with all dependencies included:
sudo apt install git docker.io
git clone https://github.com/ReFirmLabs/binwalk.git
cd binwalk
sudo docker build -t binwalk .
That's it!
To analyze and extract a local file /tmp/firmware.bin using the Binwalk docker image:
sudo docker run -t -v /tmp:/home/appuser binwalk -Me firmware.bin
The extracted files will be located in your /tmp/extractions directory.
To compile Binwalk, you must first have the Rust compiler installed.
Download the Binwalk git repository:
sudo apt install git
git clone https://github.com/ReFirmLabs/binwalk.git
Install build/runtime dependencies.
Note
Binwalk relies on several external utilities to perform extraction at runtime. These are not required, but automated extraction of certain file types will fail if they are not installed.
To install all build and runtime dependencies (recommended):
sudo ./binwalk/dependencies/ubuntu.sh
OR, to install only the required build dependencies:
sudo apt install build-essential libfontconfig1-dev liblzma-dev
Build Binwalk:
cd binwalk
cargo build --release
./target/release/binwalk --help
The Binwalk binary will be located at the target/release/binwalk path, as shown above.
You may copy it to, and run it from, any location on your system that you prefer.
List all signatures and required extraction utilities:
binwalk --list
Scan a file's contents:
binwalk file_name.bin
Exclude specific signatures from a scan:
binwalk --exclude=jpeg,png,pdf file_name.bin
Only serch for specific signatures during a scan:
binwalk --include=jpeg,png,pdf file_name.bin
Scan a file and extract its contents (default output directory is extractions):
binwalk -e file_name.bin
Recursively scan and extract a file's contents:
binwalk -Me file_name.bin
Generate an entropy graph of the specified file (a PNG image will be saved to the current working directory):
binwalk -E file_name.bin
Save signature or entropy analysis results to a JSON file:
binwalk --log=results.json file_name.bin
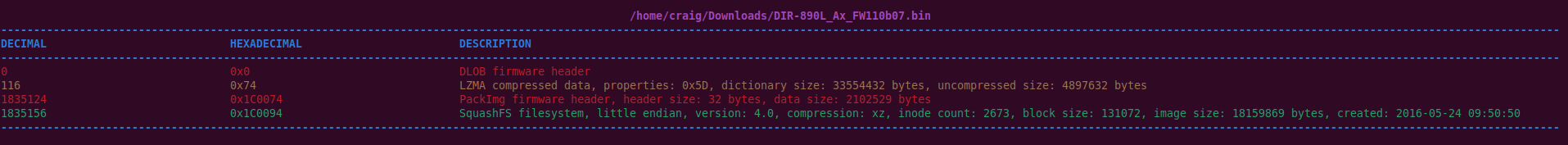
For each identified file type, Binwalk displays the file offset in both decimal and hexadecimal, along with a brief description.
Output is color-coded to indicate the confidence of the reported results:
There is no strict definition for the confidence level of each result, but they can generally be interpreted as:
Tip
High confidence; both file metadata and at least some portions of the file data were checked for accuracy
Warning
Medium confidence; a reasonable amount of validation/sanity-checking was performed on the file metadata
Caution
Low confidence; the "magic bytes" for the reported file type were identified, but little-to-no additional validation was performed
Note
During recursive extraction only "interesting" results will be displayed; use the --verbose command line option to display all results.
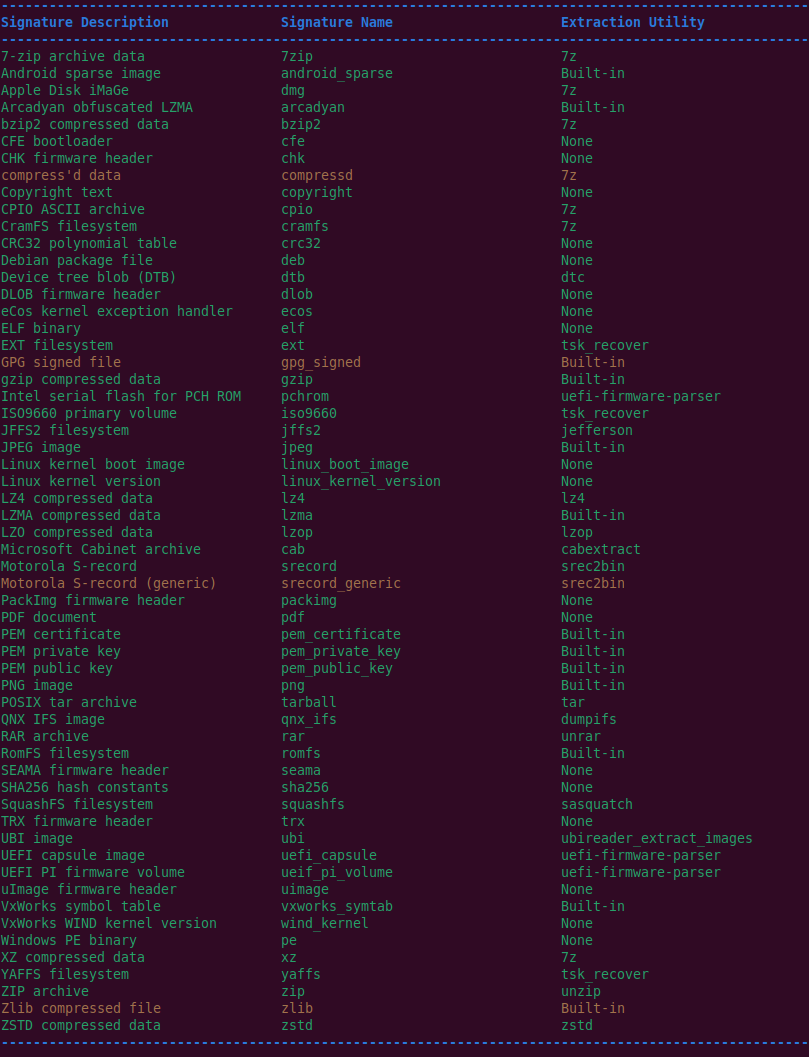
All supported file signatures and their corresponding extraction utility (if any) can be displayed with the --list command line option:
Each signature is color-coded to indicate:
Tip
Signature is fully supported
Warning
Signature is prone to false positives and will only be matched at the beginning of a file
Note
The values displayed in the Signature Name column can be used with the --include and --exclude signature filter arguments.
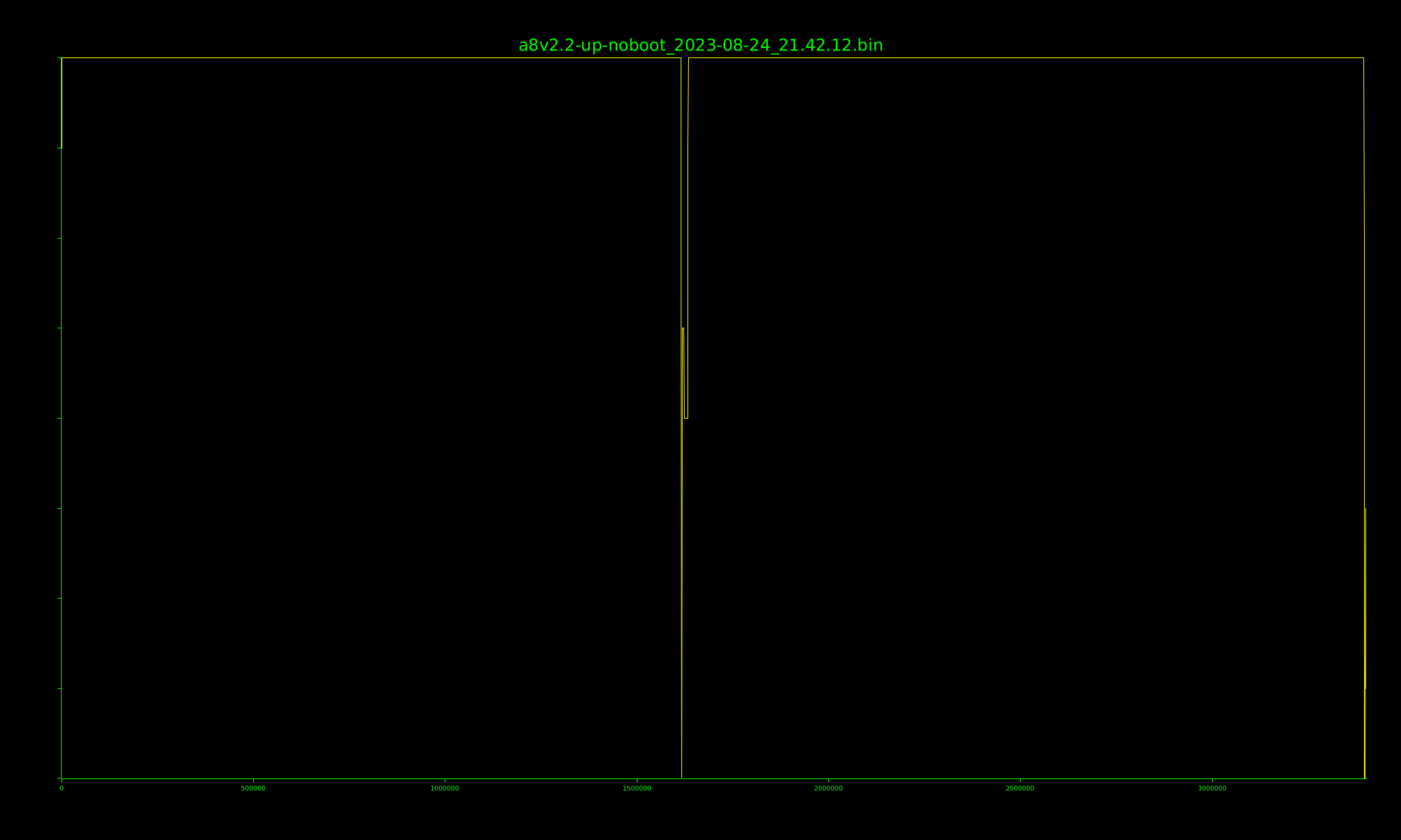
Entropy graphs (--entropy) display a plot of how random the contents of a file are, with the
level of randomness displayed on the y axis and the file offset displayed on the x axis:
Randomness is calculated on a unit-less scale of 0 (not random at all) to 8 (very random). Since compressed and encrypted data is, by nature, very random,
this is useful for identifying sections of a file that have been compressed or encrypted.
The JSON logs (--log) include more detailed signature and extraction information than is reported on the command line.
If an entropy scan was requested (--entropy), the JSON data will contain the raw entropy data for the specified file.
Errors and debug logs are handled by the Rust env_logger, which allows users to control log levels
via the RUST_LOG environment variable:
RUST_LOG=off binwalk -Me file_name.bin
RUST_LOG=info binwalk -Me file_name.bin
RUST_LOG=debug binwalk -Me file_name.bin
All errors and debug information are printed to stderr.
Currently binwalk is primarily a command line utility, but a Rust library is available.
Warning
Binwalk can be very resource intensive. By default it will use all available CPU cores, and reads files into memory in their entirety.
Tip
Use the --threads argument to limit the number of concurrent threads.