This is a section of the Javascript Blockchain/Smart Contract FreeCodeCamp Course. This part of the course is to help users understand basic security and some fundamentals of auditing.
This repo has a few contracts with big flaws, see if you can see them, and see if the tools help you find them!
⌨️ (31:28:32) Lesson 18: Security & Auditing
- Hardhat Security
- What is an Audit?
- Help your auditors!
- Process
- Resources
- Getting Started
- Usage
- Linting
- Formatting
- Thank you!
This project is apart of the Hardhat FreeCodeCamp video.
An audit is a security focused code review for looking for issues with your code.
When writing good code, you 100% need to follow these before sending you code to an audit.
Tweet from legendary security expert Tincho
- Add comments
- This will help your auditors understand what you're doing.
- Use natspec
- Document your functions. DOCUMENT YOUR FUNCTIONS.
- Test
- If you don't have tests, and test coverage of all your functions and lines of code, you shouldn't go to audit. If your tests don't pass, don't go to audit.
- Be ready to talk to your auditors
- The more communitcation, the better.
- Be prepared to give them plenty of time.
- They literlly pour themselves over your code.
"At this time, there are 0 good auditors that can get you an audit in under a week. If an auditor says they can do it in that time frame, they are either doing you a favor or they are shit. " - Patrick Collins, March 4th, 2022
An auditors process looks like this:
- Run tests
- Read specs/docs
- Run fast tools (like slither, linters, static analysis, etc)
- Manual Analysis
- Run slow tools (like echidna, manticore, symbolic execution, MythX)
- Discuss (and repeat steps as needed)
- Write report
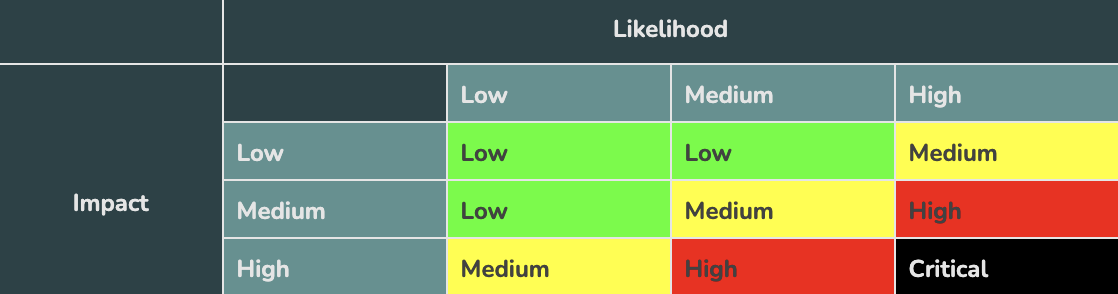
Typically, you organize reports in a chart that looks like this:
These are some of the best places to learn even MORE about security:
PRs welcome to improve the list.
- Slither
- Static analysis from Trail of Bits.
- Echidna
- Fuzzing from Trail of Bits.
- Manticore
- Symbolic execution tool from Trail of Bits.
- MythX
- Paid service for smart contract security.
- Mythrill
- MythX free edition.
- ETH Security Toolbox
- Script to create docker containers configured with Trail of Bits security tools.
- ethersplay
- ETH Disassembler
- Consensys Security Tools
- A list of Consensys tools.
- Ethernaut (This is a must play!)
- Damn Vulnerable Defi (This is a must play!)
- rekt
- A blog that keeps up with all the "best" hacks in the industry.
- Trail of bits blog
- Learn from one of the best auditors in the space.
- Openzeppelin Blog
- Another blog of one of the best auditors in the space.
- Smart Contract Security Best Practices
- Consensys blog on security vulnerabilities. Also check out their tools.
- Chainlink X Certik Blog on Security
- I helped write this. 😊
- More attacks
- Git
- You'll know you did it right if you can run
git --versionand you see a response likegit version x.x.x
- You'll know you did it right if you can run
- Nodejs
- You'll know you've installed nodejs right if you can run:
node --versionand get an ouput like:vx.x.x
- You'll know you've installed nodejs right if you can run:
- Yarn instead of
npm- You'll know you've installed yarn right if you can run:
yarn --versionand get an output like:x.x.x- You might need to install it with npm
- You'll know you've installed yarn right if you can run:
- Docker
- You'll know you've installed docker right if you can run:
docker --versionand get an ouput likeDocker version xx.xx.xx, build xxxxx
git clone https://github.com/PatrickAlphaC/hardhat-security-fcc
cd hardhat-security-fcc
yarn
Then, go right into usage
Sorry! Feel free to make a PR if you'd like to see typescript here.
If you can't or don't want to run and install locally, you can work with this repo in Gitpod. If you do this, you can skip the clone this repo part.
Open the docker shell:
yarn toolbox
Then, run:
slither /src/contracts/ --solc-remaps @openzeppelin=/src/node_modules/@openzeppelin --exclude naming-convention,external-function,low-level-calls
To exit:
exit
Open the docker shell:
yarn toolbox
Then, run this:
echidna-test /src/contracts/test/fuzzing/VaultFuzzTest.sol --contract VaultFuzzTest --config /src/contracts/test/fuzzing/config.yaml
To exit:
exit
To check linting / code formatting:
yarn lint
or, to fix:
yarn lint:fix
yarn format
If you appreciated this, feel free to follow me or donate!
ETH/Polygon/Avalanche/etc Address: 0x9680201d9c93d65a3603d2088d125e955c73BD65