Latest Version: beta - Release Date:
This project is an integration between Microsoft Defender for Endpoint and VMRay products: Analyzer, FinalVerdict and Totalinsight. The connector will collect alerts and related evidences, and query or submit these samples into VMRay Sandbox. It accelerates the triage of alerts by adding comments to the alert in MS Defender Console with the analysis of the sample. It also retrieves IOC values from VMRay and submits them into Microsoft Defender for Endpoint.
- The connector is built using Azure logic app, Azure functions app and Azure Storage.
- Azure Logic app
SubmitDefenderAlertsToVMRaymonitors the alerts from MS Defender as soon any AV/EDR alert are generated. If any AV/EDR alert is found, it will send the alert details to the Azure function appVMRayDefender. - Azure function app
VMRayDefenderchecks if the alert contains a file and checks if the file hash has already been analyzed by VMRay. - If the hash was already analysed, the system checks if user configure to reanalyse the hash in configuration step, if yes it resubmits that to VMRay to reanalyse, if not it skips re-examining it.
- Azure function app
VMRayDefenderrequests the file from Microsoft Defender by starting a live response session. - Microsoft Defender starts a live response session that run PowerShell code on the endpoint. The power shell moves the files out of quarantine to a temporary folder before sending to Azure storage(vmray-defender-quarantine-files) container.
- Azure function app
VMRayDefendermonitors the Azure storage(vmray-defender-quarantine-files) container and submits the quarantine file to VMRay. - Azure function app
VMRayDefenderwill wait till the submission is completed and When the VMRay analysis is done VMRay results are sent back to the Azure function appVMRayDefender. - The Azure function app
VMRayDefenderpost the results as a note within the relevant defender alert. - If configured to send IOCs, the Azure function app
VMRayDefenderprovides the IOCs as the indicators to Microsoft Defender that may use them for automatically alerting or blocking. - Once the Azure function app
VMRayDefendercompletes its process, it generates a JSON file named after the Defender Alert ID and uploads it to the Azure Storage Container: vmray-defender-functionapp-status. This JSON file contains all the details of the process. - The Azure Logic App
SendEmailNotificationmonitors the vmray-defender-functionapp-status container for new files. When a new file is detected, it sends an email notification to the configured recipient in logic app.
- Azure Logic app
- Microsoft Defender for Endpoint.
- VMRay Analyzer, VMRay FinalVerdict, VMRay TotalInsight.
- Microsoft Azure
- Azure functions with Flex Consumption plan. Reference: https://learn.microsoft.com/en-us/azure/azure-functions/flex-consumption-plan
- Azure Logic App with Cunsumption plan. Reference: https://learn.microsoft.com/en-us/azure/logic-apps/logic-apps-pricing#consumption-multitenant
- Azure storage with Standard general-purpose v2.
-
In VMRay Console, you must create a Connector API key.Create it by following the steps below:
- Create a user dedicated for this API key (to avoid that the API key is deleted if an employee leaves)
- Create a role that allows to "View shared submission, analysis and sample" and "Submit sample, manage own jobs, reanalyse old analyses and regenerate analysis reports".
- Assign this role to the created user
- Login as this user and create an API key by opening Settings > Analysis > API Keys.
- Please save the keys, which will be used in confiring the Azure Function.
- Open https://portal.azure.com/ and search
Microsoft Entra IDservice.
- Click
Add->App registration.
- Enter the name of application and select supported account types and click on
Register.
- In the application overview you can see
Application Name,Application IDandTenant ID.
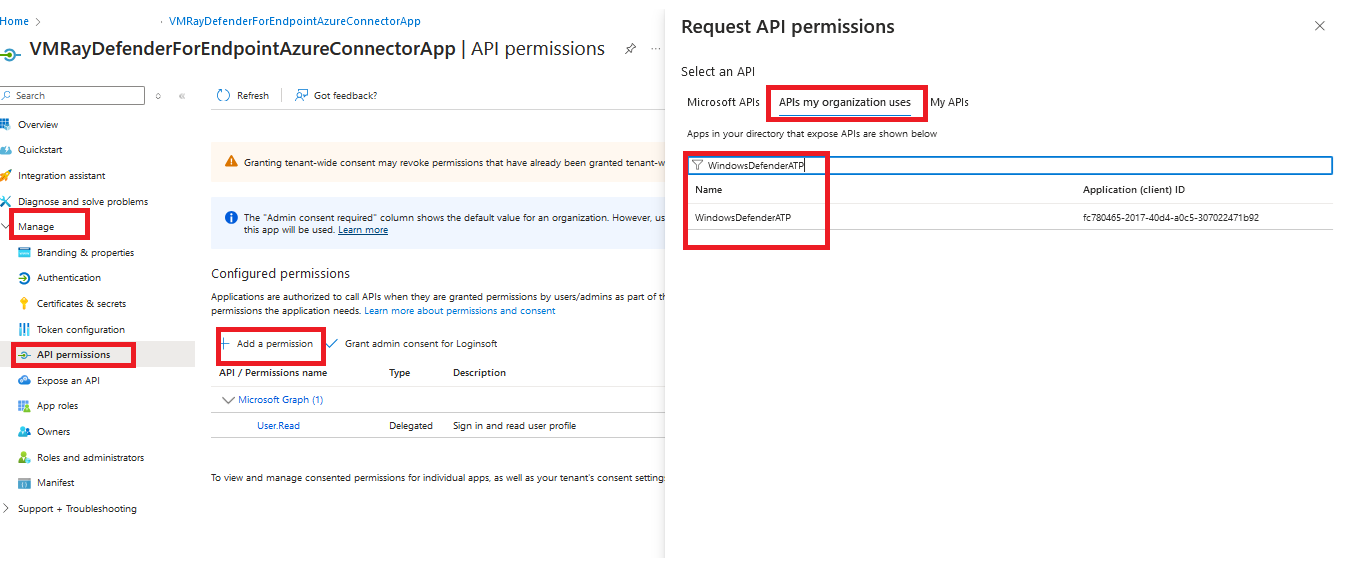
- After creating the application, we need to set API permissions for connector. For this purpose,
- Click
Manage->API permissionstab - Click
Add a permissionbutton - Select
APIs my organization uses - Search
WindowsDefenderATPand click the search result
- Click
- On the next page select
Application Permissionsand check permissions according to the table below. And clickAdd permissionsbutton below.
| Category | Permission Name | Description |
|---|---|---|
| Alert | Alert.Read.All | Needed to retrieve alerts and related evidence |
| Alert | Alert.ReadWrite.All | Needed to enrich alerts with sample information |
| Machine | Machine.LiveResponse | Needed to gather evidences from machines |
| Machine | Machine.Read.All | Needed to retrieve information about machines |
| Ti | Ti.Read.All | Needed to retrieve indicators |
| Ti | Ti.ReadWrite | Needed to retrieve and submit indicators (application specific) |
| Ti | Ti.ReadWrite.All | Needed to retrieve and submit indicators (general) |
| Library | Library.Manage | Needed to upload custom ps1 script for retrieving av related evidences |
- After setting only the necessary permisions, click the
Grant admin consent for ...button to approve permissions.
- We need secrets to access programmatically. For creating secrets
- Click
Manage->Certificates & secretstab - Click
Client secretstab - Click
New client secretbutton - Enter description and set expiration date for secret
- Click
- Use Secret
ValueandSecret IDto configure connector.
Reference
- Open https://security.microsoft.com
- Open
Settingspage andEndpointstab. - Open
Advanced features. - Activate
Live Response,Live Response for ServersandLive Response unsigned script executionoptions.
- Open https://portal.azure.com/ and search
Deploy a custom templateservice.
- On the next page select
Build your own templatein the editor.
- Copy
azuredeploy.jsoncontents from theFunctionAppfolder and save it.
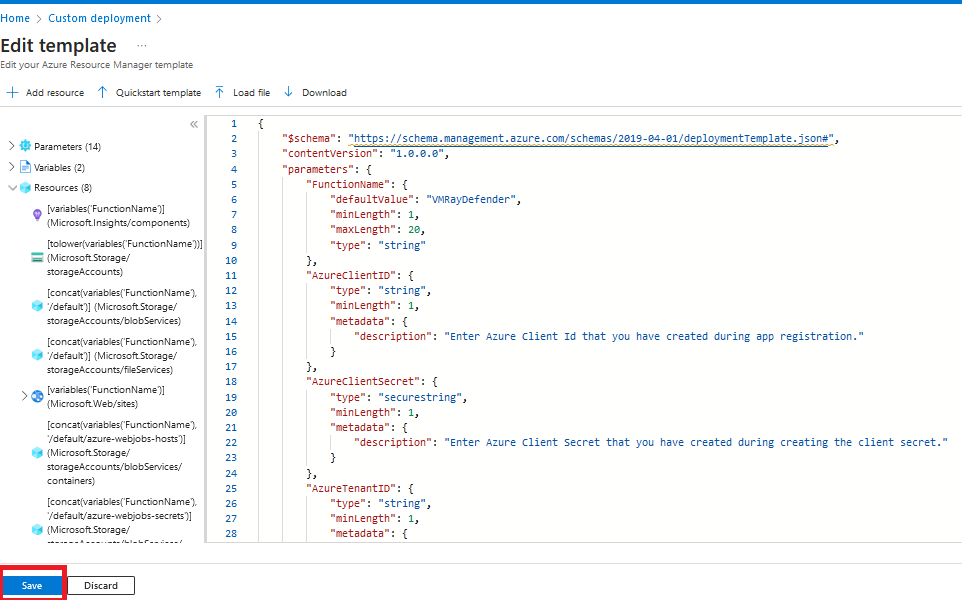
- On the next page, please provide the values accordingly.
| Fields | Description |
|---|---|
| Subscription | Select the appropriate Azure Subscription |
| Resource Group | Select the appropriate Resource Group |
| Region | Based on Resource Group this will be uto populated |
| Function Name | Please provide a function name if needed to change the default value |
| Azure Client ID | Enter the Azure Client ID created in the App Registration Step |
| Azure Client Secret | Enter the Azure Client Secret created in the App Registration Step |
| Azure Tenant ID | Enter the Azure Tenant ID of the App Registration |
| Azure Storage Connection String | Please leave this empty |
| Azure Storage Saas Token | Please leave this empty |
| App Insights Workspace Resource ID | Go to Log Analytics workspace -> Settings -> Properties, Copy Resource ID and paste here |
| Vmray Base URL | VMRay Base URL |
| Vmray API Key | VMRay API Key |
| Vmray Resubmit | If true, the files will be resubmitted to VMRay analyser, even if the file hash was found in VMRay |
| Vmray API Retry Timeout | Provide maximum time to wait in minutes, when VMRay API is not responding |
| Vmray API Max Retry | Provide number of retries, when VMRay API is not responding |
| Vmray Analysis Job Timeout | Provide maximum time to wait in minutes, when VMRay Job submissions is not responding |
| Defender API Retry Timeout | Provide maximum time to wait in minutes, when Microsoft Defender API is not responding. |
| Defender API Max Retry | Provide number of retries, when Microsoft Defender API is not responding |
| Machine Availability Timeout | Provide maximum time to wait in minutes, when the machine is not responding |
| Machine Availability Retry | Provide number of retries, when machine is not responding |
| Create Indicators In Defender | If true, Indicators will be created in Microsoft Defender |
| Vmray Sample Verdict | Based on the selection, Indicators will be created in Microsoft Defender |
| Defender Indicator Action | The action that is taken if the indicator is discovered in the organization |
| Defender Indicator Alert | True if alert generation is required, False if this indicator shouldn't generate an alert |
- Once you provide the above values, please click on
Review + createbutton.
- Download the zip package from the
FunctionAppfolder. - Open https://portal.azure.com/ and search
Storage accountsservice.
- Open the storage account, the name starts with
vmraystorage. - Go to
Storage Browser->Blob Containers, click on container, the name starts withvmraycontainer. - Click on
Switch to Access key.
- Upload the downloaded zip package to the container.
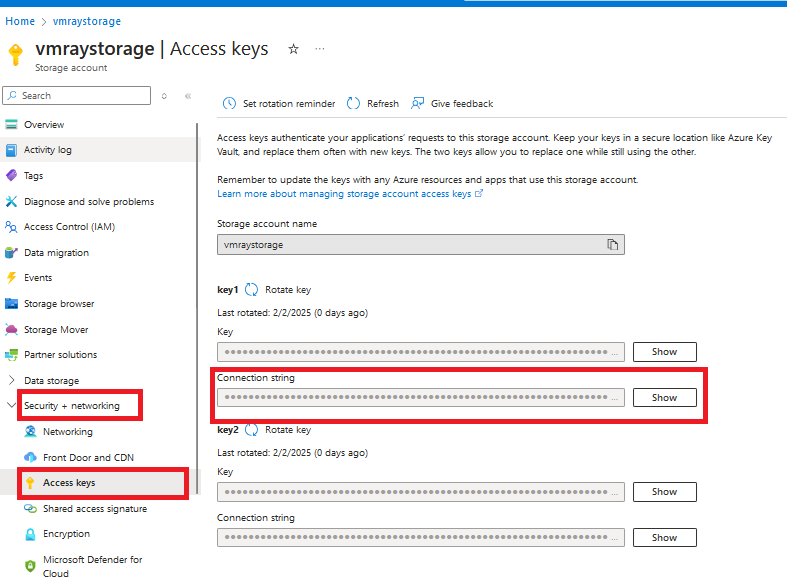
- Go to
Security + networking->Access keys, CopyConnection stringand save it temporarily for next steps.
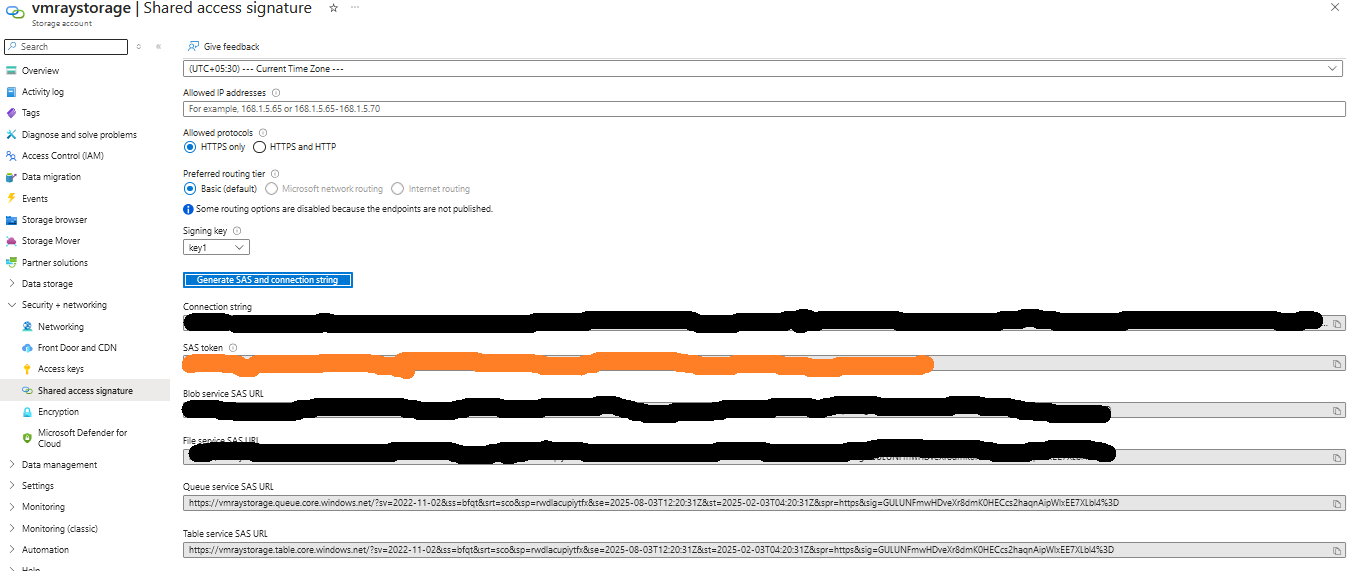
- Go to
Security + networking->Shared access signature, check all the options underAllowed resource types, provideEnd(expiration time, preferred 06 months), click onGenerate SAS and connection string.
- Copy
SAS tokenand save it temporarily for next steps.
- Open https://portal.azure.com/ and search
Function Appservice.
- Open the VMRay FunctionApp name starts with
vmraydefender. - Go to
Settings->Environment variables, double-clickAzureStorageConnectionStringand provide the connection string value copied in the previous step and click onsave. - Go to
Settings->Environment variables, double-clickAzureStorageSaasTokenand provide the Saas token value copied in the previous step and click onsave. - Click on
Apply->Confirmbuttons.
- Go to
Overview-> click onRestart.
- Open https://portal.azure.com/ and search
Deploy a custom templateservice.
- On the next page select
Build your own templatein the editor.
-
Copy
azuredeploy1.jsoncontents from theLogicAppfolder and save it. -
On the next page, provide the appropriate
SubscriptionandResource groupand click onReview & create.Note: When deploying the function app if you chose a different name, please kindly provide the same name here as well.
- Once the deployment is complete, go to newly deployed logic app, click on edit. The logic app will open in a designer mode.
- Click on the
WDATP Trigger, click onAdd new.
- On the next page, choose
AuthenticationasService prinicipal, and provide appropriate values.
- Click on
Alerts - Get single Alertaction, click onCheange connectionand select the connection created above.
-
Save the Logic App.
-
Open https://portal.azure.com/ and search
Deploy a custom templateservice.
- On the next page select
Build your own templatein the editor.
- Copy
azuredeploy2.jsoncontents from theLogicAppfolder and save it. - On the next page, provide the appropriate
SubscriptionandResource groupand click onReview & create.
- Once the deployment is complete, go to newly deployed logic app, click on edit. The logic app will open in a designer mode.
- Click on the
Azure Blob Trigger, click onChange connectionand click onAdd newon the following page.
- Provide appropriate values and click on
Create new.
- Click on
folder iconon theContainer box.
- Select folder named
vmray-defender-functionapp-status
- Click on
Get blob contentaction, click onChange connection.
- Select the connection created in the above step.
-
Do the same
Delete blobaction, click onChange connectionand select the connection created in the above step. -
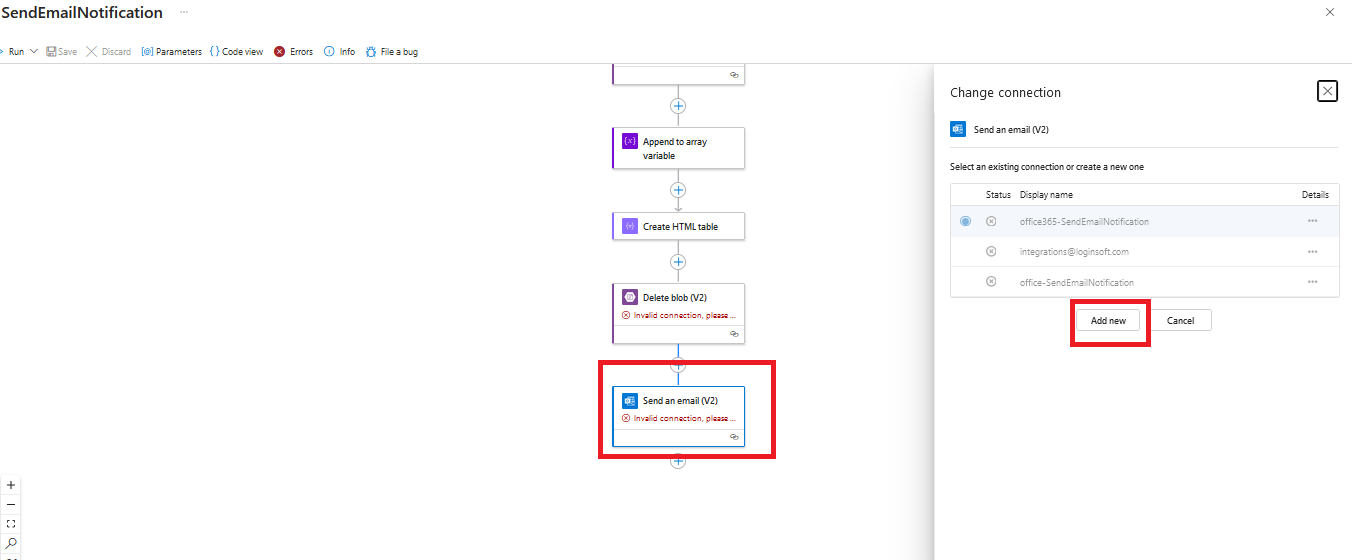
Click on
Send an Email(V2)action, click onChange connectionand click onAdd new, provide appropriate connection.
- Save the Logic App.
- To debug and check logs after receiving an email, follow these steps:
- Logic App
SubmitDefenderAlertsToVMRayruns will fail. This is a expected behaviour. - In Logic App Consumption Plan, each API call runs for a maximum of 2 minutes before retrying the process. This is the default behavior for consumption-based Logic Apps. Since this Logic App is calling the
VMRayDefenderfunction app and the process might take more than 2m to finish, the Logic App will fail. But theVMRayDefenderfunction app will do all the work behind and let the customers know once the analyisis is completed
Why 2 playbooks Approach
- To overcome the 2 minutes isssue, we need to deploy the Logic apps with the Standard Plan, it would cost approximately $175 per month.To avoid this extra cost, we created an additional Logic App that monitors whether the previous Logic App succeeded or failed.
- It then notifies the customer via email, allowing them to stay in sync with the process.