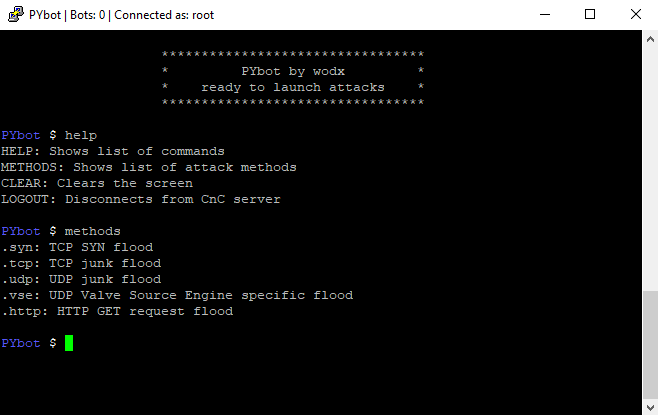
PYbot is a basic open source denial of service botnet system written in Python 3, consists of a connect and control server and a bot malware script.
| Command | Description |
|---|---|
| help, ? | Shows list of commands |
| methods | Shows list of attack methods |
| clear, cls | Clears the console window screen |
| exit, logout | Disconnects from the C&C server |
| .syn <host> <port> <duration> | Starts a TCP SYN flood attack |
| .tcp <host> <port> <duration> <size> | Starts a TCP junk flood attack |
| .udp <host> <port> <duration> <size> | Starts a UDP junk flood attack |
| .vse <host> <port> <duration> | Starts a VSE query flood attack |
| .http <host> <duration> | Starts a HTTP GET request flood attack |
- TCP Flood
- Floods target with trashed TCP data packets.
- TCP SYN Flood
- Floods target with SYNchronize TCP packets.
- Read more about the attack method here.
- UDP Flood
- Floods target with trashed UDP data packets.
- Read more about the attack method here.
- VSE Flood
- Floods target with VSE server queries.
- Designed to take down Source based game servers by sending legitimate traffic to the target server.
- HTTP GET Request Flood
- Floods target with HTTP GET requests.
- Read more about the attack method here.
- Install Git and Python 3 on your server.
- Clone the PYbot Github repository to your server via Git:
$ git clone https://github.com/WodxTV/PYbot.git. - Change the host address and C&C port in the configuration section in bot.py to your server address and C&C port.
- Start the CnC server by executing the command:
$ python cnc.py <cnc port>. - Add accounts in logins.txt using the format:
username:password. - Connect to the server through PuTTY on a raw socket connection.
Compiling the malware and installing it on vulnerable devices won't be told as it's highly illegal to get remote access to devices without permission. Use of this project for illegal activities is at own risk! I'm not responsible for any of your taken actions!